The Last Mile for Zero Trust and SASE
Zero Trust and SASE frameworks improve security but can leave a hole when they only protect the “pipe” but not the endpoint itself. Even when zero trust policies limit employee data access to the minimum scope necessary, the PC itself remains the vulnerable last mile.
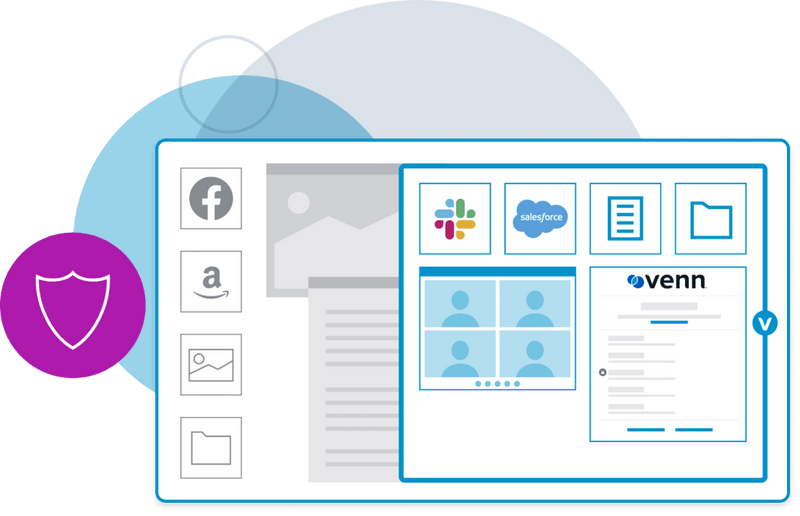
Venn isolates and protects business applications and data on a worker’s computer offering the following benefits:
Secure Sensitive Client Assets
Venn allows companies to maintain full control over sensitive company data
including what data can be accessed and how data isstored or shared
without having to manage the whole PC.
Control
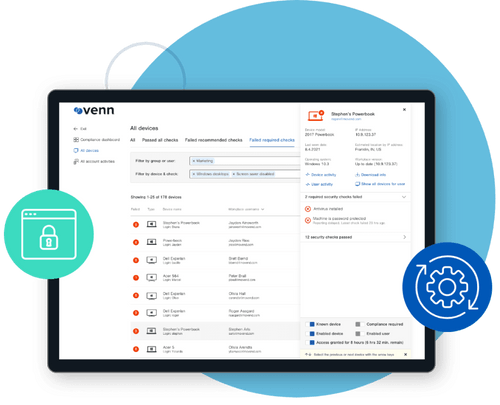
Enables robust administrative control over work applications and data including policies for network access, peripheral use, copy-paste and more.
Turnkey HIPAA
& PCI compliance
Because Venn is both HIPAA and PCI compliant, customers gain a much faster and easier to execute compliance program.
Save Money
VDI is a popular choice for securing contractor and temporary worker PCs. Venn is less costly, less complicated and preferred by users.
Onboard And Offboard More Quickly
Since there’s no need to manage or ship PCs, new contractors can be onboarded with a simple download to their personal PC. When workers leave, companies can instantly and remotely delete the Venn enclave without worrying if a computer will be returned.
