
Use Cases
Venn is the #1 VDI Alternative
Unlike VDI, Venn allows users to run applications locally within a Secure Enclave, where corporate policies are continuously enforced. No additional infrastructure or remote hosting necessary.
Give Users a Local Experience. No Lag. No Latency.
VDI was once built to secure remote work – but it’s now frustrating users, overwhelming IT, and inflating costs. Venn offers a VDI alternative with a fundamentally different approach. With Blue Border™, organizations can protect apps, data, and network access on unmanaged and BYOD computers – without hosting applications and data remotely. The result? Seamless security, a far better user experience, and dramatically lower overhead.
Embrace a Local, Latency-Free Approach
Unlike virtual desktops, Venn keeps users working locally on natively installed applications without latency – all while extending corporate firewall protection to business activity only.
Protect Business Data
With Venn, work lives in a company-controlled Secure Enclave that protects and isolates business activity from any personal use on the same computer. Prevent copy/paste, screen sharing, file downloads, and more.
Maintain Compliance Without the Complexity
Achieve compliance with rigorous industry standards and regulations – like SOC 2, HIPAA, FINRA, CMMC, and GDPR – without the administrative burden of managing and securing physical devices.

According to Gartner, maintaining a robust security posture in environments where user-owned, unmanaged devices access corporate applications and data requires a dedicated BYO-PC security initiative.
Gartner, Inc. “Hype Cycle for Endpoint Security, 2024” by Franz Hinner, Satarupa Patnaik, Eric Grenier, Nikul Patel and “Hype Cycle for I&O Digital Workplace Transformation, 2024″ by Autumn Stanish, Pankil Sheth

VDI Challenges for a Secure Remote Workforce
IT teams have historically used tools like VDI and DasS to secure company data on unmanaged or BYOD computers, but these are often expensive, latency-ridden, and complex to upkeep. There’s a better way.
Download our eBook to unlock best practices for securing remote work and overcoming VDI challenges.
Turnkey Compliance
Venn makes it easy to meet regulatory requirements with built-in, turnkey compliance for HIPAA, PCI, SEC, SOC 2, FINRA and more. Security and compliance controls are automatically enforced on any unmanaged device, so you can onboard contractors confidently without added overhead.

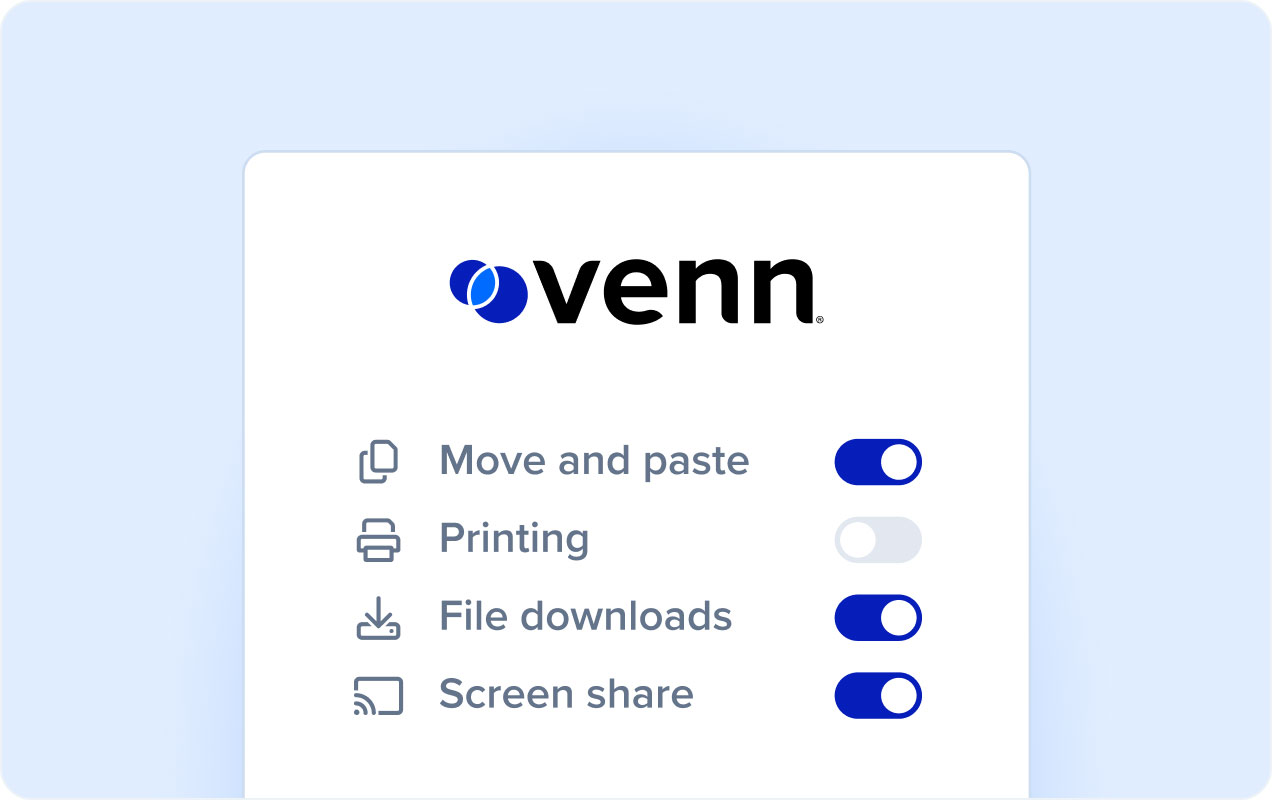
Robust Security Controls
Venn extends the power of the corporate firewall to any BYOD or unmanaged device. IT administrators gain granular security controls that improve data protection without compromising user privacy or productivity. Security policies are automatically enforced across all critical work applications and data, ensuring secure access within a company-defined perimeter.
Workforce Agility
Allowing contractors and consultants to onboard using BYOD computers enables faster time-to-productivity. IT teams eliminate the time, cost, and hassle of provisioning, managing, and shipping laptops – accelerating deployments and minimizing delays.
With Venn, you can… onboard and off-board users securely with ease
With Venn you can onboard and off-board users in minutes – without shipping laptops, configuring VDI, or taking control of personal devices.
With Venn, you can… reduce infrastructure costs
VDI is a popular choice for securing third party contractor and offshore worker devices. Venn is less costly, less complicated and preferred by users. Users can work on their own devices and IT teams save on the cost of VDI or having to lock down and ship PCs back and forth.
With Venn, you can… enable productivity and deliver enhanced user satisfaction
With Venn, workers don’t have to change the way they work. You can empower users to work on the device they prefer – boosting productivity and driving higher satisfaction without sacrificing control or security.
