Featured Resources
How to Create a BYOD-Friendly Data Loss Prevention Policy


March 13, 2025
Blog
How to Create a BYOD-Friendly Data Loss Prevention Policy
Creating and implementing a data loss prevention policy is a critical security measure for organizations today. But many DLP policies prioritize security at the cost of usability, which leads to employee frustration and, in turn, security workarounds–ultimately increasing the risk of data leaks and shadow IT. Achieving this balance is challenging, as implementing DLP policies […]
BYOD Security: Managing Third-Party Risk


February 18, 2025
Blog
BYOD Security: Managing Third-Party Risk
How a Call Center-Driven Healthcare Company is Tackling BYOD and Operational Efficiency


December 17, 2024
Blog
How a Call Center-Driven Healthcare Company is Tackling BYOD and Operational Efficiency
5 Myths About Remote Work Security: What Every IT Leader Should Know


June 12, 2024
Blog
5 Myths About Remote Work Security: What Every IT Leader Should Know
5 Risks of Unmanaged Devices and How to Mitigate Them


Knowledge Article
5 Risks of Unmanaged Devices and How to Mitigate Them
What Are Unmanaged Devices? Unmanaged devices are network-connected devices that lack active monitoring, management, or control by IT or security teams. They are often personal devices or third-party devices that employees or contractors use, which fall outside of the organization’s standard management and security policies. These devices can pose significant security risks due to lack […]
Mobile Application Management (MAM): Challenges and Best Practices


Knowledge Article
Mobile Application Management (MAM): Challenges and Best Practices
What Is Mobile Application Management (MAM)? Mobile Application Management (MAM) is a security framework focused on controlling and securing mobile applications within an organization. It allows IT administrators to manage and protect corporate data within apps on both company-owned and personal devices, without necessarily managing the entire device. MAM solutions handle app distribution, configuration, access […]
8-Step Process for Contractor Onboarding Success


Knowledge Article
8-Step Process for Contractor Onboarding Success
What Is Contractor Onboarding? Contractor onboarding is the process of integrating independent contractors or freelancers into a company, ensuring they understand their roles, responsibilities, and how to work effectively within the organization. This process differs from employee onboarding and focuses on legal compliance, clear communication, and efficient access to necessary tools and resources. This onboarding […]
Are Traditional Secure Remote Access Technologies Enough in 2025?


Knowledge Article
Are Traditional Secure Remote Access Technologies Enough in 2025?
Secure remote access refers to the methods and technologies that enable authorized users to connect to private networks or resources from remote locations while ensuring the confidentiality, integrity, and availability of data and systems. It’s crucial for maintaining business continuity, enabling remote work, and protecting sensitive information from unauthorized access. Key aspects of secure remote […]
Enforce DLP Policies for Installed Apps on Unmanaged or BYOD Computers
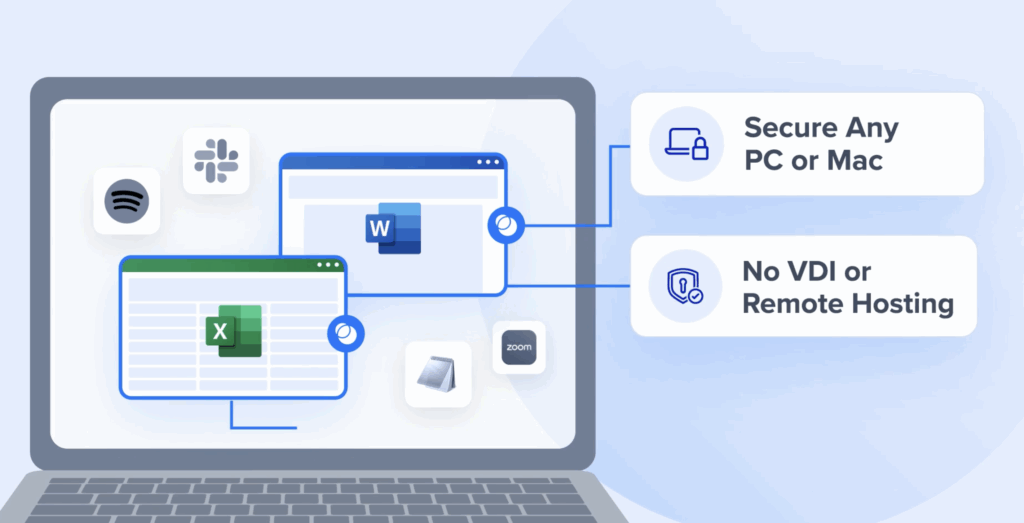

September 11, 2025
Product Demos
Enforce DLP Policies for Installed Apps on Unmanaged or BYOD Computers
Today’s workforces aren’t just full-time employees sitting in the office. Contractors, consultants, and remote employees are a critical part of many organizations, but giving them secure access to company data isn’t easy. Personal devices, unmanaged laptops, and diverse software environments create real security challenges, especially when sensitive data is involved. Traditional solutions, like virtual desktops […]
Understanding Citrix Pricing and 6 Ways to Reduce Your Costs


Knowledge Article
Understanding Citrix Pricing and 6 Ways to Reduce Your Costs
What Is the Citrix Platform? The Citrix platform is a suite of virtualization and cloud services designed to deliver secure desktops, applications, and data to any device. It combines desktop and application virtualization with centralized management tools, allowing organizations to provide consistent access for employees regardless of location. Its main components include: These solutions support […]
Citrix VDI (Citrix DaaS): Key Features, Pros/Cons, and Alternatives


Knowledge Article
Citrix VDI (Citrix DaaS): Key Features, Pros/Cons, and Alternatives
What Is Citrix VDI (Citrix DaaS)? The primary Citrix VDI offering is called Citrix DaaS (formerly Citrix Virtual Apps and Desktops). It is a technology that allows users to access desktop environments and applications from various devices through a centralized server. The Citrix DaaS solution allows users to use a desktop remotely, from PCs, tablets, […]
Azure Virtual Desktop Pricing in 2025 and 7 Ways to Cut Your Costs


Knowledge Article
Azure Virtual Desktop Pricing in 2025 and 7 Ways to Cut Your Costs
How Is Azure Virtual Desktop Priced? Azure Virtual Desktop pricing consists of two main components: user access rights and Azure infrastructure costs. User access rights are typically priced per user, while infrastructure costs are based on consumption, including virtual machines, storage, and networking. Organizations can also leverage existing eligible Windows or Microsoft 365 licenses to […]
Secure Work Files Stored Locally on any Unmanaged Laptop
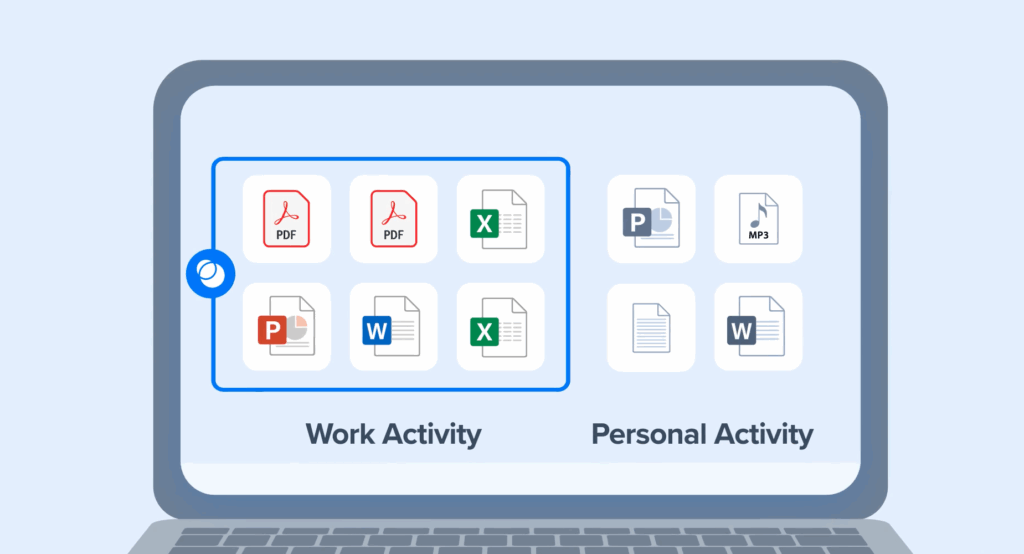

September 9, 2025
Product Demos
Secure Work Files Stored Locally on any Unmanaged Laptop
For organizations that rely on contractors, consultants, and remote employees, data exfiltration is one of the biggest security concerns. How can sensitive company files stay safe on devices that IT doesn’t fully control? With Venn, the answer is simple. Venn secures sensitive work files on unmanaged devices—without VDI or any form of virtualization or remote […]