Designed to Make Remote Work Fast, Secure and Seamless
Blue Border™ is the world’s first purpose-built technology that isolates and protects company data and applications locally on any PC or Mac.
Native app performance without the lag and latency of VDI
Legacy solutions like VDI are expensive, complex, and frustrating – plagued by high costs, poor performance, and a poor user experience. That is why Venn built something better.
Instead of hosting a virtual desktop, Blue Border™ creates a company-controlled Secure Enclave directly on the user’s PC or Mac – isolating business apps and data from anything personal on the same machine. Work apps continue to run locally, delivering 100% native performance with no lag or no latency. IT maintains control without managing the entire device or forcing users to work in a remotely hosted environment.


Download the Blue Border™ Product Brochure
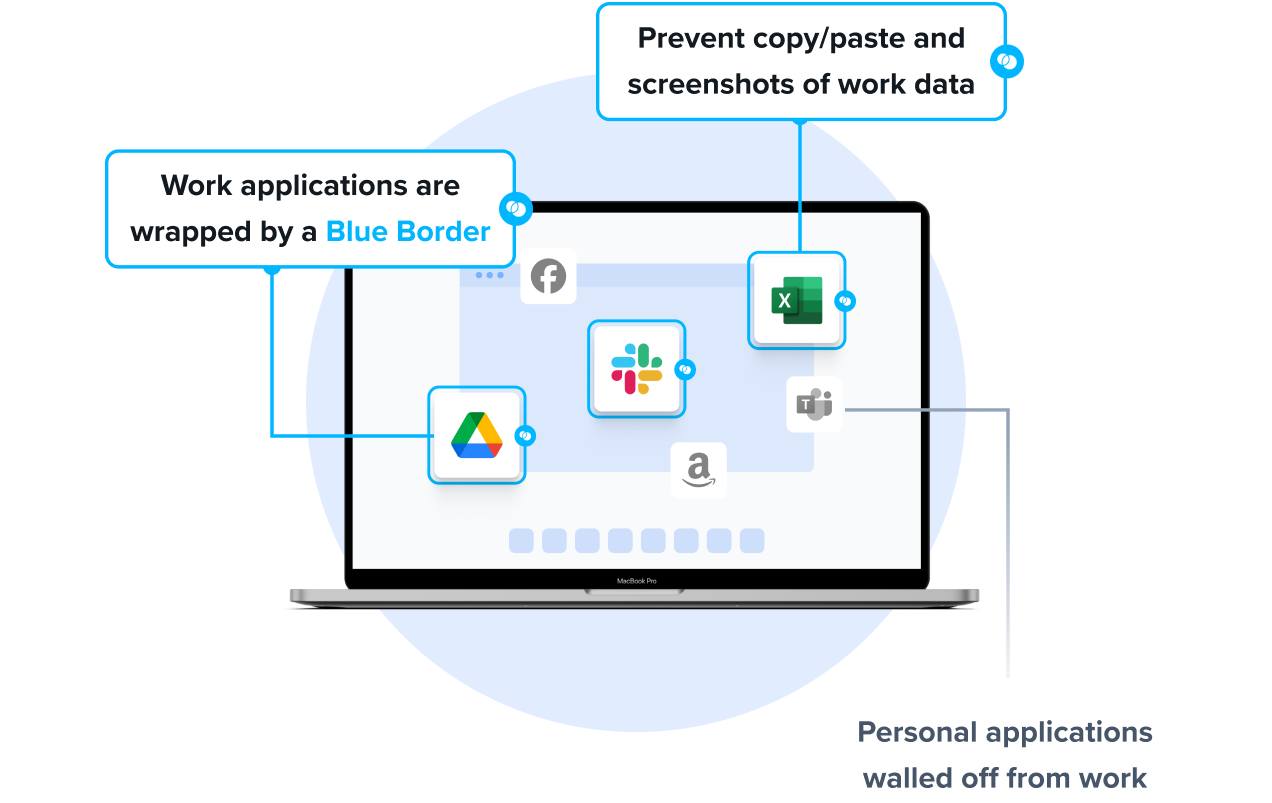
- Runs on Any Device – Isolates work apps and data locally on the endpoint, keeping corporate access fully governed without touching personal files or activity.
- Zero Lag, Zero Latency – Eliminates the performance complexity of VDI/DaaS by letting users work natively on their own machines.
- Compliance-Ready Controls – Apply precise policy, data protection, and audit enforcement controls that meets strict regulatory standards.
See how Blue Border™ replaces virtual desktops and legacy remote access tools
Control the Data, Not the Device
Blue Border™ provides the unique opportunity to control access to work applications and data – without managing the entire device or violating privacy.
While users are working inside Blue Border™, they are under corporate governance policies – but for all personal activity – they are not. For apps not running inside Blue Border™, all activity remains 100% private. Users can seamlessly toggle between work and personal activity on the same device.

Simplified Administration
Blue Border™ does not require any backend infrastructure, so companies can onboard and offboard remote employees and contractors in minutes. Centralized administration simplifies management, offering complete visibility and control over your BYOD workforce.
With Blue Border™, you can gain real-time insights into user activity, so you always know where, when, and from what device a user accessed an app or sensitive data.

100% Application Performance
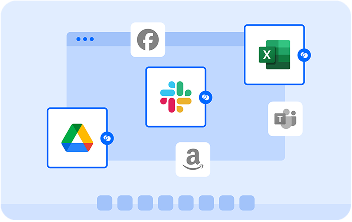
Unlike virtual desktops, users work with native installed applications running locally. Blue Border™ protects any installed work-sanctioned app including Chrome, Adobe, Slack, Microsoft Office applications, web conferencing tools like Zoom and Teams, VOIP applications, CAD and design tools, SAP, custom business applications and more.
Users can seamlessly toggle between application use within Blue Border™ and their personal use. This ensures a smooth and secure user experience.

Built-In User Privacy
Venn keeps personal activity completely separate and private. Anything outside of Blue Border™ can’t be seen, tracked, or monitored by the company or Venn.
Legacy solutions like VDI or traditional device management can be frustrating for users. These solutions often lead to risky workarounds because users feel their natural workflows are being interfered with and their privacy potentially invaded. Blue Border™ was built with user privacy in mind.
Purpose built with the highest standards
Venn was built to comply with the strictest cybersecurity standards including:
- SOC 2 Type II
- HIPAA
- SEC
- FINRA
- NAIC
- NYS DFS
- Mass 201 CMR 17.00
- CMMC
- PCI
How It Works
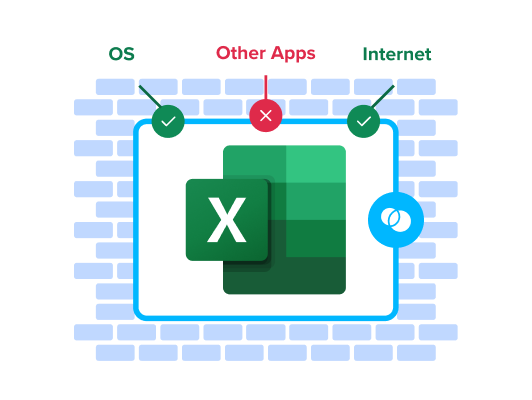
When a user launches a work application, Venn puts a virtual wrapper around it, visually indicated by a blue line around the application window. That work application is then running inside of the Secure Enclave, which acts like a firewall, controlling what can go in or out.

Users authenticate into Venn on their unmanaged Mac or PC.

Users launch work-sanctioned apps that run locally inside Blue Border.
Work apps and data are contained within a company-managed Secure Enclave.

All data is encrypted and corporate policies (HIPAA, FINRA, SEC, PCI, etc.) are actively enforced.
Full Security. Zero Compromise. On Any PC or Mac.
Purpose-built features to secure contractors, consultants, third parties and remote workers.
| Features |

|
VDI, Cloud PCs, DaaS | Browser-only | Company Managed |
|---|---|---|---|---|
Security and ComplianceProvide a single point of access for all work apps, files, and websites.
Venn
Full
VDI, Cloud PCs, DaaS
Mostly
Browser-only
Yes
Company Managed
Yes
|
Full | Mostly | Yes | Yes |
User Convenience and PrivacyAllows users to use a single computer for both work and life without impacting their user experience or performance in any way
Venn
Full
VDI, Cloud PCs, DaaS
Mostly
Browser-only
Yes
Company Managed
Yes
|
Full | Mostly | Yes | Yes |
CostHelps cut down on HW and management costs for remote employee computing devices
Venn
Full
VDI, Cloud PCs, DaaS
Barely
Browser-only
Yes
Company Managed
Barely
|
Full | Barely | Yes | Barely |
ControlAllows centralized security and IT policies and remote management of devices
Venn
Full
VDI, Cloud PCs, DaaS
No
Browser-only
Some
Company Managed
Barely
|
Full | No | Some | Barely |
Easy DeploymentSelf-service deployment and easy integration with 3rd party IT and security software
Venn
Full
VDI, Cloud PCs, DaaS
No
Browser-only
Some
Company Managed
Barely
|
Full | No | Some | Barely |
Remote Work at Scale
Venn
Full
VDI, Cloud PCs, DaaS
Mostly
Browser-only
Some
Company Managed
Barely
|
Full | Mostly | Some | Barely |
See Why Venn is the Trusted Choice
Managing a Remote Workforce Requires More Than Just Security
Venn’s mission goes beyond securing BYOD – we aim to empower our customers to fully embrace and optimize their entire remote workforce. To achieve this, we’re continuously enhancing Blue Border™ with advanced tools that tackle today’s most complex management challenges.
Software
Distribution
Venn Application Delivery ensures that applications are swiftly deployed and consistently maintained across all Venn-enabled devices.
Demonstrate Compliance
With Blue Border™, GRC leaders can have confidence that necessary controls are in place and auditable for SOC 2, HIPAA, FINRA, PCI, CMMC and more.
User
Privacy
Venn Privacy Shield embodies our commitment to privacy through innovative architecture and patented technologies, protecting user privacy outside the Blue Border™.
Onboarding Assistance

Venn Onboarding process includes technical assistance available to all new users.



The Future of Remote Work is Here. Schedule a Demo
Join the 700+ organizations including Fidelity, Guardian, and Voya that trust Venn to meet FINRA, SEC, HIPAA, NAIC, and SOC 2 standards. Request a demonstration today and discover how Venn can revolutionize your remote work security strategy by unlocking cost savings and limitless workforce agility.

