Remote Browser Isolation: Challenges, Alternatives, and Best Practices

What Is Remote Browser Isolation (RBI)?
Remote Browser Isolation (RBI) is a web security technology that isolates browsing activity by hosting user sessions on a remote server, preventing web content from directly reaching and executing on the user’s device. This creates a separation between the user’s device and potentially malicious web content, shielding against various online threats.
The RBI approach ensures that malicious website code, drive-by downloads, and browser exploits are confined within the isolation environment, never reaching the end user’s machine. Because all rendering and execution occur remotely, threats have minimal opportunities to impact devices on the corporate network. However, it has high bandwidth requirements, has significant latency issues, and often impacts user productivity and satisfaction.
RBI works by avoiding direct loading of web pages on the user’s computer. Instead, it executes the browsing session on a remote server, usually in the cloud. The remote server then transmits a safe, sanitized version of the webpage (often a rendered image or a video stream) to the user’s device.
While RBI has many advantages, today it is widely considered to be a legacy technology. Most users prefer to work on a browser on their device, which is generally faster and more convenient than RBI solutions. RBI also adds complexity and cost to an organization’s IT environment, when compared to leaner solutions like client-side isolation.
This is part of a series of articles about browser security.
How Does Remote Browser Isolation Work?
Remote browser isolation works by creating a secure, virtual environment to run web sessions, separating the execution of web content from the user’s device. When a user navigates to a website, the web traffic is routed to a remote server or cloud environment where the page is rendered and interacted with. The content is then streamed as pixels or a video feed back to the user’s browser, making it appear as though the page is running locally on their device.
This process effectively isolates any malicious code, such as malware or script-based attacks, by preventing it from executing on the local system. Even if the website is compromised, the isolation environment acts as a barrier, ensuring the attack does not affect the user’s machine or the corporate network. Additionally, RBI solutions can monitor and filter web traffic for harmful activities in real time, blocking any suspicious actions before they reach the end user.
The architecture can vary based on deployment, with some organizations using cloud-based RBI solutions, while others opt for on-premises setups. Both methods rely on secure isolation containers to handle modern web browsing demands without degrading user experience.
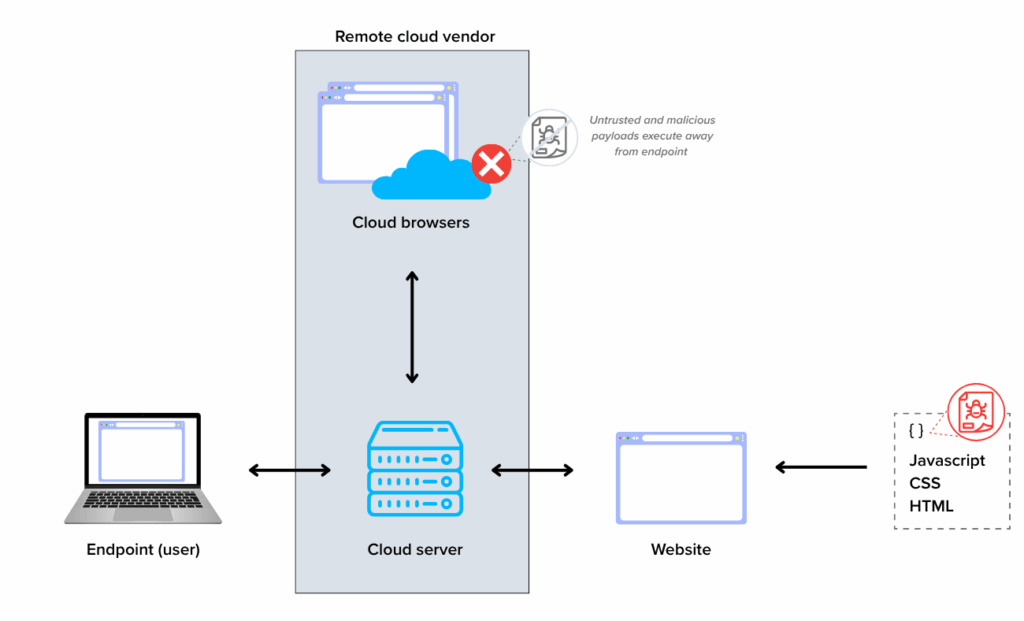
Types of Remote Browser Isolation
There are two main technical approaches to achieving RBI: DOM mirroring and pixel reconstruction.
DOM Mirroring
DOM mirroring is a technique where the Document Object Model (DOM) of a website is replicated from the isolated browser to the user’s device. The actual page executes on the remote server, with the server relaying a sanitized copy of the DOM to the local browser. Scripts are stripped or safely modified before delivery, allowing users to interact with web applications while blocking potential malware or exploits embedded in scripts.
This method keeps the user experience close to native browsing, including most site interactivity. Since scripts run in isolation before being sanitized, threats rarely make it onto the endpoint. However, DOM mirroring can present challenges when handling complex JavaScript or rapidly evolving dynamic web content, which may not always be correctly mirrored or sanitized.
Pixel Reconstruction
Pixel reconstruction, sometimes called pixel streaming, relies on transmitting images or video streams (essentially screen captures) of the web session from the remote environment to the local browser. The user’s browser acts as a thin client that displays the reconstructed pixels and transmits input (mouse clicks, keyboard, scrolls) back to the isolated environment, where real interaction with the website takes place.
This method ensures a high level of security, as no original web code or scripts ever reach the endpoint. All potential attack vectors embedded in the site’s code or scripts remain isolated on the remote server. The tradeoff is potential latency and reduced performance, especially for interactive or multimedia-rich sites, since all rendering is performed offsite and relayed as visuals to the user.
Benefits of RBI and Alignment with Zero Trust Security
Remote browser isolation (RBI) offers several advantages for organizations aiming to protect against browser-based threats:
- Enhanced security: By isolating web sessions, RBI prevents malicious code, malware, and exploits from reaching the user’s device, reducing the risk of infection and data breaches.
- Reduced attack surface: Since the execution of web content is done in a remote environment, sensitive devices are shielded from attack vectors commonly associated with browsers, such as drive-by downloads and script-based exploits.
- Protection against zero-day vulnerabilities: With RBI, even if a website contains an unpatched vulnerability or a zero-day exploit, the attack is contained within the isolated environment, preventing potential damage to the user’s device.
- Compliance with security standards: RBI helps organizations comply with data protection and privacy regulations by preventing the leakage of sensitive data through web-based attacks.
- Reduced IT overhead: With fewer endpoints exposed to threats, organizations can reduce the burden on IT teams to manage and respond to browser-based attacks, thus saving time and resources.
In addition to these benefits, RBI aligns well with the principles of zero trust security, which assumes that no device, user, or network is inherently trusted – everything must be verified before granting access. RBI enhances this model by ensuring that web-based interactions, one of the most common attack vectors, are securely isolated. Here’s how RBI supports zero trust:
- Continuous verification: RBI continuously isolates web traffic, ensuring that no malicious code or threats are introduced to the network, even if the user’s device is compromised.
- Segmentation of trust: By isolating the browsing activity from the user’s device, RBI ensures that no direct communication or execution of untrusted code occurs on the endpoint, enforcing the principle of least privilege.
- Granular access control: With RBI, organizations can set specific access policies for web browsing, ensuring that only approved sites and activities are allowed, and suspicious sites are blocked or isolated.
Common Challenges of Remote Browser Isolation
Latency and Bandwidth
Latency is a frequent concern in RBI deployments, as all browser content is rendered in a remote environment and streamed to the user’s device. Even minor delays can diminish the browsing experience, particularly with interactive web applications or media-heavy content. Streaming pixel-based sessions especially may introduce perceptible lag or slow response to user inputs, resulting in user frustration and decreased productivity.
Bandwidth requirements are also elevated with RBI solutions, especially pixel reconstruction approaches, since high-resolution screen contents are continually transmitted over the network. Organizations with limited bandwidth or remote workers may experience degraded performance. Successful deployments require careful planning and quality-of-service optimizations to support the increased network load.
Application Compatibility Issues
Many web applications utilize advanced features, plugins, or custom scripts that may not function properly when executed in an isolated environment. RBI platforms sometimes struggle to fully replicate the behavior of complex enterprise web apps, particularly when these apps require real-time communication, plugins, or proprietary authentication mechanisms. As a result, users could encounter broken functionality or inconsistent experiences, impeding productivity.
Moreover, certain security controls (such as script sanitization or active content filtering required by RBI) can inadvertently block legitimate features or disrupt critical workflows. Maintaining a balance between strong web isolation and seamless application compatibility requires ongoing tuning, whitelisting, and potential collaboration with app vendors for compatibility fixes.
Infrastructure and Cost Overhead
Launching and maintaining RBI solutions often involves significant infrastructure investment, whether the service is hosted in the cloud or on-premises. Cloud-based RBI solutions incur recurring subscription costs, while on-premises setups require capital investment in servers, storage, and network resources. These costs can escalate quickly as organizations scale their implementation across hundreds or thousands of users.
In addition to infrastructure, the operational complexity of deploying, integrating, and managing RBI can add burden to security and IT teams. Continuous monitoring, updating, and troubleshooting the isolation platform may require additional specialized staff or third-party support, further driving up total cost of ownership for the solution.
RBI Alternatives for Browser Security
The challenges and complexity of RBI have led many organizations to replace or complement it with other browser security technologies. Here are the primary options.
Secure Web Gateways
Secure web gateways (SWGs) act as inspection points between users and the internet. They filter web traffic by analyzing URLs, content, and downloaded files in real time. SWGs enforce corporate policies by blocking unsafe sites, preventing downloads of malicious files, and scattering access based on categories. Using URL filtering and content scanning, they can prevent exposure to known threats before a user ever accesses a page.
Unlike RBI, which isolates full sessions remotely, SWGs allow browsing to occur locally while scanning content on the network edge or in the cloud. This makes them faster and easier to deploy, with minimal impact on user experience. However, SWGs cannot fully prevent attacks hidden in complex scripts or zero‑day exploits that execute in the browser – tasks that RBI isolates more reliably.
Endpoint Security Solutions
Endpoint security solutions deploy protection software directly on user devices. These agents monitor behavior, detect suspicious processes, block malware, and prevent exploit-based attacks. They often include features like sandboxing, antivirus, and endpoint detection and response (EDR). Unlike RBI, which isolates the entire web session remotely, endpoint tools defend the browser in place – making execution local but protected.
This approach retains full browser functionality and responsiveness, with no streaming overhead or latency. It’s also typically easier to scale across many devices since no central isolation infrastructure is required. The trade‑off is that highly sophisticated or novel web-based threats can sometimes bypass endpoint defenses. Without isolation, those threats may still reach the device, so endpoint posture must be constantly updated with threat intelligence and patches.
Virtual Private Networks
Virtual private networks (VPNs) secure traffic by encrypting data between the user’s device and the corporate network. They are primarily designed to protect data in transit, not isolate browsing sessions. VPNs prevent eavesdropping and hide browsing from e.g. public Wi‑Fi, but once traffic arrives in the corporate network or to the internet, it still executes locally on the user’s device.
VPNs do not filter or sanitize web content; malicious scripts, drive‑by downloads, or browser exploits may still reach the endpoint. While VPNs improve privacy and transport security, they offer no defense-in-depth for browser-based attack vectors. They are often used in combination with SWGs or endpoint security to provide layered protection without the complexity and latency of full session isolation.
Client-Side Isolation
Client‑side isolation runs the browser in a protected container on the user’s device, isolating it from the main operating system. Variants include application sandboxing, containerized browser sessions, or secure enclave techniques that create a secure physical or logical space within the device. Web content executes locally, but within a confined runtime environment.
This provides stronger protection against web-based threats than traditional endpoint software while preserving near-native performance and low latency. Resource use is moderate; the container isolates harmful content without requiring remote rendering. Because execution remains local, client‑side isolation minimizes streaming overhead and avoids the user frustrations typical of RBI. Its effectiveness depends on the strength of the sandbox and the rigor of the containment boundaries.
Best Practices for Remote Browser Isolation Implementation
For organizations already invested in RBI, or considering adopting RBI, here are important best practices for effective implementation.
1. Define Isolation Policies for Threat Levels
Defining isolation policies based on the threat level of web content is essential for ensuring that security resources are appropriately allocated without compromising user experience. This requires an understanding of the various types of web traffic and their associated risks. For example, websites that handle sensitive financial transactions, allow file downloads, or include user-generated content may pose higher risks and should be subjected to stricter isolation protocols.
These policies should also be dynamic, allowing for real-time adjustments depending on the context of the user session. For instance, high-risk behavior like accessing external email links or downloading attachments may trigger stronger isolation policies automatically. Furthermore, creating a classification system for websites based on risk can help streamline the process, using tools like URL categorization and threat intelligence feeds. This approach helps maintain a balance between strong security and minimal disruption to everyday browsing activities.
2. Prepare for Performance Optimization
Performance optimization is one of the most critical aspects of a successful RBI deployment, as delays in loading or lagging web applications can significantly reduce productivity and frustrate users. Optimizing RBI performance begins with choosing the right deployment method (whether cloud-based or on-premises) based on the organization’s infrastructure and performance needs. For cloud-based deployments, selecting a provider with sufficient global data center coverage and low-latency connections is crucial. Using a content delivery network (CDN) to cache frequently accessed content closer to the user can further reduce latency.
For on-premises deployments, leveraging high-performance hardware such as SSDs, dedicated GPUs, and optimized network switches can help support the heavy computational demands of rendering complex websites and streaming content in real-time. Additionally, organizations should assess the browsing patterns of their user base and deploy load balancing techniques to distribute web traffic efficiently across available isolation servers.
Regular monitoring of network bandwidth usage, latency, and server load should be implemented to adjust resource allocation dynamically based on demand, ensuring that performance doesn’t degrade during peak usage.
3. Monitor and Log Sessions for Compliance
Monitoring and logging web sessions are crucial for maintaining a secure and compliant RBI environment. Logging every web interaction allows administrators to track which users visited specific websites, identify any potential security events, and ensure that all activities comply with internal security policies and external regulatory requirements.
The logs should be detailed enough to provide insights into session data, including which websites were accessed, what actions were performed, and whether any suspicious activities were detected.
For compliance, logs should be securely stored and easily accessible for audit purposes. They need to meet specific legal and regulatory standards, including data retention policies and access controls. For example, organizations that handle sensitive data may need to store logs for a set number of years and ensure that logs are tamper-proof to meet standards like GDPR or HIPAA.
4. Align with Security Frameworks
Aligning RBI with well-established security frameworks, such as zero trust and the NIST Cybersecurity Framework, strengthens the overall security architecture and ensures that RBI integrates effectively with other security measures.
When integrating RBI into a zero trust framework, the isolation solution should be capable of providing real-time authentication, continuous monitoring, and detailed session control, ensuring that only verified and authorized users can access specific web resources. Additionally, it should align with the least-privilege access model by restricting unnecessary access to certain websites or types of web activity, depending on the user’s role or security posture.
For organizations following the NIST Cybersecurity Framework, RBI can support several key areas, such as Protect (by isolating web sessions from harmful content), Detect (through real-time monitoring of web traffic and user behavior), and Respond (by providing isolation and containment of any detected threats).
5. Educate End Users and Administrators
For end users, training should focus on helping them understand how RBI improves their security by isolating potentially dangerous web traffic. They should be made aware of the types of web content that may be isolated (such as risky websites or files) and how RBI will affect their day to day work. Aligning expectations can reduce the impact on user productivity and satisfaction.
Administrators require more in-depth training on managing the RBI infrastructure. This includes understanding how to configure and fine-tune isolation policies, monitor system performance, and handle troubleshooting. They should be able to configure the system to scale as needed, ensure that it integrates smoothly with other security tools like secure web gateways (SWGs) and endpoint protection, and ensure that the system is regularly updated to handle new web threats.
Venn: Ultimate Client-Side RBI Alternative
If you need to secure browser activity on unmanaged or BYOD laptops, Venn may be the Remote Browser Isolation alternative you’re looking for.
Unlike most RBI solutions, Venn does not use any sort of remote hosting to secure web activity. In fact, with Venn, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave, protecting and isolating business activity while ensuring end-user privacy. In this way, Venn not only secures browser activity, but also company data that users access through installed applications like Zoom, Slack, CAD, etc.
As such, Venn is an excellent RBI alternative for companies that need to secure company data on laptops they do not own or manage. You can learn more about Venn here.
More Blogs

In my previous blog I discussed the impact the 2nd Digital Transformation is having on IT teams andd employee computing experiences around the globe. Understanding this massive shift from the perspective of IT leadership is all well and good, but what does this transformation look like from an employee standpoint? In other words, how are […]

As a Senior Product Owner here at Venn I get asked a variety of questions about our secure remote workspace, often revolving around the same concepts or fundamental aspects of the product. With most users accustomed to slow, clunky legacy VDI experiences, Venn’s unique set of features and capabilities represent deviations from the way most […]

The COVID-19 pandemic forced organizations around the world to rapidly design remote work programs that both protected their employees and ensured business continuity in turbulent economic times. From the onset of this shift to dispersed organization structures business leaders around the world naturally assumed that it was to be a disruption, not a complete reset, […]