Trusted Platform Module vs Secure Enclave: Which Is Better?
Trusted platform module (TPM) technology has served as the gold standard for hardware‑based security for a long time, safeguarding millions of laptops and desktops by storing cryptographic keys in a chip that is tamper-resistant. From BitLocker drive encryption to secure boot, TPM security supports many everyday protections that keep operating systems and sensitive data out of reach of attackers.
But the workplace has changed faster than the silicon inside most endpoints. Global expansion, nonstop remote work, and bring‑your‑own‑device (BYOD) policies mean contractors, partners, and employees may log in from anywhere, and often on hardware that IT teams do not own or fully control. In this sprawling environment, even a purpose‑built chip like the TPM faces limits: provisioning keys only after the right driver is installed, relying on physical possession of the device, and offering little coverage for mobile platforms.
Enter the Secure Enclave: a modern, platform‑agnostic approach that isolates sensitive data in a protected workspace on a device, regardless of who owns the device. By abstracting security from the underlying hardware and extending controls to unmanaged endpoints, a Secure Enclave helps organizations meet today’s distributed‑workforce security demands without sacrificing user experience.
In this blog, we will unpack what a trusted platform module is, examine its strengths and weaknesses, and deliver a comparison of Secure Enclaves vs TPMs to determine which model better fits contemporary BYOD strategies and remote‑work realities.
What Is a Trusted Platform Module (TPM)?
A Trusted Platform Module (TPM) is a specialized chip built into many modern laptops and desktops that helps protect sensitive information through secure cryptographic operations.
At a high level, TPM is used to securely generate, store, and manage cryptographic keys, ensuring that data stays encrypted and protected from unauthorized access, even if the system is compromised. A common example of this in action is BitLocker, Microsoft’s disk encryption feature, which uses the TPM to lock and unlock the drive securely.
Core Functions of TPM Include:
- Secure generation and storage of cryptographic keys
- Keys are never exposed to the operating system or user, preventing theft.
- Device authentication and attestation
- Confirms a machine’s identity and integrity before granting access to sensitive systems.
- Secure boot and system integrity checks
- Prevents unauthorized code or firmware from running during startup.
- Protection against firmware and ransomware attacks
- By ensuring code authenticity, TPM makes it harder for malware to take hold at the boot or BIOS level.
TPMs are common in company-issued Windows devices, where they power features like BitLocker and Windows Hello, which uses facial recognition or fingerprint scanning to authenticate users securely.
But TPMs were designed for company-owned, fully managed devices. They weren’t designed for the unmanaged or personally owned machines often used in BYOD or contractor-heavy environments. When devices fall outside the control of IT teams, TPM security starts to show its limitations.
That’s where Secure Enclave technology comes in.
What Is a Secure Enclave?
A Secure Enclave is a protected, local workspace on any unmanaged computer that isolates and encrypts company data, separating it from any personal use on the same machine.
You can think of it as the BYOD-era equivalent of MDM for laptops, but much more flexible and privacy-conscious. Rather than locking down the entire device, a Secure Enclave creates a company-controlled workspace that enforces policies and security measures only where it matters: on company data.
Secure Enclaves run work apps locally on the endpoint, secure company data on unmanaged devices, separate personal and work usage, and reduce IT burden. Let’s discuss:
Work Apps Run Natively
Unlike virtual desktop infrastructure (VDI), apps inside a Secure Enclave run locally on the device. This means no performance lag, no streaming delays, and no need for remote infrastructure. Users get full native functionality, even with graphics-heavy or latency-sensitive applications.
Company Data Is Secure
Work files, applications, and network traffic stay protected. Only apps running inside the enclave can access corporate data, and all data is encrypted; both at rest and in transit.
Separates Personal and Business Use
With a Secure Enclave, personal and work environments remain strictly separated. Venn’s Blue Border™ makes it obvious to users when they are inside the secure workspace vs. in personal windows by surrounding work windows with a blue border. Everything outside the Blue Border remains private and untouched by IT.
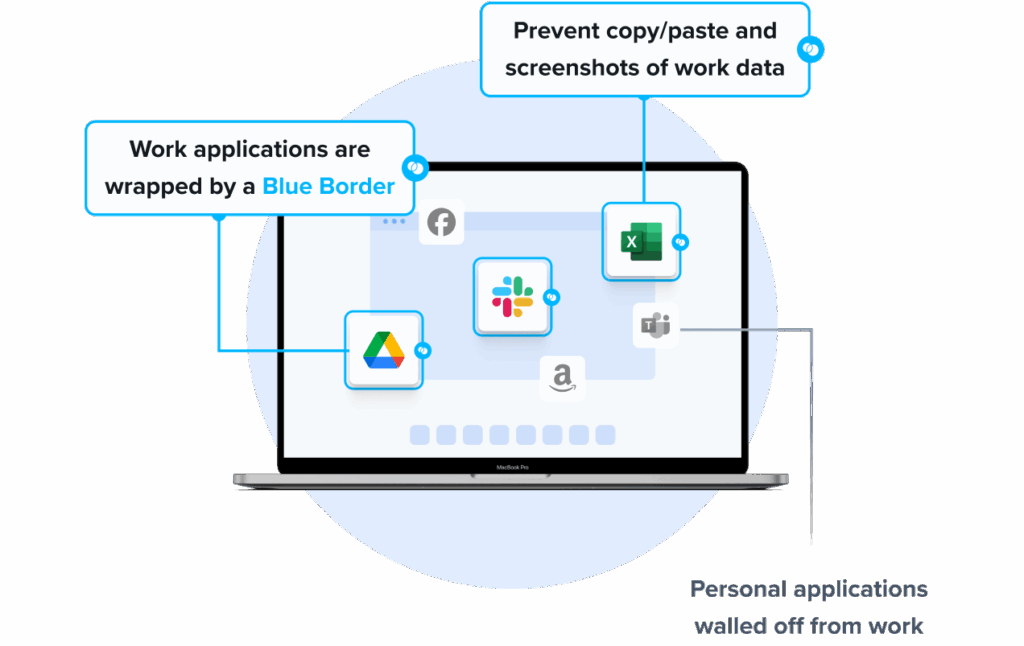
Reduces IT Burden
Provisioning a Secure Enclave is fast and simple. Contractors can be onboarded via email and offboarded instantly; no need to ship, recover, or wipe devices manually. IT teams can focus on more strategic initiatives, instead of locking down and shipping hardware.
Secure Enclave vs TPM: Comparing Technologies
Both TPM and Secure Enclaves help secure company data, but they approach the problem from different angles.
Here’s how they compare across key categories:
| Category | Trusted Platform Module (TPM) | Venn’s Secure Enclave Technology |
| Functionality | Hardware-based chip for key generation and secure boot; supports encryption tools like BitLocker. | Software-defined secure workspace; protects work apps, data, and traffic on any unmanaged device. |
| Security | Protects device integrity at the system level; limited to boot-time and hardware-layer protection. | Isolates work from personal use; encrypts all data at rest and in transit; protects the full work environment. |
| Compliance & Management | Helps meet encryption standards; requires physical provisioning and manual management. | Turnkey compliance; quick onboarding and offboarding. |
| Use Case & Flexibility | Ideal for enterprise-issued, managed devices; limited adaptability to BYOD or remote users. | Built for BYOD, remote work, and contractor use; deployable on any supported device. |
| User Privacy & Experience | Invisible to users; no separation of personal and work data; limited UX control. | Clear boundary between work and personal use; strong privacy protections; apps run locally with no latency. |
Functionality
Trusted Platform Modules are built into the hardware, and they specialize in cryptographic key generation and secure storage. They operate at the system level, but don’t control user applications or workspaces. They are used for device authentication, disk encryption (i.e., BitLocker), and secure boot.
Venn’s Secure Enclave technology operates at the software level, independent of hardware. By downloading the software, you create a protected, encrypted workspace on the endpoint. Venn supports multi-factor authentication and enforces granular access controls within the enclave. All network traffic within the enclave is encrypted and routed through secure tunnels, ensuring data is secure both at rest and in transit. Venn runs all apps and data locally, ensuring seamless user experience and functionality.
Why Venn’s Secure Enclave technology wins: It not only protects encryption keys but also enforces policy controls and encrypts all work-related data movement, extending security beyond what TPM can offer at the device level. defines how apps and data behave on any device.
Security
TPMs are great for boot-level integrity, secure key storage, and hardware authentication. They help detect unauthorized firmware or system changes. However, they are not as deeply integrated into application-level environments.
Venn’s Secure Enclave technology creates a software-defined, isolated execution environment directly on user devices, with a clear visual boundary between work and personal use. All work data and applications run locally within the enclave, fully separated from the personal environment. This minimizes the attack surface while ensuring end-user privacy. It also delivers fine-grain isolation at the application and workspace level.
Why Venn’s Secure Enclave technology wins: it ensures both company data protection AND user privacy, providing isolation that is perfect for BYOD and remote work scenarios; something that TPM alone can’t achieve.
Compliance and Management
Compliance refers to how well an organization meets external regulations or internal policies designed to protect data, privacy, and operations. Examples of compliance mandates are HIPAA, SOC 2, FINRA, and GDPR.
Management refers to the day-to-day tasks IT teams carry out to control access, update policies, onboard and offboard users, and monitor device health or usage. Examples of management include setting up and decommissioning devices, pushing security policies, and performing remote wipes or updates.
Let’s discuss the differences between TPM and Venn’s Blue Border for ensuring compliance and ease of management.
Trusted Platform Modules (TPMs) can help companies meet compliance requirements for device integrity and encrypted storage. However, in terms of management, TPMs are hardware-centric and usually require hands-on IT involvement for device provisioning and decommissioning.
Venn’s Secure Enclave technology enforces compliance policies directly within the enclave, supporting standards including HIPAA, FINRA, SOC, and more. And with centralized management that enables instant policy updates and quick onboarding/offboarding, Venn offers turnkey compliance and strong, intuitive management for IT teams.
As such, Venn’s Secure Enclave offers a better solution for compliance and management.
Use Cases and Flexibility
TPM is well-suited for traditional enterprise environments. It works best on company-issued laptops and desktops that IT teams fully manage. It is ideal for secure boot, disk encryption, and platform integrity checks. But TPM depends on physical hardware, which makes it hard to use in environments where devices aren’t owned or controlled by the company. In a world full of contractors, remote workers, and BYOD policies, TPM simply doesn’t scale.
Venn’s Secure Enclave is built for modern work environments, ideal for remote workers and contractors on BYOD or unmanaged devices. Venn is hardware-agnostic and IT can deploy it via email, making onboarding fast and easy, with no shipping or imaging required. Contractors can be up and running in minutes, and when the job ends, access can be removed instantly with remote wipe capabilities. Venn’s Secure Enclave technology supports a wide range of use cases across industries, regions, and work models. It’s ideal for organizations that need to move quickly and securely without being tied to hardware.
Venn offers unmatched flexibility, making it the superior choice when it comes to a range of use cases and flexibility.
User Privacy and Experience
TPM protects the device and operating system, but it doesn’t separate work from personal use. There’s no clear line between business and personal data, especially on a BYOD laptop, which can lead to privacy concerns and accidental data exposure. The protections TPM offers happen in the background, so the user isn’t always aware of what’s being secured, and what’s not.
Venn’s Secure Enclave technology takes a different approach. It creates a clear boundary between personal and work environments. Venn’s Blue Border shows users when they’re in a work window vs. a personal window. Everything inside the Blue Border is protected and managed by the end-user’s company; everything outside stays private to the end-user. At the same time, work apps run natively on the device, providing a completely seamless user experience. That means Venn provides better performance, less frustration, and a smooth user experience that doesn’t get in the way of productivity.
Venn offers the ultimate combination of user privacy and experience, addressing the usability gaps left by TPM-centric approaches.
Secure Diverse Endpoints with Confidence
While TPM has delivered trusted hardware-based protection for years, it was never designed for today’s dynamic, hybrid, and BYOD workforces. As companies expand globally and rely more on remote and contractor-based workers, the limitations of hardware-tied security models become more apparent.
Venn’s Blue Border, powered by Secure Enclave technology, rises to the challenge. It offers strong encryption, centralized policy control, seamless compliance, and a great user experience, all without IT teams needing to own or manage the whole endpoint device itself. It also runs apps and data locally.
Whether your team is across the hall or across the globe, Venn ensures company data stays protected and separate from personal use, making it the superior choice over TPMs for securing work data on any device.
Ready to see how Venn’s Blue Border can simplify BYOD security for your organization?
Ronnie Shvueli
Senior Digital Content Marketing Manager
More Blogs


