The Secure Workspace for Remote Work
Secure company data and apps on unmanaged or BYOD computers used by contractors and remote employees — without VDI
Venn is trusted by over 700 companies worldwide



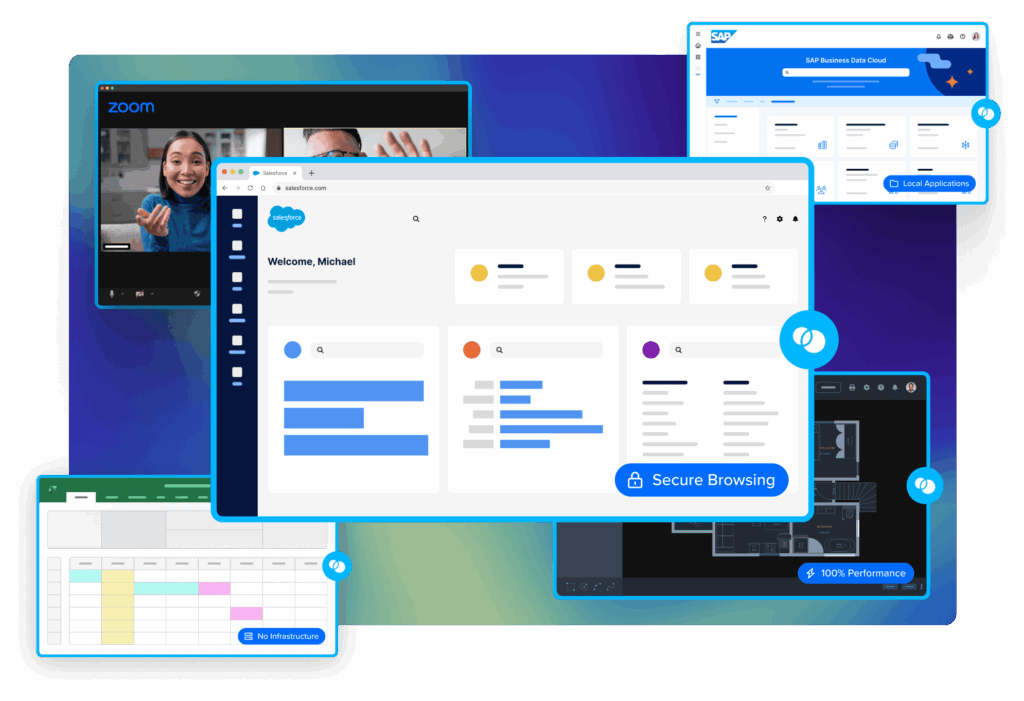
Run Work Apps Locally. Secure Data Instantly. No VDI Required.
Remote and contract employees want to use their own laptops – but unmanaged devices create security and compliance risks. Traditional fixes like VDI or issuing company hardware are costly and slow. Venn’s Blue Border™ offers a smarter alternative: secure work apps and data locally on any PC or Mac, with no hosting, virtualization, or extra hardware required.
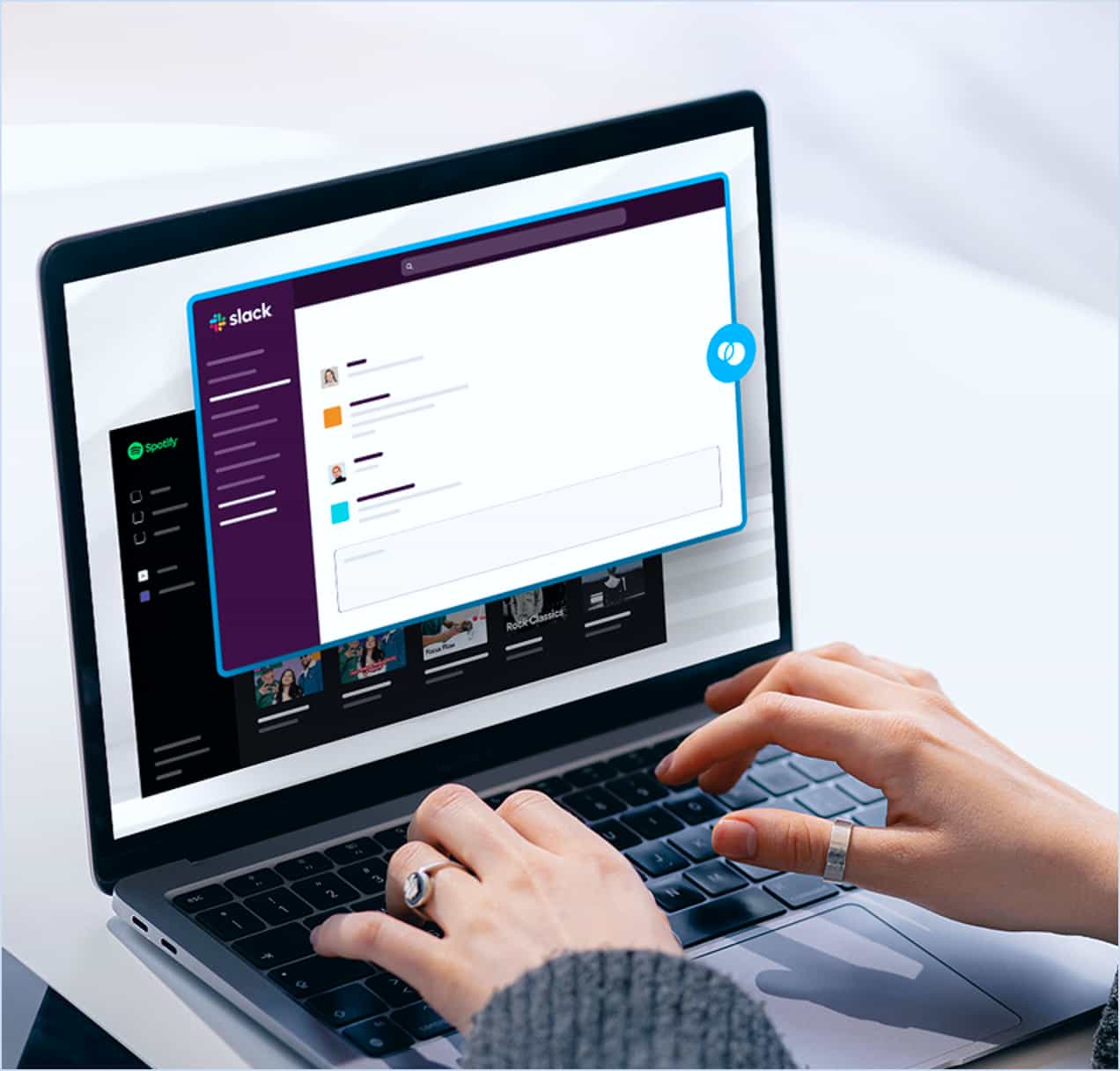
With Blue Border™, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Blue Border™ – protecting and isolating business activity while installed apps run locally, natively, and securely. No hosting and no virtualization.

Download the Blue Border™ Product Brochure
- Runs on Any Device – Isolates work apps and data locally on the endpoint, keeping corporate access fully governed without touching personal files or activity.
- Zero Lag, Zero Latency – Eliminates the performance complexity of VDI/DaaS by letting users work natively on their own machines.
- Compliance-Ready Controls – Apply precise policy, data protection, and audit enforcement controls that meets strict regulatory standards.
See how Blue Border™ replaces virtual desktops and legacy remote access tools
Reduce IT complexity and deliver real business value
By eliminating the need to provision, ship, and manage company-owned devices, BYOD streamlines operations and lowers IT overhead. It accelerates onboarding, supports remote flexibility, and reduces capital costs — all while giving employees and contractors the freedom to work on devices they already know. When implemented securely, BYOD becomes a powerful lever for scaling efficiently and driving measurable results.
Cost Reduction
Reduce or eliminate the cost and complexity of buying, managing and shipping company-owned PCs and Macs, as well as VDI licensing and infrastructure.
Security and Compliance
Protect company data from accidental or malicious exfiltration, compromise or loss. Turnkey regulatory compliance with industry standards including HIPAA, PCI, SOC, SEC, FINRA and more.
Workforce Agility
Rapidly onboard and offboard remote workers on the PC or Mac of their choosing in minutes. Even if they are joining part-time or for a couple weeks, hire any employee or contractor anywhere quickly and securely.
Alleviate IT Burden
Refocus IT resources on important strategic initiatives instead of wasting time managing and locking down employee laptops or supporting frustrated users on complex VDI infrastructure.
User Privacy
Assure end-users of their privacy outside Blue Border™ so they are willing to utilize their personal machines for work.
User Convenience
Enable users to work locally with their preferred installed applications with clear separation between work and personal uses.

Revolutionize the Future of Remote Work
The expansion of remote work is forcing change. The traditional model of provisioning and managing corporate laptops is becoming unsustainable. IT leaders are under pressure to do more with less – and BYOD presents a smarter path forward. With the right controls in place, organizations can reduce complexity, lower costs, and empower remote teams to work securely from their own devices.

Venn vs. VDI/Enterprise Browser/SASE/UEM
BYOD has exposed gaps in many remote work security solutions. VDI is expensive, slow, and a nightmare to manage. Enterprise browsers limit app access and force change management. SASE focuses on network traffic and Endpoint Management (UEM) is entirely focused on full device control. What do they all have in common? They all fall short when it comes to securing business data on unmanaged or BYOD laptops.
Venn is purpose-built for BYOD. With Blue Border™, users work locally on their own computers while IT leaders maintain full control over data access. No infrastructure to maintain, no virtual desktops to host, and no need to take over the entire device.



See Why Venn is the Trusted Choice
Why Customers Choose Venn

Ensure contractors and remote employees are secure and productive. Venn securely enables BYOD workforces on any personal computer (PC or Mac), removing the burden of buying, securing, managing and shipping laptops.
Say goodbye to VDI. Venn offers an intuitive, cost-effective solution for enabling BYOD that is purpose-built to strengthen security and compliance. Business applications run locally – not from a remote server – providing 100% performance and an ideal user experience.
Get out of the business of company-managed computers. Eliminate the time-consuming task of buying, shipping, managing and securing laptops for every remote employee and contractor. IT teams can now focus on more strategic initiatives.
Securely manage third-party contractors, freelancers and offshore workers. Whether they use a PC or Mac for their personal device, Venn ensures company data is protected without the cost and complexity of VDI or sacrificing user productivity.
Protect company data without owning and or managing the entire device. Venn’s Blue Border™ prevents accidental or malicious data exfiltration, compromise or loss on any unmanaged computer with DLP policies that span copy/paste, data transfers, screenshots and more.
Experience a new level of control with Venn’s Blue Border™, which is similar to an MDM solution but for laptops. Work lives in a company-controlled Secure Enclave installed on the user’s computer, where business activity is isolated and protected from any personal use on the same computer. Unlike traditional MDM, Venn does not manage the entire device – in fact there is no device management at all. Just control over business apps and data.
Blue Border™ enable workers to use their personal computers the way they want – for both work and life. Venn keeps all work and personal activities separate and secure while ensuring end-user privacy. When users are working outside of Blue Border™, no one at their company or Venn can see their activity.
Venn accelerates M&A integration by providing simple and streamlined onboarding for acquired employees. By reducing bottlenecks that can hinder rapid scale (infrastructure and hardware) and enforcing unified security policies through Blue Border™, Venn helps ensure business continuity, compliance, and faster time-to-value during the transition.
How BYOD Delivers Value Across the Org
IT Leaders
Cut costs and securely enable BYOD workforces on unmanaged devices. Revolutionize IT operations with rapid worker onboarding and off boarding in just minutes.
Compliance and
Security Professionals
Protect company data without owning and controlling every device. Prevent accidental or malicious data exfiltration. Maintain compliance with PCI, SOC 2, HIPAA, SEC, FINRA, CMMC, NAIC and more.
End Users
Work and live comfortably on any personal computer of choice. PC or Mac. Enjoy guaranteed privacy and maximum flexibility.

Secure Your Remote Workforce in Minutes. Not Weeks
Schedule a demo to discover how Venn provides a cost-effective VDI alternative that is simpler to manage, faster to deploy and loved by end users
