Best Browser Security Software: Top 5 Options in 2025

What Is Browser Security Software?
Browser security software protects users and organizations from threats during web browsing. Unlike legacy antivirus or network security solutions, browser security software focuses on threats from web content, web applications, and browser plugins. Common risks include phishing attacks, drive-by downloads, malicious extensions, and data breaches from compromised web sessions.
As business operations increasingly rely on cloud services and web-based tools, the browser has become a critical endpoint, making it a prime target for attackers aiming to compromise credentials or sensitive data.
These solutions combine multiple defense mechanisms tailored for web environments, such as isolating browsing sessions, monitoring activity in real-time, and enforcing policies to control what data can leave the browser. With the evolution of remote work and the use of unmanaged devices, browser security software fills gaps left by traditional endpoint and perimeter defenses. It acts as a control point at the user interface level, directly protecting work done in the browser.
In this article:
Key Capabilities of Modern Browser Security Software
Isolation and Sandboxing
Isolation and sandboxing separate web content from the host operating system to prevent harmful code from reaching device resources. By creating a virtual workspace or a container for each browsing session, these tools block malware and exploits from infecting the local machine. This approach neutralizes threats like zero-day vulnerabilities in the browser or plugins before they have the chance to spread.
Departments handling regulated data can be restricted to specific, secure browser instances. Advanced isolation solutions can stream the visual representation of a page to the user, keeping webpage execution off the endpoint. This reduces attack surface area, especially on endpoints that may not be fully managed or patched, and makes it harder for attackers to exfiltrate data.
Zero Trust Access Controls
Zero trust access controls ensure that every user and web session is strictly authenticated and continuously verified, with no implicit trust granted based on network, device, or previous authentication state. Browser security solutions enforce these principles by verifying user identity, endpoint security posture, and context, such as geographic location or device type, before granting access to websites or internal web applications.
Policy enforcement can be fine-tuned to allow only the precise set of users, devices, or conditions under which a given application can be accessed. Suspicious activity can automatically trigger additional authentication steps or session termination. For organizations, this means granular, dynamic control over sensitive data and resources.
Secure SaaS and Web Application Access
Secure access to SaaS and web applications is crucial as organizations rely more on third-party platforms for daily operations. Browser security software provides controlled, policy-enforced access to business-critical applications, regardless of user location or device ownership. Features may include conditional access policies based on user role, real-time risk assessment, and adaptive authentication mechanisms that respond to contextual signals.
Critical to this capability is the differentiation between corporate and personal accounts, and the ability to enforce safe browsing and data handling practices. For example, copying and pasting sensitive data, downloading files, or uploading documents to unauthorized apps can be restricted within the browser. This helps prevent accidental or deliberate data leaks and aligns browser use with corporate compliance requirements.
Data Loss Prevention (DLP) in the Browser
Data loss prevention (DLP) in the browser extends conventional DLP technology directly into the web interface, inspecting data as it moves in and out of web applications. This includes monitoring clipboard activity, file downloads and uploads, screenshot attempts, or even printing within the browser. Policies can block or log such actions when they involve regulated or sensitive data, such as customer records, intellectual property, or financial information.
Browser-based DLP is particularly valuable in environments with bring-your-own-device (BYOD) policies or contractors needing temporary access to internal apps. By applying DLP controls within the browser itself, organizations maintain visibility and control even when they lack full management of the underlying endpoint.
Visibility and Activity Monitoring
Visibility and activity monitoring are core strengths of browser security platforms, giving organizations detailed insight into what users do in their browsers. This includes tracking visited URLs, login attempts, data downloads, form submissions, and extension installations. Real-time activity logs support security investigations and compliance reporting by creating an auditable record of web interactions.
This continuous monitoring enables threat detection and response that is specific to the browser context. For example, security teams can be alerted when users access shadow IT applications, attempt to sidestep security policies, or interact with potentially malicious websites. Unlike endpoint security tools, browser-based monitoring catches risks unique to web workflows.
Go Beyond the Browser. Secure All Apps.
Learn how Venn secures both browser-based AND locally installed apps on unmanaged devices.

Notable Browser Security Software
1. Venn

Venn offers a fundamentally different approach to browser-based security by creating a secure local environment on the user’s device, rather than forcing users into a browser-only workflow. Venn separates and isolates work from personal activity on the same laptop, allowing companies to secure work apps and data without managing the entire device. This makes Venn particularly well-suited for BYOD, remote, and contractor-heavy workforces that need strong security controls without relying on VPNs, VDI, or restrictive enterprise browsers.
Key features include:
- Secure Enclave technology: Encrypts and isolates work data on personal devices, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
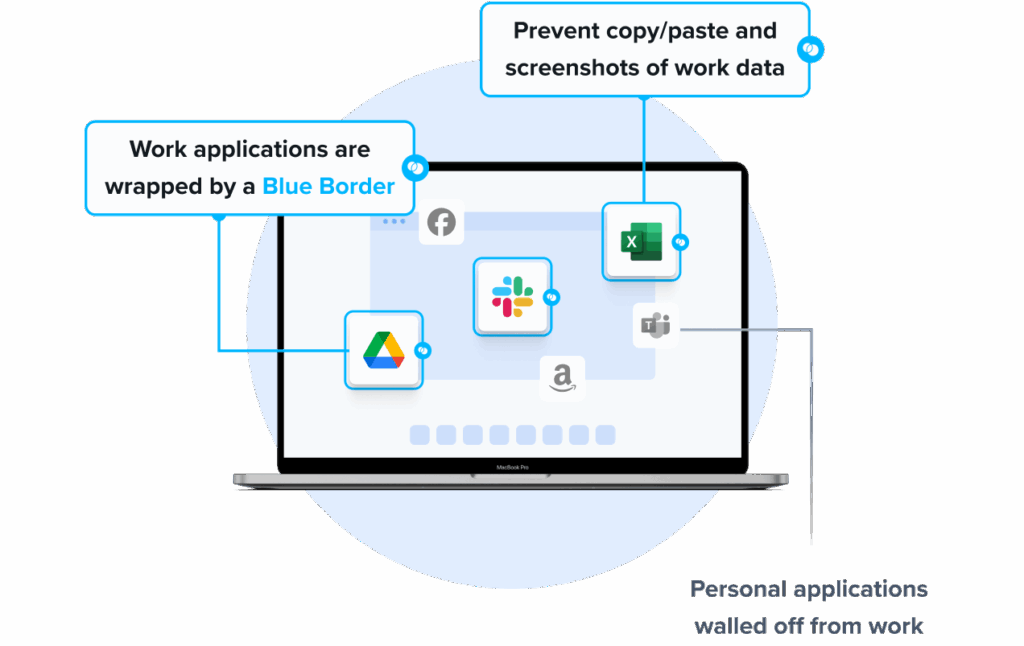
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Turnkey compliance: Using Venn helps companies maintain compliance with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
2. LayerX Security

LayerX Security is an agentless browser extension platform that turns a browser into a secure enterprise tool. Built to address the browser as the primary blind spot in enterprise security, it offers protection against data leakage, shadow SaaS usage, risky browser extensions, GenAI data risks, identity threats, and web-based attacks.
Key features include:
- Agentless architecture: Deploys across any browser using MDM tools, with zero impact on performance or user experience
- GenAI security controls: Monitors and restricts usage of generative AI tools to prevent sensitive data exposure
- Web and SaaS DLP: Prevents unauthorized file uploads, clipboard use, and data sharing across cloud and web apps
- Shadow SaaS detection: Identifies and controls unsanctioned SaaS usage within the organization
- Risky extension protection: Detects and blocks potentially malicious or non-compliant browser extensions
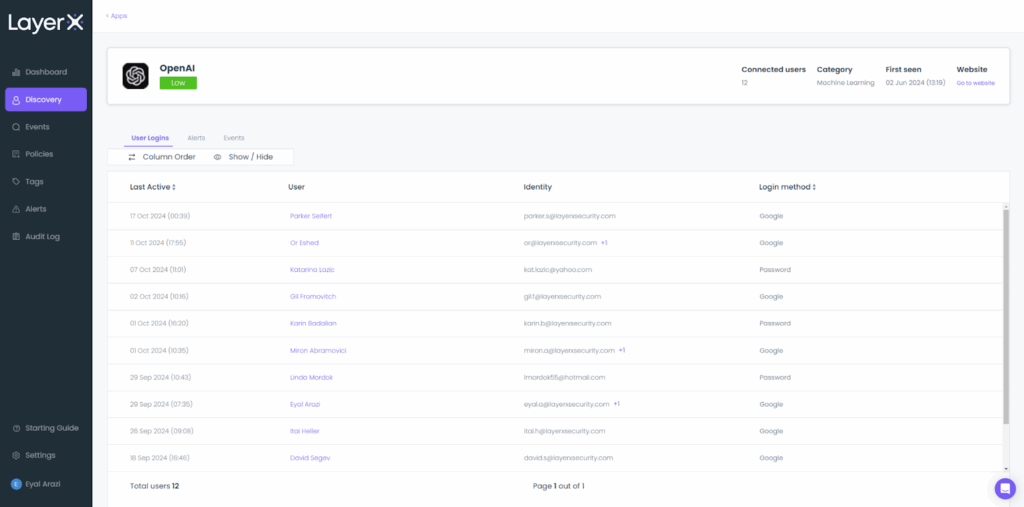
Source: LayerX
3. ManageEngine Browser Security

ManageEngine Browser Security is a centralized browser management and security solution to help enterprises protect sensitive data and enforce consistent browser policies across diverse environments. It enables IT administrators to gain visibility into browser usage, manage browser configurations, control access to extensions and web applications, and lock down browsers.
Key features include:
- Centralized browser management: Administer security settings across multiple browsers from a single console
- Browser usage visibility: Track browser activity and identify risky add-ons and plugins within the network
- Add-on control: Detect, manage, and restrict browser extensions that could lead to potential security breaches
- Security configuration enforcement: Push standardized browser policies to endpoints to prevent attacks like phishing and credential theft
- Web access control: Grant or block access to specific browser-based applications and websites based on business policies
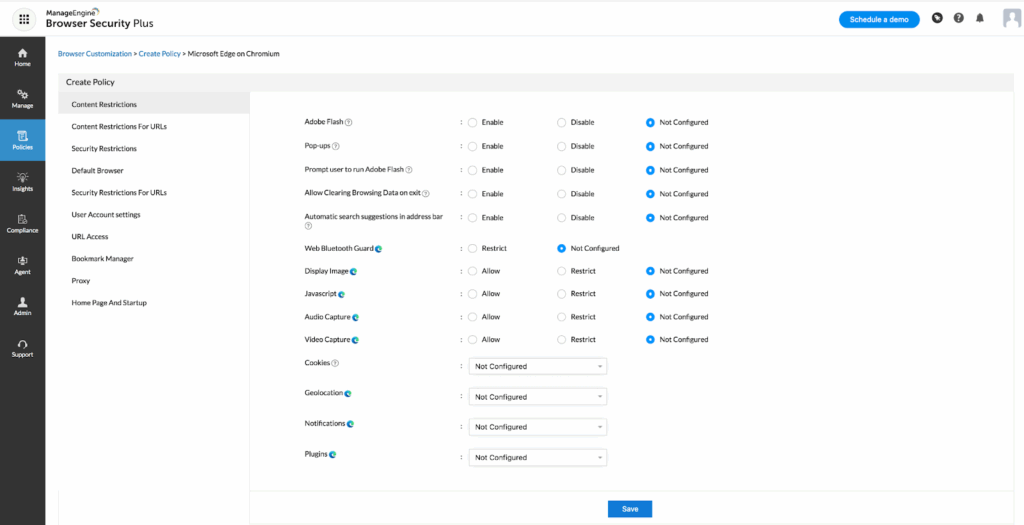
Source: ManageEngine
4. Island

Island is an enterprise browser that combines native security, access control, and productivity-enhancing tools into a single platform. It embeds enterprise-grade protections directly into its architecture. This allows organizations to manage application access, enforce security policies, and automate workflows.
Key features include:
- Universal application access control: Enforces conditional access based on user identity, device, network, location, and app context
- Built-in zero trust network access: Provides secure access to corporate resources without relying on external VPN or VDI infrastructure
- Security by design: Protects against malware, phishing, session hijacking, and other web-based threats through integrated defenses
- Context-aware data protection: Dynamically applies data usage policies to prevent leakage across applications and sessions
- Device visibility and management: Offers insight into user activity and device posture for compliance and threat detection
Source: Island
5. Seraphic Security

Seraphic Security offers a browser-native protection platform that transforms a standard browser such as Chrome, Edge, Firefox, or Safari into a secure enterprise browser without altering the user experience. It deploys an invisible agent that brings security and governance into the browser.
Key features include:
- Bring your own browser (BYOB): Secures the browsers users already prefer, removing the need to standardize or replace endpoints
- Real-time threat prevention: Blocks phishing, malware, and advanced web-based attacks as users browse, without latency
- Data protection: Controls sensitive actions like file uploads, copy-paste, screen sharing, and printing inside the browser
- Secure remote access without VPN/VDI: Enables access to enterprise apps from any location or device without costly infrastructure
- Zero-day attack mitigation: Detects and blocks novel exploits that bypass traditional endpoint or network security
Source: Seraphic Security
Key Considerations for Choosing Browser Security Software
Selecting browser security software involves more than comparing feature checklists. Organizations must align product capabilities with their specific threat models, regulatory obligations, and operational realities. Below are key factors to consider when evaluating solutions:
- Deployment model compatibility: Determine whether the solution fits your environment. Main options include secure remote platforms, agent-based, agentless, extension-based, or standalone browser. Each model has trade-offs in visibility, control, user experience, and ease of deployment across managed and unmanaged devices.
- Support for BYOD and unmanaged devices: Ensure the solution can enforce policies and maintain visibility even when users access corporate resources from personal or untrusted devices. This is critical for remote workforces, contractors, and partner ecosystems.
- Granularity of policy controls: Evaluate how precisely you can define access rules, data protection policies, and user behavior controls. Granular policy enforcement allows for context-aware restrictions that adapt to user role, app sensitivity, device posture, and risk signals.
- Visibility and auditing depth: Assess the solution’s ability to capture detailed activity logs, such as URL visits, file transfers, form inputs, and extension usage, while maintaining compliance with privacy regulations. Logs should be easily exportable and searchable for incident response and audits.
- Integration with existing security stack: Check for compatibility with your identity providers (e.g., SSO, MFA), SIEM tools, endpoint detection and response (EDR) platforms, and DLP systems. Seamless integration reduces operational overhead and extends existing controls into the browser.
- User experience and performance impact: Solutions must secure browsing without degrading performance or interfering with legitimate workflows. Poorly designed tools may slow down applications, block necessary extensions, or create friction that leads to workarounds.
- Scalability and administrative simplicity: Consider how easily the solution can scale across thousands of endpoints and how intuitive the policy management interface is. Centralized management consoles, role-based admin access, and prebuilt templates can reduce administrative overhead.
- Vendor viability and innovation roadmap: Investigate the vendor’s financial health, support model, and pace of innovation. Browser threats evolve rapidly; look for providers actively updating protections against new exploits, such as those involving generative AI or novel SaaS abuse tactics.
Conclusion
Browser security software and remote work solutions have become a critical layer of enterprise defense as work shifts to the cloud and employees operate from varied devices and locations. By protecting the browser itself, these solutions address threats that bypass traditional perimeter and endpoint controls, while also giving organizations granular visibility and policy enforcement over web activity. For teams managing sensitive data and distributed workforces, adopting browser-focused security closes a key gap in the modern security architecture.