Best Secure Remote Access Providers: Top 5 Solutions in 2025

What Are Secure Remote Access Providers?
Top providers of secure remote access offer features like isolation between work and personal data on endpoints, end-to-end encryption, multi-factor authentication (MFA), Zero Trust access controls, session auditing, and compliance logging. When choosing a provider, consider factors such as your business needs, the level of security required, budget, and whether you need features like cross-platform compatibility or advanced reporting.
Key features to look for include:
- Isolation between work and personal data on endpoints: In Bring Your Own Device (BYOD) environments, users connect from unmanaged devices, making it critical to strongly separate work and personal data and applications.
- Encryption: End-to-end encryption to secure data in transit.
- Multi-factor authentication (MFA): Adds an extra layer of security beyond passwords to verify user identity.
- Access controls: Granular control over who can access what resources.
- Auditing and logging: Detailed logs of all remote access activities for compliance and security monitoring.
- Compliance features: Solutions that meet industry-specific and government compliance standards.
- Cross-platform compatibility: Support for various operating systems and mobile devices.
- Zero trust architecture: A security model that ensures all users and devices are verified before being granted access to resources.
Organizations rely on secure remote access not only for productivity but also to comply with regulatory requirements and protect against sophisticated cyber threats. Secure remote access providers must constantly innovate and integrate advanced features such as device posture verification and incident response support to address evolving risks, making them indispensable partners for modern IT operations.
In this article:
Key Features to Look For in a Secure Remote Access Provider
Isolation Between Work and Personal Data on Endpoints
In BYOD environments, endpoint isolation prevents sensitive corporate data from mixing with personal applications, files, and browsing activity. This is usually achieved through secure containers or secure enclaves that run separately from the personal environment. Corporate apps and data remain encrypted and controlled, while personal use of the device is unaffected.
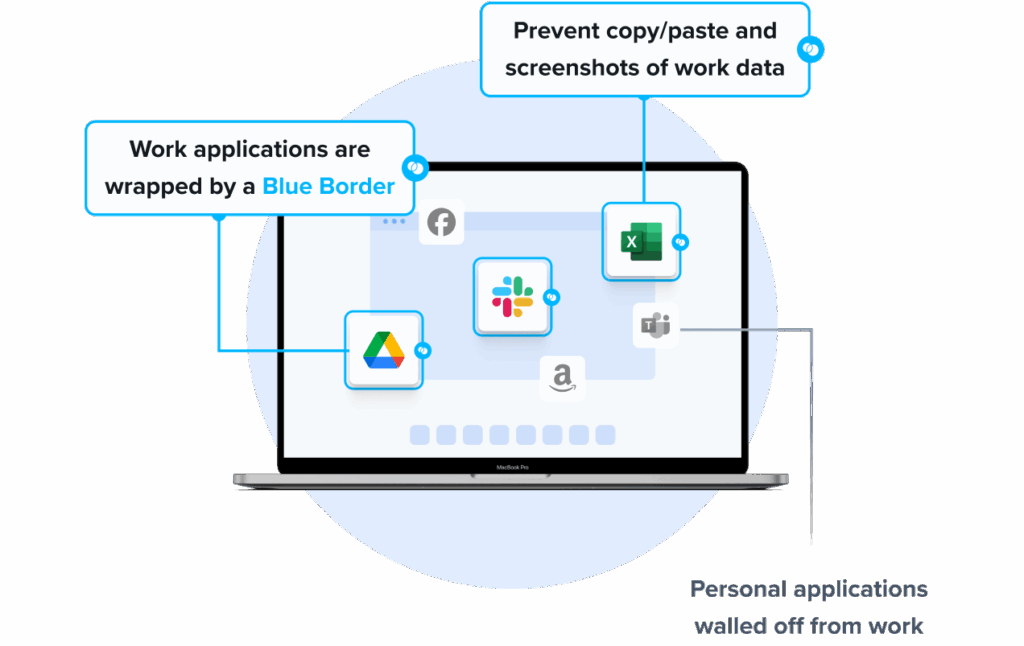
A strong provider should also support policies that restrict copy-paste, file transfer, or screen capture between corporate and personal spaces. This containment ensures that even if the personal environment is compromised, business data remains secure. Isolation features are especially important for regulated industries where data leakage or compliance violations carry significant risks.
Encryption
Secure remote access solutions must use strong encryption to defend data in transit. Industry-standard protocols such as TLS or IPsec ensure that any intercepted traffic is unreadable to attackers. Encrypted tunnels are essential for preventing man-in-the-middle attacks, eavesdropping, and data tampering, especially on unsecured networks like public Wi-Fi.
In addition to strong encryption, providers should offer capabilities like split tunneling, which directs only necessary traffic through the secure tunnel while letting other traffic take a direct path to the internet. This helps optimize bandwidth usage and reduces latency for users, creating a balance between security and performance without putting either at risk.
Strong Authentication and Authorization
Strong authentication and authorization mechanisms are central to any secure remote access solution. Multi-factor authentication (MFA) should be standard, requiring users to verify their identity with a combination of something they know (password), something they have (device or token), or something they are (biometrics).
Centralized access controls, single sign-on (SSO), and role-based permissions further help ensure that users are only granted the minimum level of access required for their work. An ideal provider offers options to integrate existing identity providers and directory services, supporting protocols like SAML, OAuth, and OpenID Connect.
Access Controls
Effective access controls determine what specific resources users can reach once authenticated. Providers should support fine-grained policies that restrict access based on user role, device type, location, or time of day. These controls should be dynamic and adapt to changing conditions, such as blocking access from high-risk geographies or requiring step-up authentication when sensitive applications are requested.
Advanced solutions also integrate with identity and access management (IAM) systems to enforce least-privilege principles consistently. This prevents unauthorized access, limits lateral movement within the network, and reduces the potential impact of compromised accounts.
Auditing and Logging
Detailed auditing and logging provide visibility into remote access activities, which is essential for both security and compliance. Providers should generate logs that include session start and end times, accessed resources, commands executed, and policy enforcement outcomes. These records allow security teams to identify abnormal behavior and investigate incidents effectively.
The best solutions also integrate with security information and event management (SIEM) platforms, enabling centralized analysis and automated alerts. This ensures that suspicious activity is detected quickly and compliance reports can be produced with minimal manual effort.
Compliance
Many industries face strict regulatory requirements, such as HIPAA, PCI DSS, or GDPR. Secure remote access providers must offer features that help organizations demonstrate compliance, such as encryption of sensitive data, retention of access logs, and controls that enforce data sovereignty.
Leading providers often undergo independent audits and provide compliance certifications, giving organizations assurance that the solution meets specific legal and industry standards. Built-in compliance support reduces the burden on internal IT and legal teams while lowering the risk of regulatory penalties.
Cross Platform Compatibility
A secure remote access solution must support diverse environments, as employees use a mix of operating systems and devices. Providers should offer consistent functionality across Windows, macOS, Linux, iOS, and Android, with minimal differences in features or performance.
Support for unmanaged or BYOD endpoints is also important. Solutions that provide browser-based or clientless access ensure that users can securely connect without installing software, enabling flexibility for contractors, partners, and mobile workers.
Zero Trust Architecture
Zero trust architecture eliminates implicit trust and requires continuous verification of users, devices, and sessions. Secure remote access providers implementing zero trust ensure that access decisions are based on multiple contextual signals, including user identity, device health, and network conditions.
Unlike traditional VPNs, zero trust models segment access to specific applications rather than the entire network. This reduces the attack surface, prevents lateral movement, and limits the impact of compromised credentials, aligning with modern cybersecurity best practices.
Enable Remote Workers Without VDI or Issuing Devices
Secure your entire extended workforce without issuing devices or VDI. Keep your organization agile, compliant, and secure.

Notable Secure Remote Access Providers
1. Venn

Venn’s Blue Border™ protects company data and applications on BYOD computers used by contractors and remote employees. Similar to an MDM solution but for laptops – work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Key Features include:
- Seamless MFA integration: Works with Okta, Azure, and Duo for smooth, secure authentication
- Encrypted workspace: Protects all data and applications with robust encryption
- Context-aware access controls: Enforces policies based on user, device, and environment
- Comprehensive session logging: Tracks all activity with full audit visibility
- Unified Zero Trust solution: Combines endpoint protection, remote access, and Zero Trust security
- Faster, scalable alternative: Optimized performance compared with legacy VPNs and VDI
Schedule a demo of Blue Border™
2. NinjaOne Remote

NinjaOne Remote is a secure remote access solution for IT teams that need fast connectivity across Windows, macOS, and mobile devices. It provides one-click connections from the NinjaOne console, allowing technicians to start support sessions without switching tabs or logging into additional tools.
Key features include:
- One-click connections: Launch sessions in 2–3 seconds from within the NinjaOne console, tickets, or device pages
- Strong encryption: Uses x25519+XSalsa20+Poly1305 for secure, logged, and optionally recorded sessions
- Cross-platform support: Remote control for Windows, macOS, Android, and view access for iOS
- Quick connect for BYOD: Securely connect to off-network or unmanaged devices without VPN or installation
- Bandwidth optimization: Auto-adjusts video quality and switches between TCP/UDP for stable sessions

Source: NinjaOne
3. NordLayer

NordLayer provides a secure remote access platform intended to protect remote teams without adding complexity. It enables users to connect to company systems (whether files, servers, or internal applications) via an encrypted tunnel with VPN technology, IP masking, and multi-layer authentication.
Key features include:
- Encrypted access tunnel: Combines VPN, network encryption, and IP masking to secure user connections from any location
- Multi-layered authentication: Supports strong user verification to ensure only authorized access, including multi-factor authentication
- Device-agnostic connectivity: Enables secure access to company resources from desktops, laptops, or mobile devices
- Cloud LAN capabilities: Lets remote users securely access internal resources as if they were on a local network
- Centralized management: Easy-to-use control panel for managing user access, security policies, and device connections at scale
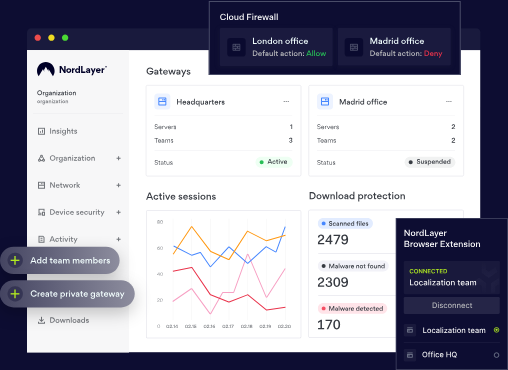
Source: NordLayer
4. Zscaler Private Access

Zscaler Private Access (ZPA) delivers secure and scalable remote access by applying zero trust network access (ZTNA) principles to private applications. Unlike traditional VPNs, ZPA brokers direct, identity-based connections between users and specified apps without exposing the apps to the public internet or placing users on the corporate network.
Key features include:
- Zero trust architecture: Provides user-to-app segmentation with no network access, blocking lateral movement and unauthorized access
- AI-powered app segmentation: Automatically discovers apps and generates policies to minimize risk and accelerate setup
- Private app access without VPN: Replaces VPNs with direct, encrypted connections; no need to expose apps to the public internet
- Clientless remote access: Allows secure RDP, SSH, and VNC access for remote workers and third parties without software installation
- Workload segmentation: Secures app-to-app traffic across multicloud and hybrid environments like AWS and Azure
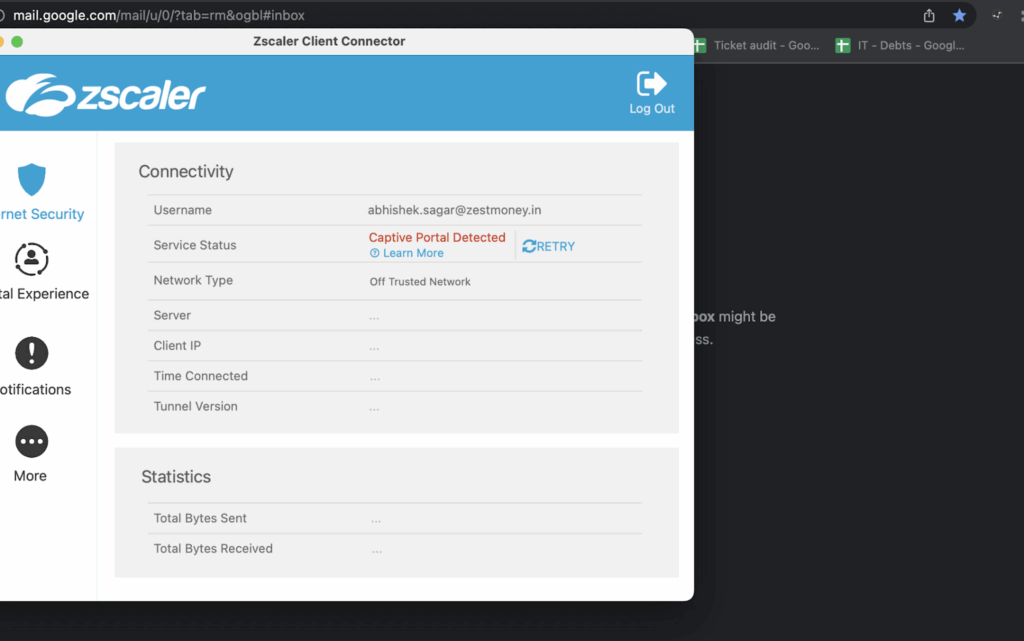
Source: Zscaler
5. Cloudflare Remote Access

Cloudflare Access offers a VPN-free approach to secure remote access using ZTNA principles. It authenticates each request based on identity, device posture, and other context to enforce least-privilege access across environments, including on-premises, cloud, SaaS, and non-web apps.
Key features include:
- VPN-free ZTNA: Replaces legacy VPNs with context-aware, secure access to all internal and cloud-based applications
- Access controls: Verifies identity, device posture, and other contextual signals before granting access to any resource
- Clientless access for third parties: Enables secure access for contractors and partners without requiring software installation
- Developer-focused design: Supports fast, secure access to internal tools and infrastructure for technical teams
- Unified zero trust policies: Centralized policy management across SaaS, self-hosted, and non-web applications
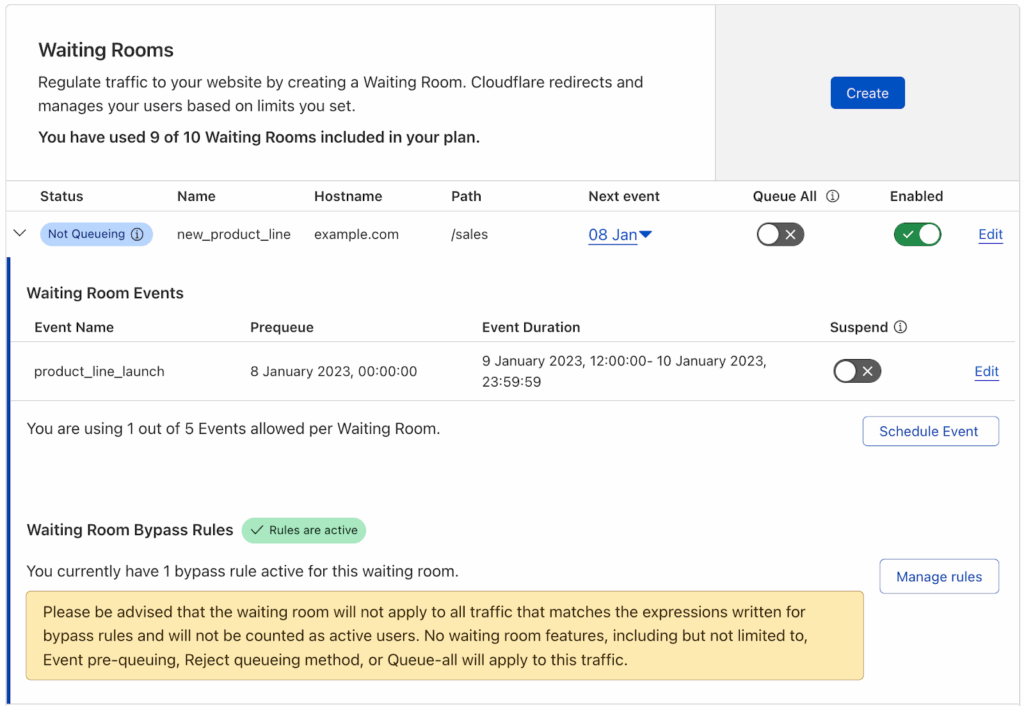
Source: Cloudflare
Conclusion
Secure remote access providers are a cornerstone of modern IT security, ensuring that employees, contractors, and partners can safely connect to organizational resources from any location or device. By combining encryption, strong authentication, granular access controls, and continuous monitoring, these solutions help organizations maintain both productivity and security.