Talon Enterprise Browser: Pros, Cons, and 5 Alternative Solutions

What is Talon Enterprise Browser (Prisma Access Browser)?
Talon Enterprise Browser (Prisma Access Browser) is a protected browser workspace that allows users to securely access company data and resources from any device and any location. With Talon Enterprise Browser, which was also known as TalonWork, companies can prevent data loss for web-based and SaaS apps while defending against malware. By isolating web traffic on the endpoint, the solution provides users with a native experience. With features including file encryption, URL filtering, and a file scanning engine, Talon Enterprise Browser minimizes cyber risk with DLP.
Talon Cyber Security Acquisition by Palo Alto Networks
Talon Enterprise Browser was launched in 2021 by Ofer Ben Noon and Ohad Bobrov. In 2023, Palo Alto Networks, a multinational cybersecurity company with headquarters in California, acquired Talon.
“We are thrilled to welcome Talon to Palo Alto Networks,” said Nikesh Arora, CEO and chairman of Palo Alto Networks. “Most work today occurs via web browsers, often on unmanaged devices, which poses enormous security risks. Through the seamless integration of Talon’s Enterprise Browser with Prisma® SASE, we will be elevating our best-in-class solution that helps provide ironclad security and data protection for all users across all applications and from any device or location.”
Palo Alto Networks Prisma SASE provides a foundation of security for cloud-enabled organizations. Their acquisition of Talon Enterprise Browser was a strategic move to provide customers with a zero trust security solution for enabling security and productivity on unmanaged devices without sacrificing end-user privacy.
Key Features of Prisma Access Browser
In order for a BYOD security solution to truly minimize the attack surface on unmanaged computers, it must include a range of robust security features. So, what are the key features of Prisma Access Browser that make it one of the choice solutions for BYOD security? Let’s discuss.
Phishing & Malware Protection
Prisma Access Browser leverages Palo Alto Networks’ powerful threat detection technologies, including URL Filtering and WildFire, to proactively prevent file-based attacks and block malicious websites. As such, when employees use unmanaged or personal devices, the browser detects and stops phishing attempts, malicious downloads, and suspicious links before harm is done. This built-in protection reduces the risk of credential theft, ransomware, and other common browser threats.
Zero Trust Access
Zero Trust is a key pillar of modern cybersecurity, and Prisma Access Browser embraces it. The browser enforces strong identity verification and conditional access policies for each session. Additionally, access to corporate data and apps is granted based on a combination of user identity, device posture, and context such as location and time. In this way, Prisma Access Browser ensures that even if a device is unmanaged or outside the corporate perimeter, access is tightly controlled, which limits exposure to threats and compromised endpoints.
Data Loss Prevention (DLP)
Another key feature of Prisma Access Browser is its integrated DLP capabilities. It allows organizations to configure policies that prevent sensitive data from being copied, pasted, downloaded, or uploaded through the browser. For example, users might be allowed to view a customer database in a web app but not be allowed to export it to a file or email it to a personal address. These controls are especially useful in industries with regulatory requirements like HIPAA, PCI-DSS, or GDPR.
Chromium-Based Interface
Since Prisma Access Browser is built on Chromium (the same open-source foundation used by Google Chrome), it delivers a familiar, intuitive experience to end users. Users can navigate as they normally would and even install Chrome extensions, which reduces the learning curve and adoption friction. At the same time, companies using Prisma Access Browser benefit from the additional security enhancements, creating an important balance between security and usability that’s vital for remote and hybrid work environments.
Cross-Platform Support
Regardless of whether employees are on Windows, macOS, iOS, or Android, Prisma Access Browser can support consistent policy enforcement and protection across devices. In today’s work-from-anywhere world, where users may switch between laptops, phones, and tablets throughout the day, this is crucial. Companies don’t have to worry about security gaps just because someone logs in from a different device because policies don’t just follow the endpoint, but the user themselves.
Advanced Threat Intelligence
The Talon Enterprise Browser (Prisma Access Browser) integrates with Palo Alto’s global threat intelligence network, helping it continuously adapt to new threats. Pulling from real-time data and machine learning models allows the browser to detect suspicious behavior, malicious payloads, and evolving attack vectors as they appear. IT teams benefit from enterprise-grade protection without having to manually update threat databases or rely on outdated blocklists. As threats evolve, Prisma Access Browser evolves with them, providing proactive protection backed by one of the industry’s most respected security research teams.
Key Limitations of Prisma Access Browser
When it comes to limitations of the Prisma Access Browser, users cite a few.
- Chromium Lock-in: The browser’s reliance on Chromium may limit support for alternative engines or unique browser features.
- Learning Curve & Deployment Complexity: Though user-friendly, configuring policies and scaling across global fleets takes time and skilled administrators.
- Residual Browser Risk: Even hardened, browsers remain attack targets, especially via zero-day exploits.
- Licensing Overhead: SASE licensing can be costly; complimentary offers are limited to select customers.
- Browser-Only Workflows: The solution constricts users to browser-only workflows, which can be problematic for any worker that utilizes locally-installed apps like SAP, CAD, dev tools, and more.
Notable Alternatives for Talon Enterprise Browser
Talon Enterprise Browser is a strong solution for securing browser activity on unmanaged laptops, but there are other excellent options for BYOD security.

1. Venn
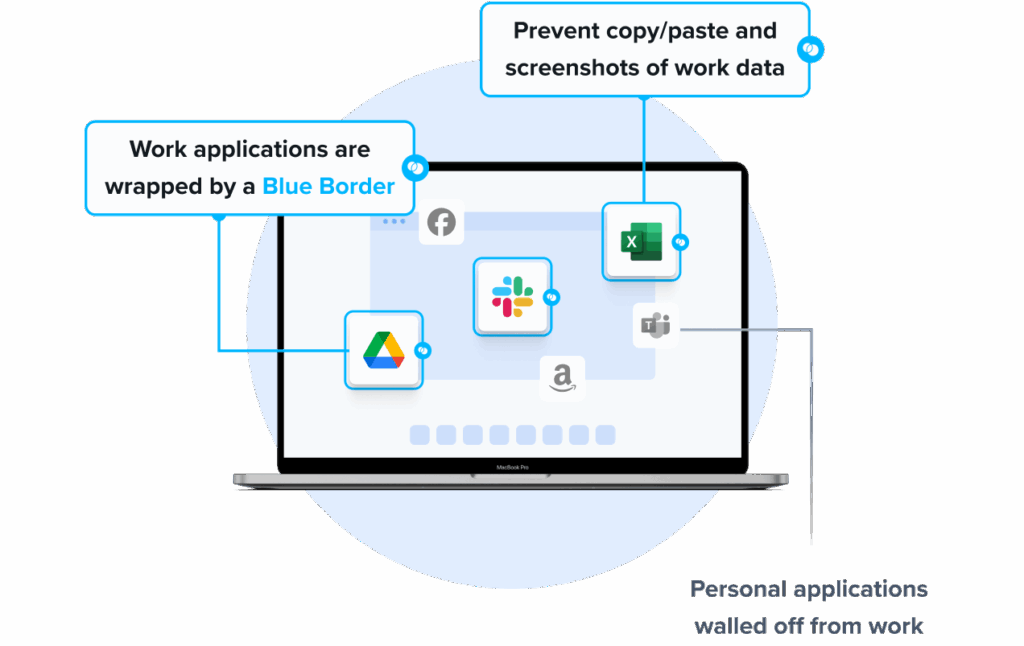
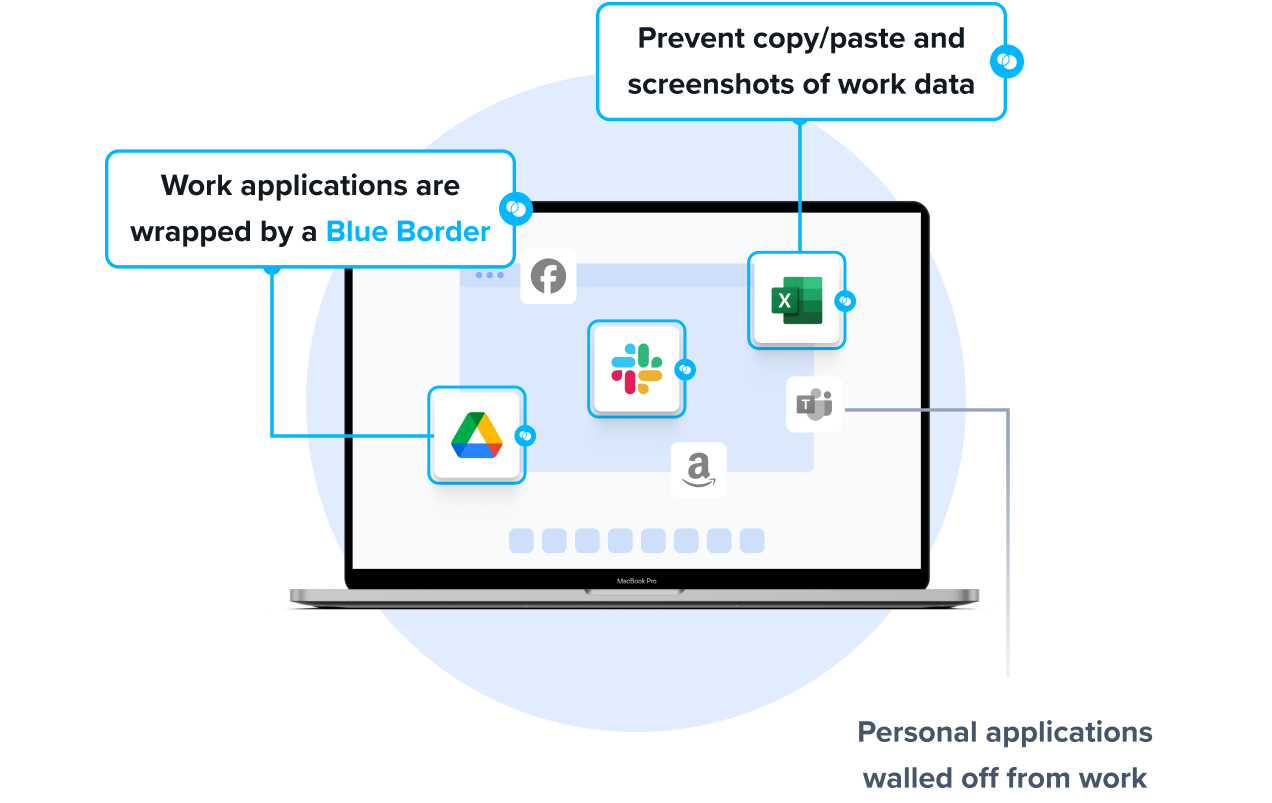
Venn is the leading alternative to Talon Enterprise Browser for organizations that need to secure company data on unmanaged or BYOD computers without forcing users into browser-only workflows. Venn protects both browser-based and locally installed apps within a company-controlled Secure Enclave on the user’s device, delivering native performance without lag or latency. Unlike Talon, which restricts users to the browser, Venn runs apps locally on the endpoint while isolating them from personal activity. Blue Border™ visually distinguishes work from personal use, helping users stay productive while ensuring IT maintains control over business activity. Venn supports turnkey compliance with HIPAA, PCI, SOC, SEC, and FINRA, making it ideal for regulated industries with remote or contract-based workforces.
Features
- Secure Enclave technology encrypts and isolates work data on personal devices
- Local execution of business apps with no latency or lag
- Visual separation via Blue Border to distinguish work vs. personal sessions
- Supports turnkey compliance with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more
- Granular restrictions on copy/paste, download, upload, screenshots, watermarks, and DLP
Secure Browser-Based and Locally Installed Apps. Secure BYOD Access
Schedule a demo to discover how Venn provides a cost-effective VDI and Enterprise Browser alternative that is simpler to manage, faster to deploy, more comprehensive in app coverage, and loved by end users.
2. Island Enterprise Browser

Island Enterprise Browser is also a Chromium-based browser that provides strong isolation and data containment between tabs. Island is well-suited for organizations that need tight controls across unmanaged devices in regulated environments, and it’s tailored for heavily regulated verticals needing detached browsing environments.
Features
- Conditional access policies evaluate identity, device, location, and network within the browser
- Implement restrictions on copy/paste, download, upload, screenshots, watermarks, and DLP
- Built-in device posture assessment integrated into policy decisions
- Transparency and governance for unmanaged use cases
3. Citrix Enterprise Browser
Part of the Citrix Workspace ecosystem, Citrix Enterprise Browser is a Chromium-based, locally installed browser designed for secure access to web and SaaS apps. It encrypts browser data, applies zero-trust policies, and supports remote browser isolation.
Features
- Launches internal and SaaS apps without VPN, inside secure sandboxed browser sessions
- Encrypts passwords, cache, history, cookies, autofill, bookmarks and settings
- Restricts printing, keylogging, screen capture, clipboard, file transfers, watermarks, and personal data masking
- Central policy control: browser management, extension enforcement, bookmarks push, web filtering configured centrally
4. SURF Security
SURF Security delivers a zero‑trust, enterprise browser that features sandboxing, proactive phishing detection, and comprehensive web content filtering. Through integration with tools like Okta, it supports SSO with session kill/logout features when risk policies trigger. It’s a good choice for teams seeking zero-trust enforcement in a familiar UI.
Features
- Zero‑trust browser architecture built from zero, replacing or augmenting consumer browsers
- Proactive threat detection and phishing prevention baked into the browser core
- One-click DLP enforcement controls (copy, paste, print, screenshot rules, data quarantine)
- Integration with identity systems (e.g., Okta) enabling universal logout and session kill on risk
5. LayerX
LayerX takes a different approach. It’s not a standalone browser, but an agentless extension that secures existing browsers like Chrome/Edge. It offers real-time monitoring and risk analysis of web sessions, blocking phishing, malicious extensions, and risky uploads/downloads. It’s ideal for organizations that prefer to stay within mainstream browsers while layering on strong security without heavy infrastructure.
Features
- Continuously monitors all browsing events for anomalies and threats in real time
- Visibility and risk classification of all installed browser extensions; blocks the dangerous ones adaptively
- AI‑powered web object scanning to detect and prevent phishing, credential theft, and malicious scripts
- Identity threat protection: controls credential storage, shared account behavior, and enforces granular rules without disrupting UX
Conclusion
Talon Enterprise Browser (now Prisma Access Browser) is a good option for organizations looking to secure browser-based activity on unmanaged or BYOD devices. It offers a robust set of security features, including phishing protection, DLP, and Zero Trust access, that help reduce risk. But like any solution, it comes with trade-offs, particularly for teams that rely on locally-installed apps or want more deployment flexibility.
Fortunately, a growing number of alternatives offer different approaches to BYOD security. From full-featured platforms like Venn that secure both local and web-based apps, to lightweight browser extensions like LayerX, companies have more options than ever to match their specific needs. Whether browser-based security is the right fit or not, the most important thing is finding a solution that balances user experience, data protection, and operational efficiency in today’s complex hybrid work environments.
More Blogs