Best DaaS Providers and Alternatives: Top 7 in 2026

What Are Desktop-as-a-Service (DaaS) Providers?
Desktop-as-a-Service (DaaS) providers host virtual desktops and applications in the cloud, allowing users to access them from various internet-connected devices. It is offered as a scalable, pay-as-you-go service. Major DaaS providers include Citrix and VMware (now Omnissa).
DaaS providers offer:
- Access from anywhere: Users can connect to their virtual desktops and applications from various devices like laptops, tablets, and smartphones through a web browser or a secure app.
- Central management: Providers handle the underlying infrastructure, simplifying IT operations and allowing IT teams to focus on more strategic tasks.
- Scalability: DaaS platforms are highly scalable, enabling organizations to easily adjust resources and user counts to meet changing business demands.
- Security: DaaS solutions often provide improved security features, with control and data layers isolated to ensure sensitive information remains secure.
While DaaS centralizes desktop delivery, it introduces persistent issues related to cost, complexity, and user experience. Continuous dependency on network quality results in lag and poor responsiveness, especially for users working over slow or unstable connections. Costs can escalate quickly due to recurring subscription fees, data transfer charges, and per-user licensing.
Looking for a DaaS alternative?
Unlock best practices for securing remote access on unmanaged laptops – without any remote hosting or latency.

In this article:
What DaaS Providers Offer
Access from Anywhere
DaaS allows users to reach their virtual desktops from any internet-connected device. However, this access depends heavily on consistent network performance. High latency, packet loss, or limited bandwidth can severely degrade responsiveness, causing slow screen refresh rates and lagging inputs.
Users in remote or mobile environments frequently experience unstable sessions or disconnections. Rather than improving flexibility, this reliance on stable connectivity often restricts usability outside controlled network conditions.
Central Management
With DaaS, administrators control desktops, policies, and updates through a central console, but this centralization also adds operational overhead. Each layer (hypervisors, brokers, storage, and network routing must be maintained and tuned for performance.
Troubleshooting slowdowns or connection failures is complex, as issues can stem from multiple interdependent systems. Updates to base images or policies can impact thousands of sessions, often requiring planned downtime or reconfiguration.
Scalability
While DaaS claims elastic scalability, real-world scaling introduces cost and resource challenges. Adding users increases compute, storage, and licensing expenses. Scaling down doesn’t always yield immediate savings, as providers often bill based on reserved capacity or minimum usage commitments.
Rapid change in workforce size can make DaaS cost-inefficient, particularly for organizations with temporary or contract-based workers.
Flexibility and Choice
DaaS supports multiple desktop configurations and operating systems, but customization can lead to inconsistencies and management overhead. Each variation (different OS versions, application stacks, or policy sets) requires separate templates and maintenance.
Compatibility issues between client devices and virtualized applications can also cause degraded performance or limited functionality, particularly for multimedia or graphics-heavy workloads.
Security
Although DaaS centralizes data storage, it doesn’t eliminate security challenges. The expanded attack surface includes the connection broker, session manager, and underlying cloud infrastructure. Misconfigurations, weak authentication policies, or vulnerabilities in third-party integrations can expose sensitive data.
Because all data flows through remote sessions, visibility and control depend entirely on the provider’s monitoring tools. This creates blind spots for internal security teams and increases reliance on external vendors for compliance and incident response.
Is DaaS the Right Choice for a BYOD Environment?
While DaaS is still commonly used by organizations, it is not well-suited for BYOD environments. It assumes full control over the user session, but in BYOD scenarios, the endpoint is unmanaged and unpredictable. DaaS relies on stable, high-performance network connections and often requires agents, clients, or browser-based sessions that may not work consistently across personal devices. This results in poor user experience, frequent technical issues, and increased IT support demand.
Security is also a concern. While DaaS centralizes desktops in the cloud, it still depends on secure connections from potentially compromised or unpatched personal devices. Without full control over the endpoint, DaaS can’t effectively enforce isolation, monitor activity, or prevent data leakage. These limitations make it a poor fit for modern, flexible work models that rely on personal devices and varied access conditions.
Notable DaaS Alternatives
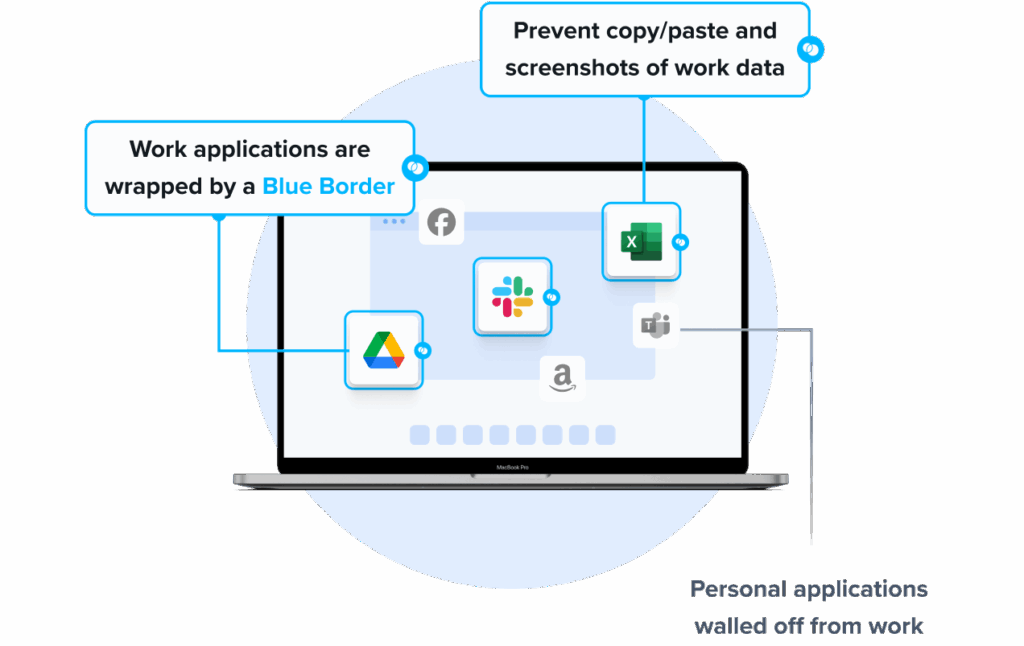
1. Venn’s Blue Border

Unlike DaaS, Venn takes a fundamentally different approach to securing remote and BYOD workforces. Instead of hosting desktops in the cloud, Venn secures company data and applications locally on unmanaged computers used by contractors and remote employees.
Similar to an MDM solution but for laptops, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Unlike DaaS, Venn keeps users working locally on natively installed applications without latency – all while extending corporate firewall protection to business activity only.
Key features include:
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
2. Zscaler Zero Trust Exchange Platform

Zscaler Zero Trust Exchange is a cloud-native platform that brokers least-privileged, one-to-one connections between users and applications. Its proxy architecture performs full TLS/SSL inspection, hides private apps from the internet, prevents lateral movement, and applies data protection with AI/ML-driven controls.
Key features include:
- Proxy-based architecture: Brokers one-to-one connections between users and applications using identity, context, and policy, enabling full TLS inspection without exposing apps to the internet.
- Minimize attack surface: Hides private applications behind the exchange, removing inbound connectivity and unsolicited discovery to reduce exposure and scanning risk.
- Prevent compromise: Inspects traffic, including encrypted sessions, to block threats across internet, SaaS, and private application access.
- Eliminate lateral movement: Connects authorized entities directly to specific applications rather than networks, limiting reachable surfaces and preventing traversal inside data center or cloud environments.
- Data protection and AI: Identifies and protects sensitive data in motion, at rest, and in use, leveraging AI/ML for classification, policy enforcement, and operational automation.
Source: Zscaler
3. Prisma Access

Prisma Access is a cloud-delivered security service that protects users, applications, data, and devices everywhere. It unifies ZTNA, secure web gateway, CASB, FWaaS, and remote browser isolation, supported by high-availability SLAs, native acceleration, and an access agent for consistent connectivity and policy enforcement.
Key features include:
- Unified cloud-delivered security: Delivers ZTNA, secure web gateway, CASB, firewall as a service, and remote browser isolation as a single, cloud-operated service.
- Least-privileged access: Provides zero trust access to applications, eliminating implicit trust and reducing attack surface compared to traditional VPN-based remote connectivity models.
- Operational resilience and experience: Backed by a 99.999% uptime SLA and native app acceleration, with security processing and SaaS performance service level targets.
- Data visibility and control: Provides application visibility with inline and API-based controls, contextual policies, and SaaS security posture management to protect sensitive data.
- Access agent and integration: Offers a next-generation access agent for SASE and NGFW deployments, supporting consistent connectivity and policy enforcement across users and devices.
Source: Palo Alto Networks
Notable DaaS Providers
1. Citrix DaaS

Citrix DaaS is a cloud-oriented desktop and application virtualization service that enables organizations to securely deliver virtual apps and desktops to devices from any location. Designed for hybrid and multi-cloud environments, it supports deployment across public cloud providers like Azure, AWS, and Google Cloud, as well as on-premises hypervisors.
Key features include:
- Hybrid and multi-cloud support: Manage virtual apps and desktops across cloud and on-premises environments using Azure, AWS, Google Cloud, Hyper-V, and VMware.
- Citrix-managed infrastructure: Citrix handles components like Delivery Controllers, licensing, monitoring services, and databases.
- Flexible delivery options: Supports VDI and session-based desktops across Windows and Linux; delivery protocols include HDX for optimized performance.
- Studio Console: Web-based interface for deployment lifecycle management: create machine catalogs, delivery groups, and configure resource policies.
- Cloud Connectors: Provide secure communication between Citrix Cloud and on-prem or cloud-hosted workloads; automatically maintained by Citrix.
Source: Citrix
2. Omnissa Horizon

Omnissa Horizon, formerly known as VMware Horizon, is a commercial desktop and application virtualization platform that delivers virtual desktops to users through VMware’s infrastructure. It enables organizations to run Windows or Linux desktops in virtual machines hosted on VMware ESXi hypervisors, centrally managed via vCenter Server.
Key features include:
- Virtualization: Includes vSphere Hypervisor, vCenter Server, View Manager, and other integrated tools for desktop virtualization.
- Licensing options: Offers Enterprise and Premier editions, with options for features like application virtualization (ThinApp), profile management (Persona), and antivirus offloading (vShield Endpoint).
- Multi-protocol support: Supports VMware Blast Extreme, RDP, and PCoIP for desktop delivery across varying network conditions.
- Cross-platform client access: Horizon Client is available on Windows, macOS, Linux, iOS, Android, and ChromeOS, with web-based access via HTML5.
- Centralized management: Allows IT teams to manage desktops, applications, and user policies from a single interface.
Source: Omnissa
3. Tehama

Tehama is an enterprise desktop-as-a-service (DaaS) platform for secure, compliant, and scalable remote work. Unlike traditional DaaS or VDI models, Tehama does not require admins to manage endpoint devices. It provides cloud-based virtual desktops within isolated workrooms.
Key features include:
- Built-in compliance: SOC 2 Type II compliance controls with regular audits and penetration testing; access, policy changes, and actions are logged for audit-readiness.
- Secure virtual workrooms: Each Workroom includes network isolation, encryption, and file and credential vaults for secure collaboration.
- Contextual forensic auditing: Actions in a Workroom are logged and recorded, creating a searchable activity stream for auditors, investigators, or internal governance teams.
- Global provisioning: Deploy 1 to 10,000 secure desktops across geographic locations, with control over session durations and access policies.
- Dynamic credential management: Secrets vaults support temporary credentials, password expiration, obfuscation, and firewall enforcement.
Source: Tehama
4. Apporto

Apporto is a fully managed desktop-as-a-service (DaaS) platform. Delivered through the browser, it reduces the infrastructure and administrative burdens typically associated with virtual desktop deployments. It manages compute, storage, networking, security, and support, so IT teams can focus on strategic priorities instead of desktop operations.
Key features include:
- Fully managed infrastructure: Handles cloud operations, scaling, patching, and cost optimization, no third-party tools or Azure expertise required.
- Browser-based access: Users can launch desktops from their device, without VPNs or client installations.
- Zero trust security model: Antivirus, patching, automated backups, and compliance controls help reduce risk and simplify audits.
- AI-powered virtual assistant (Portia): Integrated support bot offers natural-language assistance, resolving common issues and reducing IT support workload.
- Monitoring & analytics: Telemetry identifies and resolves performance issues before they affect users.
Source: Apporto
Related content: Read our guide to DaaS solutions (coming soon)
Should You Choose a DaaS Provider or Alternative in a Modern BYOD Environment?
When considering whether to adopt DaaS or pursue an alternative model, organizations should evaluate the following:
- Network dependency and latency: DaaS requires a stable, low-latency connection for basic usability. Performance suffers in mobile, rural, or variable bandwidth conditions.
- Total cost of ownership: Subscription fees, per-user licensing, compute/storage charges, and management overhead quickly add up, especially with persistent desktops or complex image management.
- BYOD friction: DaaS requires client software or browser-based sessions, which can feel intrusive or underperform on personal devices, discouraging adoption.
- Operational complexity: Managing templates, updates, profiles, and access policies across a cloud-hosted desktop fleet often requires specialized skills and continuous tuning.
- Security control gaps: Although desktops are centralized, securing access endpoints, integrations, and session data remains difficult, especially without full control over user devices.
- Scalability trade-offs: Scaling DaaS often leads to higher fixed costs and infrastructure commitments, with limited short-term flexibility or cost recovery when user counts drop.
Related content: Read our guide to BYOD security
Conclusion
DaaS was designed to replicate the traditional desktop environment in the cloud, but this legacy model doesn’t align with how people work today. It creates friction for BYOD users, introduces latency and complexity, and generates recurring costs that are hard to justify at scale. Organizations looking for a sustainable, secure solution should move away from DaaS and toward alternatives like Venn. These modern platforms deliver secure, policy-controlled access to corporate resources without the burden of virtualizing entire desktops.