Top 7 DaaS Solutions and Alternatives in 2026

What Are Desktop-as-a-Service (DaaS) Solutions?
Desktop-as-a-Service (DaaS) delivers virtual desktops from a cloud provider’s infrastructure to user devices via the internet. All computing (processing, storage, and application execution) occurs in a remote data center, not on the user’s device. Users access these desktops using remote display protocols like RDP, PCoIP, or HDX.
While DaaS removes the need for local desktop management, it introduces significant downsides. Performance is highly dependent on network stability, often resulting in latency and poor responsiveness. Subscription costs for DaaS can quickly escalate with scale, especially with persistent desktop use.
Managing image templates, access control, and user environments adds operational complexity. DaaS also fails to fully align with modern endpoint diversity, especially in BYOD scenarios where control and compatibility issues persist.
Looking for a DaaS alternative?
Unlock best practices for securing remote access on unmanaged laptops – without any remote hosting or latency.

In this article:
How DaaS Solutions Work
DaaS solutions rely on a cloud infrastructure that hosts virtual machines (VMs), each configured as a desktop environment. These desktops are provisioned, managed, and delivered via a centralized platform typically offered by a DaaS provider. Users connect to their virtual desktops over the internet using a remote display protocol such as Microsoft RDP, Citrix HDX, or VMware Blast.
The provider manages the underlying hardware, hypervisors, networking, storage, and orchestration. Administrators use a management console to configure user access, assign resources, and apply security policies. DaaS platforms often integrate with identity providers to enforce authentication and role-based access controls.
When a user logs in, the DaaS service spins up a virtual desktop instance, either from a persistent image (retaining user data and settings) or a non-persistent image (resetting after each session). Sessions are isolated from each other to ensure security and performance.
Most DaaS solutions include built-in monitoring, backups, and scaling features. This lets IT teams manage resources dynamically and optimize use of infrastructure.
Is DaaS Suitable for a Modern BYOD Environment?
While DaaS platforms are still widely used by organizations, they are not well-suited for modern BYOD environments. They rely on centralized control of virtual desktops and require network-dependent access through remote display protocols. This model assumes a controlled, stable connection and consistent device compatibility, conditions rarely met in BYOD scenarios.
In addition, DaaS does not address user privacy concerns. Employees using personal devices may be reluctant to install agents or remote access clients. Performance can also vary widely based on local device specs, network bandwidth, and geographic distance from the cloud infrastructure. These limitations make DaaS a poor fit for BYOD, where flexibility, usability, and non-invasive control are essential.
Notable DaaS Alternatives
1. Venn’s Blue Border

Unlike DaaS, Venn takes a fundamentally different approach to securing remote and BYOD workforces. Instead of hosting desktops in the cloud, Venn secures company data and applications locally on unmanaged computers used by contractors and remote employees.
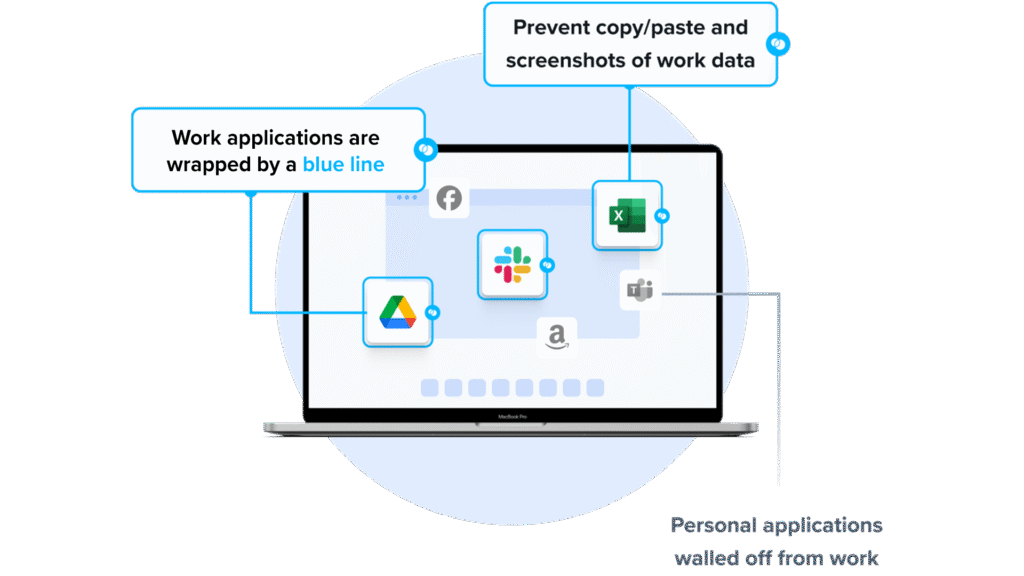
Similar to an MDM solution but for laptops, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Unlike DaaS, Venn keeps users working locally on natively installed applications without latency – all while extending corporate firewall protection to business activity only.
Key features include:
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
2. Kasm Workspaces

Kasm Workspaces is a browser-based workspace streaming platform that delivers desktops, applications, and cloud browsers to any device. It supports cloud desktops, web isolation, remote access, and app streaming, including Windows and Linux workspaces, optional GPU acceleration, developer APIs, and infrastructure-as-code deployments with Ansible and Terraform.
Key features include:
- Browser-based workspace streaming: Deliver desktops and applications through a web browser, providing device-agnostic access without installing thick clients on endpoints.
- Cloud desktops on demand: Launch secure Windows and Linux desktops in seconds, scaling up or down as needed and supporting remote work from any location.
- Web isolation and research: Use cloud browsers for isolation, web research, and investigations, separating risky activity from local devices to reduce exposure and contamination.
- Multi-OS and GPU support: Stream Windows, Linux, and other operating systems side-by-side, with optional GPU acceleration for graphics-intensive workloads and specialized applications.
- Automation and integrations: Leverage Developer APIs, Ansible and Terraform deployments, and workspace images to customize provisioning and integrate with existing pipelines.
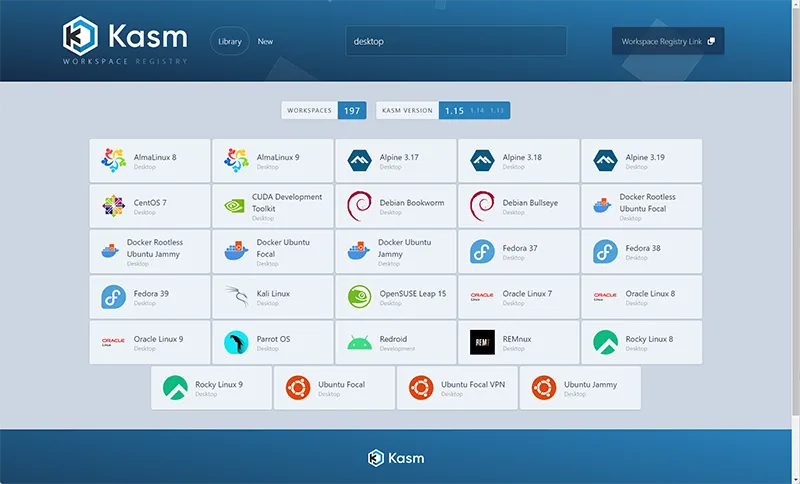
Source: Kasm
3. Parallels RAS

Parallels RAS delivers remote applications and desktops with hybrid deployment options across on-premises, private, and public clouds, including Azure Virtual Desktop and AWS. It provides native and HTML5 clients, single-console administration, MSIX App Attach/App-V, FSLogix, and integrated security controls with TLS 1.3, FIPS 140-2, MFA, and IdP integrations, plus reporting, monitoring, and high-availability load balancing.
Key features include:
- Hybrid deployment flexibility: Deploy on-premises, private or public clouds with Azure and AWS integrations, avoiding platform lock-in and supporting mixed resource locations.
- Client access: Provide native clients for Windows, macOS, Linux, iOS, and Android, plus HTML5 web access for any modern browser and thin endpoints.
- Single-console administration: Manage apps, desktops, images, gateways, load balancing, reporting, and access control from one console with multi-tenant support and dynamic scaling.
- Integrated security controls: Enforce TLS 1.3 with FIPS 140-2 support, built-in MFA and third-party integrations, rule-based access, auditing, and automated certificate management.
- High availability and monitoring: Use built-in high availability load balancing, reporting, and monitoring to maintain service continuity across sites without additional components or consoles.

Source: Parallels
Notable DaaS Solutions
4. Microsoft Azure Virtual Desktop
Azure Virtual Desktop is a cloud-based service that delivers Windows desktops and applications from the Azure cloud. It supports Windows 11, Windows 10, and Windows Server, offering single-session and multi-session options. Organizations can provide desktop environments or publish individual applications, while maintaining centralized management through the Azure portal, CLI, PowerShell, or REST API.
Key features include:
- Support for Windows 11, Windows 10, and Windows Server with single-session or multi-session options
- Ability to publish desktops or individual apps using RemoteApp
- Optimization for Microsoft 365 Apps in multi-user environments
- Support for custom and line-of-business apps, including Win32, MSIX, and Appx formats
- SaaS delivery for external users and replacement for Remote Desktop Services deployments
Source: Microsoft
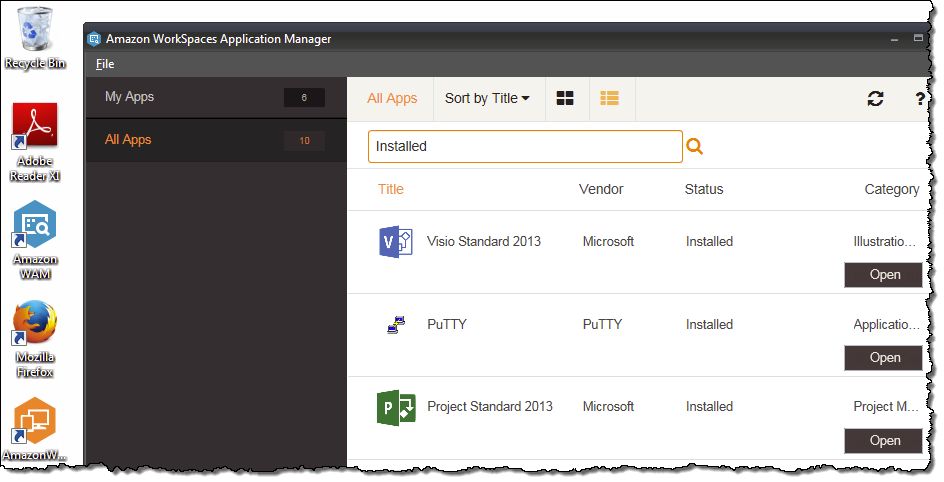
5. Amazon WorkSpaces
Amazon WorkSpaces is a managed desktop virtualization service that provisions cloud-based desktops for users. It supports multiple operating systems, including Windows, Amazon Linux 2, Ubuntu, Rocky Linux, and Red Hat Enterprise Linux. Organizations can choose between persistent desktops for individual use or non-persistent pools for shared access.
Key features include:
- Support for Windows, Amazon Linux 2, Ubuntu, Rocky Linux, and Red Hat Enterprise Linux
- Choice between WorkSpaces Personal (persistent desktops for individual users) and WorkSpaces Pools (non-persistent desktops for shared use)
- Range of hardware and software configurations, with the option to create custom images and bundles
- Integration with Microsoft Entra ID for login and access to Microsoft 365 Apps, plus support for Intune-based management
- Bring your own licenses and applications or purchase software through AWS Marketplace
Source: Amazon
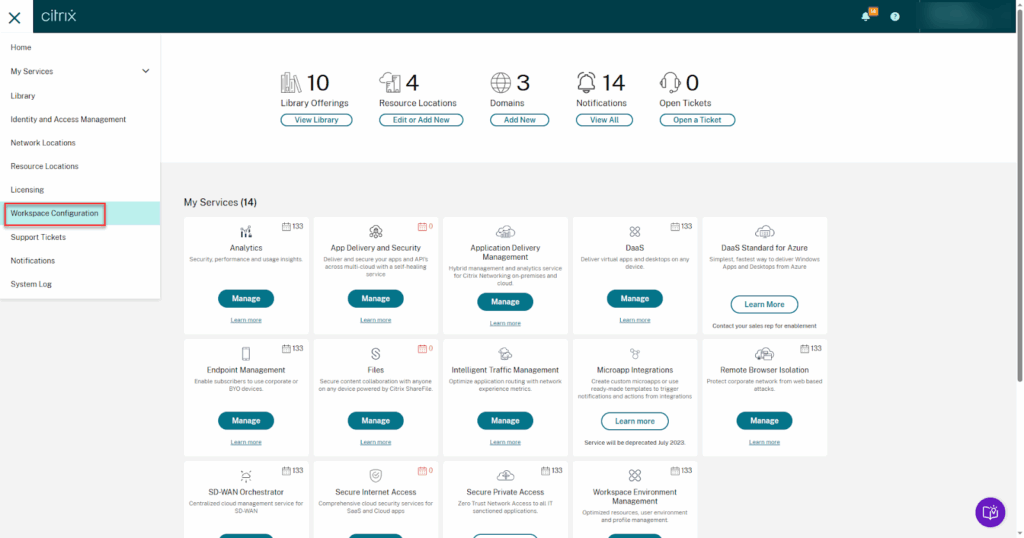
6. Citrix DaaS

Citrix DaaS is a desktop and application virtualization service that lets organizations deliver secure apps and desktops to different devices. It gives IT centralized control over applications, user policies, and security, while offloading much of the setup, maintenance, and upgrades to Citrix.
Key features include:
- Centralized delivery of virtual desktops and applications independent of device OS or interface
- Hybrid and multi-cloud support across Azure, AWS, Google Cloud, and on-premises hypervisors (XenServer, Hyper-V, Nutanix AHV, VMware vSphere)
- Multiple delivery options for persistent or non-persistent desktops, VDI models, and app publishing
- Citrix Managed Azure option for hosting and deployment of Azure workloads
- Cloud-based management of core services, including Delivery Controllers, databases, and licensing
Source: Citrix
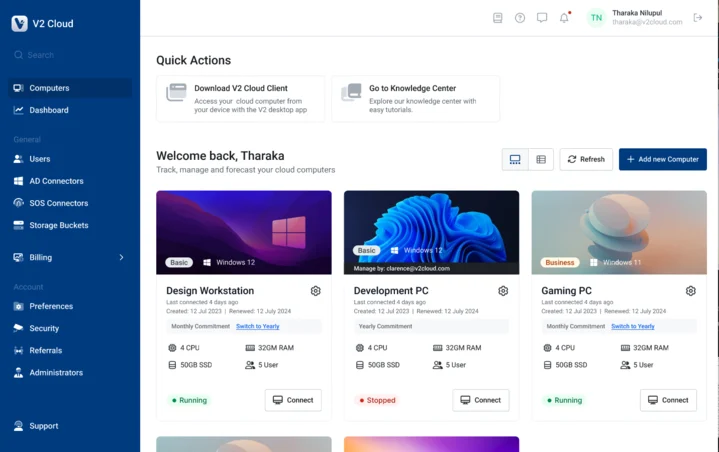
7. V2 Cloud

V2 Cloud is a Desktop-as-a-Service solution to simplify remote desktop delivery for businesses. It provides secure, browser-based access to virtual desktops, helping support remote work, BYOD policies, and collaboration.
Key features include:
- Browser-based remote desktop access, eliminating dependence on specific devices
- Support for Bring Your Own Device (BYOD) to enable flexible work with a focus on security
- Encryption and continuous monitoring to protect sensitive data
- Compliance support for meeting regulatory standards across industries
- Quick setup in four steps: select plan, configure virtual desktop specs, download client, and start using apps
Source: V2 Cloud
Considerations for Choosing Legacy DaaS vs. DaaS Alternatives
Organizations evaluating DaaS must recognize that it carries many of the same limitations as VDI, with added reliance on external infrastructure. Alternatives that isolate work applications and data at the endpoint without replicating full desktops can reduce cost, simplify management, and improve the user experience, especially in BYOD and hybrid work environments.
- Total cost of ownership: DaaS subscriptions, bandwidth usage, licensing, and support stack up quickly. Alternatives reduce overhead by removing the need to host full desktop environments.
- Performance and latency: Remote desktop protocols are sensitive to latency and offer poor performance on slow or unstable connections.
- BYOD compatibility: DaaS often requires software agents or client installs, introducing privacy concerns and reducing user acceptance on personal devices.
- Operational complexity: Provisioning, managing, and maintaining virtual desktops at scale remains labor-intensive and error-prone.
- User experience: Full desktop delivery can be overkill for most users and doesn’t align with modern app-based workflows.
Conclusion
DaaS is a legacy approach to desktop delivery that fails to meet the demands of modern, flexible work environments. It inherits many of the challenges of VDI, such as complexity, cost, and poor performance, while introducing new ones tied to cloud reliance and user friction. Organizations should consider alternatives like Venn, which provide secure, policy-enforced workspaces on any device without replicating the entire desktop environment. This approach better supports BYOD, improves manageability, and eliminates unnecessary infrastructure.
You can book a demo of Venn here.