DLP Software: Types, Key Features, and 10 Solutions to Know in 2025

What Is Data Loss Prevention (DLP) Software?
Data loss prevention (DLP) software is a category of cybersecurity tools that prevent sensitive information from being lost, misused, or accessed by unauthorized users. DLP solutions monitor, detect, and block the movement of critical data across endpoints, networks, storage, and cloud environments. Common examples of data DLP protects include intellectual property, personally identifiable information (PII), financial records, and confidential business documents. By enforcing policies for handling data, DLP helps organizations maintain control over where their data resides and how it is used or shared.
DLP software operates by identifying, monitoring, and managing the flow of sensitive information in real time. This often involves scanning data at rest, data in motion, and data in use, ensuring that confidential content does not leave the organization through email, web uploads, removable media, or cloud services. DLP solutions use pattern matching, content inspection, and contextual analysis to apply rules that prevent unauthorized sharing or accidental exposure. As data protection regulations become more stringent, DLP has become a critical part of enterprise security architectures, reducing the risks associated with insider threats and cyberattacks.
Enforce DLP on Unmanaged Laptops
Learn how to keep sensitive data secure when contractors and remote workers use personal laptops.

In this article:
Benefits of DLP Software
Organizations use DLP software to gain visibility and control over how sensitive data is accessed, transmitted, and stored. Beyond preventing data breaches, DLP helps enforce compliance and supports secure business operations. Key benefits include:
- Regulatory compliance: Helps meet requirements from regulations like GDPR, HIPAA, and PCI-DSS by preventing unauthorized data exposure.
- Insider threat mitigation: Detects and blocks risky actions by employees, whether accidental or malicious, that could lead to data loss.
- Data visibility and control: Provides detailed insight into where sensitive data lives, how it moves, and who accesses it.
- Policy enforcement: Automatically applies rules to govern data handling based on content type, user role, or transmission method.
- Risk reduction: Minimizes the chance of data leaks through common channels like email, file sharing services, and USB devices.
- Incident response support: Enables quick investigation and remediation by logging events and alerting security teams to suspicious behavior.
- Cloud data protection: Extends monitoring and control to cloud platforms and services where data often resides or is shared.
How DLP Software Works
DLP software works by monitoring data at multiple stages: at rest, in use, and in motion across servers, endpoints, networks, and cloud applications.
DLP software typically follows this operational process:
- Uses content inspection techniques such as fingerprinting, pattern matching, and contextual analysis to identify sensitive information like credit card numbers, health records, or proprietary data.
- Once sensitive data is detected, the software enforces security policies tailored to block, quarantine, encrypt, or allow the data transfer based on risk assessment and business rules. This real-time action helps prevent accidental leaks or deliberate exfiltration.
- DLP solutions integrate with IT and security infrastructure, leveraging APIs, agents, and network taps. DLP systems collect logs and telemetry for analysis, alerting security teams when a policy violation occurs.
Advanced solutions employ machine learning to recognize unusual patterns or adapt to new data types. DLP platforms usually include centralized management consoles for configuring policies, conducting investigations, and generating compliance reports.
Main Types of DLP Software Solutions
Endpoint DLP
Endpoint DLP focuses on protecting data on devices such as laptops, desktops, and servers, regardless of their physical location. This type of DLP monitors and controls data transfers involving USB drives, printers, local folders, and other peripheral devices. When users interact with sensitive content on endpoints, the DLP agent enforces security rules in real time, blocking unauthorized sharing, copying, or printing of confidential data. Endpoint DLP is essential for managing risks associated with remote work and bring your own device (BYOD) scenarios, where traditional perimeter defenses are less effective.
Network DLP
Network DLP operates at the network layer, monitoring data as it moves within and outside the organization’s infrastructure. It inspects email, web traffic, file transfers, and other communication channels for sensitive content leaving the network perimeter. By applying predefined or custom policies, network DLP can automatically block, quarantine, or encrypt outbound information, preventing accidental or malicious exfiltration of confidential data. Network DLP solutions frequently integrate with email gateways and proxy servers to enforce protection policies consistently.
Cloud DLP
Cloud DLP solutions protect data stored, processed, and shared in cloud environments like SaaS applications and public or hybrid clouds. They discover, classify, and monitor sensitive information across services such as Microsoft 365, Google Workspace, Salesforce, and other cloud platforms. Cloud DLP leverages APIs and integrations to scan files, emails, and collaboration content for policy violations, triggering automated remediation actions like quarantining documents or alerting administrators when issues are detected.
Storage DLP
Storage DLP focuses on securing data at rest in file servers, databases, data lakes, and backup repositories, often some of the largest concentrations of sensitive information in an organization. Storage DLP tools scan stored files and databases to discover and classify regulated or confidential data, alerting teams when sensitive content is found in improper locations or without adequate protections. The software can encrypt, quarantine, or restrict access to these data stores based on predefined risk and compliance policies.
Key Features and Capabilities of DLP Software
Automated Data Discovery
Automated data discovery is a fundamental capability in modern DLP solutions, enabling organizations to locate sensitive information wherever it resides across endpoints, networks, storage, and cloud platforms. The discovery process uses scanning engines that identify regulated data types, such as credit card numbers, national ID numbers, or health information, by applying signature-based detection, pattern recognition, and contextual analysis. Automated tools reduce the manual effort previously required for audits and significantly improve the speed and coverage of sensitive data identification across large, distributed environments.
As new data is created or imported into enterprise systems, automated discovery routines continuously scan and classify it. This ongoing monitoring ensures that newly added records are promptly evaluated for compliance with security policies, and any sensitive information is flagged for further protection. Automated discovery capabilities also support data inventory and risk assessment tasks, providing security teams with real-time visibility into where their most valuable data assets reside and which repositories need additional controls.
Real-Time Detection and Response
Real-time detection and response is a core DLP feature that enables organizations to intercept and remediate security incidents as they occur. DLP solutions continuously monitor user activity, data movement, and file access, applying policy-based rules to identify suspicious or unauthorized actions instantaneously. When a policy violation is detected, such as a user attempting to email sensitive files to an external recipient, the DLP system can block the action, quarantine the data, or alert security teams immediately. This proactive approach prevents data loss events before they escalate into full breaches.
These real-time mechanisms are vital for minimizing dwell time between compromise and containment, ensuring potential threats are limited in impact and scope. The ability to automate responses, such as auto-encrypting files or revoking access permissions, allows organizations to reduce dependence on manual intervention and maintain compliance with incident response standards. Real-time DLP enhances overall resilience, especially in environments where quick decision-making and rapid response are essential for data security.
AI and ML for Contextual Data Understanding
Artificial intelligence (AI) and machine learning (ML) are increasingly integrated into DLP tools to provide deeper insight into the context and intent behind data movements. These technologies analyze user behavior patterns, communication context, and historical activity to differentiate between legitimate data use and possible exfiltration or misuse. By learning what constitutes normal activity, AI-powered DLP systems can more accurately identify risky behaviors, reduce false positives, and adapt detection models to emerging threats or new data types.
ML-driven DLP also supports advanced data classification, enabling the software to recognize and protect sensitive data types even if they don’t match fixed patterns or predefined rules. For example, machine learning algorithms can discover new types of intellectual property or proprietary documents that may lack explicit identifiers. As organizations handle larger volumes and more varied kinds of information, AI and ML deliver the scalability and flexibility required to maintain effective data protection.
Compliance Mapping
Compliance mapping allows DLP solutions to streamline and automate the alignment of security controls with regulatory requirements, such as GDPR, HIPAA, CCPA, and PCI DSS. With built-in templates and frameworks, DLP software automatically maps sensitive data types, policy rules, and audit logs to specific compliance mandates. This greatly simplifies compliance workflows by ensuring that all critical controls are tracked, monitored, and documented for reporting purposes, reducing the risk of missed obligations during audits.
Furthermore, compliance mapping features often include dashboards and reporting tools that provide instant visibility into current compliance status. Security and audit teams can quickly identify areas of non-compliance and take corrective action, reducing the likelihood of fines and legal penalties. Automated compliance mapping is especially valuable for organizations operating in multiple jurisdictions or highly regulated sectors, where the cost and complexity of manual compliance efforts would otherwise be prohibitive.
Cross-Platform and Multi-Cloud Support
As organizations operate hybrid environments with a mix of on-premises systems and cloud services, cross-platform and multi-cloud support has become a must-have DLP feature. Advanced DLP tools integrate with a wide variety of operating systems, devices, and SaaS platforms, protecting data as it moves between disparate environments. This ensures consistent policy enforcement and monitoring, even as users access and share information across Windows, macOS, Linux, and mobile devices, or work in environments like AWS, Azure, and Google Cloud.
Cross-platform DLP capabilities also simplify management by providing centralized control over policy configuration, incident response, and reporting, regardless of where the protected data lives. Multi-cloud support allows organizations to apply unified DLP rules to files, emails, databases, and collaboration tools in various clouds, reducing the risk of data silos and inconsistent protections. This holistic approach is critical for enterprises with distributed workforces and complex IT landscapes.
Related content: Read our guide to DLP policy
Notable DLP Software and Solutions
1. Venn

Solution category: Endpoint DLP
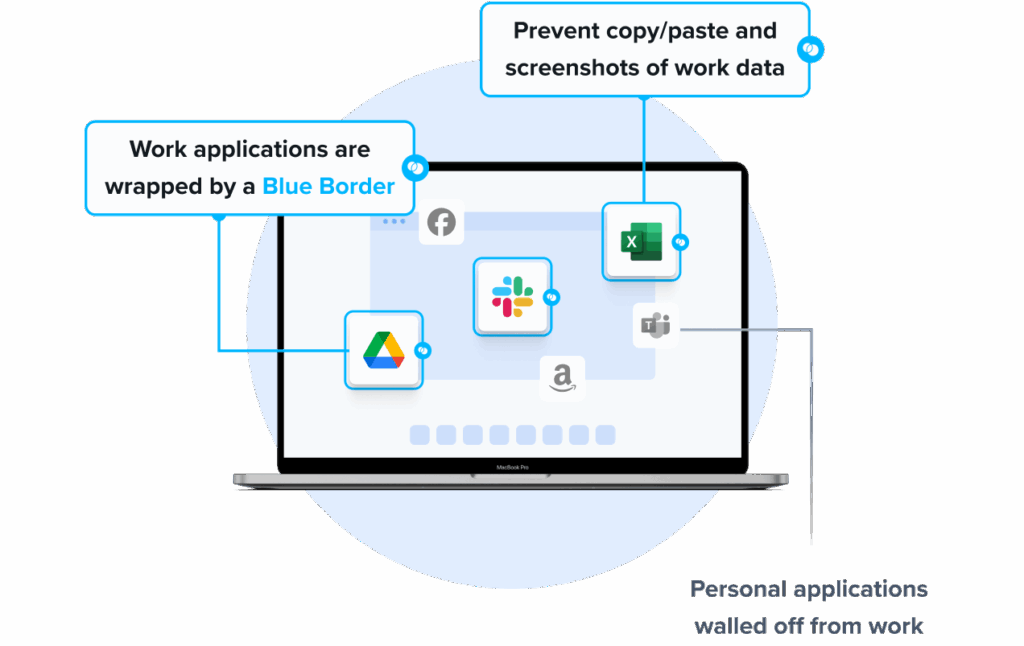
Venn’s Blue Border™ protects company data and applications on BYOD computers used by contractors and remote employees. Similar to an MDM solution but for laptops – work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Inside the Secure Enclave, IT can enforce DLP policies.
Protections include:
- Preventing copy/paste between work and personal apps
- Controlling file downloads and external storage
- Blocking screenshots
- Applying consistent protections to both browser-based and installed applications
With Venn, organizations gain enterprise-grade DLP enforcement on unmanaged devices, while users keep the fast, familiar workflows they expect.
To see Venn in action, book a demo here.
2. Broadcom DLP

Solution category: Enterprise DLP (covers endpoint, network, cloud, and storage DLP)
Broadcom (Symantec) Data Loss Prevention is an enterprise solution to provide scalable protection for sensitive data across endpoints, networks, storage systems, and cloud environments. It uses content-aware detection techniques like exact data matching and sensitive image recognition to locate and protect confidential data wherever it resides or moves.
Key features include:
- Content detection: Uses exact data matching, indexed document matching, described content matching, and OCR to locate sensitive data in files, forms, and images.
- Data coverage: Protects data across endpoints, email, cloud apps (e.g., Office 365, Salesforce), file shares, and databases.
- Unified policy management: Centralizes policy creation and enforcement across all control points: endpoint, network, storage, and cloud.
- Real-time data monitoring: Tracks data downloads, copies, emails, and web activity in real time to detect risky behavior and prevent leaks.
- Automated incident remediation: Supports workflows for blocking, quarantining, encrypting, or rerouting data, including integration with tools like ServiceNow.
Source: Broadcom
3. Forcepoint DLP

Solution category: Enterprise DLP (covers endpoint, network, cloud, and storage DLP)
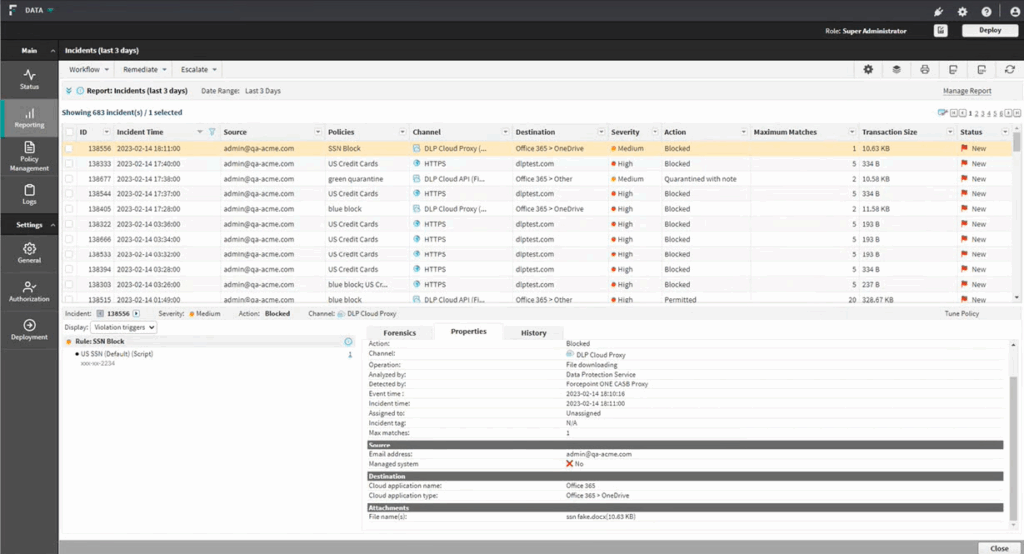
Forcepoint Data Loss Prevention is a unified solution that protects sensitive data wherever it resides: on endpoints, in the cloud, or across network channels. It combines content-aware detection with risk-adaptive protection, allowing organizations to monitor and respond to data risks in real time.
Key features include:
- Unified policy enforcement: Enforces a single set of DLP policies across endpoints, cloud services, web, and email to reduce gaps and simplify management.
- Risk-adaptive protection: Dynamically adjusts policies based on contextual user behavior using 130+ indicators of behavior (IoBs) and integrated user risk analytics.
- Extensive data coverage: Protects data in motion, at rest, and in use across SaaS apps, structured and unstructured data, PST files, and more.
- Out-of-the-box compliance: Offers over 1,700 compliance templates and classifiers to support regulatory mandates across over 80 countries, including for PII and PHI.
- Centralized management console: Provides a single UI for configuring policies, managing incidents, and generating reports across all channels.
Source: Forcepoint
4. Microsoft Purview DLP

Solution category: Cloud DLP
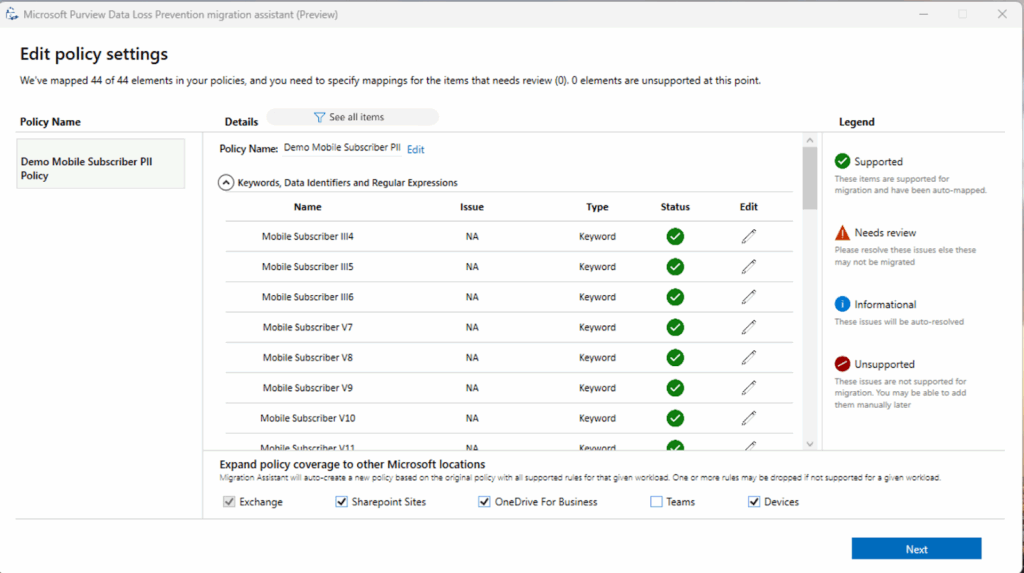
Microsoft Purview Data Loss Prevention is a cloud-native solution that protects sensitive data across the Microsoft ecosystem, including endpoints, Exchange, OneDrive, SharePoint, Teams, and Microsoft 365 Copilot. It combines unified policy management, content-aware detection, and adaptive controls to help organizations enforce data protection without disrupting productivity.
Key features include:
- Integrated ecosystem protection: Applies DLP policies across Microsoft 365 apps and services, such as Teams, SharePoint, OneDrive, Exchange, and Copilot, for consistent data protection.
- Centralized policy management: Manage, configure, and deploy DLP policies from a single compliance portal, reducing administrative overhead and simplifying oversight.
- Cloud-native delivery: Deployed and managed in the cloud, enabling fast setup, easy scalability, and minimal infrastructure requirements.
- Adaptive controls with machine learning: Uses behavioral analytics and classification to dynamically adjust enforcement policies, balancing protection and user productivity.
- Unified alerting and remediation: Provides centralized incident detection, alerting, and response workflows for quicker remediation and audit readiness.
Source: Microsoft
5. Trellix DLP

Solution category: Enterprise DLP (covers endpoint, network, cloud, and storage DLP)
Trellix Data Loss Prevention provides protection for sensitive data across endpoints, networks, storage, and cloud environments. Designed to address insider threats and compliance mandates, Trellix DLP combines real-time visibility, automated policy enforcement, and user coaching to reduce the risk of data exfiltration.
Key features include:
- Data coverage: Protects data across endpoints, networks, storage, and cloud by detecting and preventing unauthorized sharing or exfiltration.
- Unified policy management: Centralized console for deploying policies, tracking incidents, and generating compliance reports across all DLP components.
- Real-time monitoring and response: Detects sensitive data movements in real time and applies actions such as blocking, quarantining, or alerting based on policy rules.
- User coaching and justification prompts: Notifies end users of policy violations and allows them to justify actions, improving awareness and reducing accidental data loss.
- Out-of-the-box compliance support: Includes predefined rules and reporting tools aligned with major regulations like GDPR, HIPAA, and PCI-DSS.
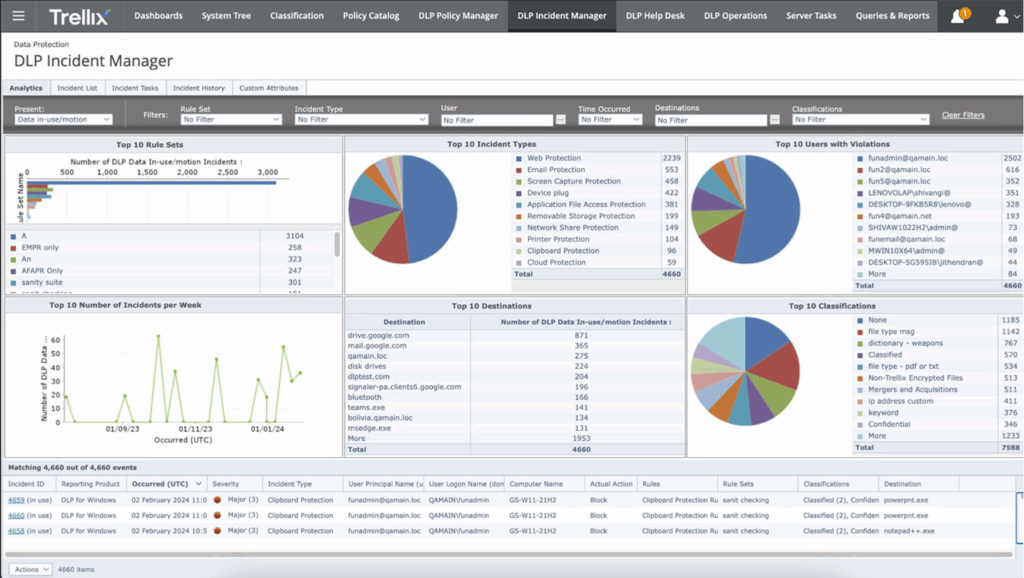
Source: Trellix
6. Digital Guardian DLP

Solution category: Enterprise DLP (covers endpoint, network, cloud, and storage DLP)
Digital Guardian Data Loss Prevention offers a SaaS-based platform to secure sensitive data across hybrid, cloud, and on-premises environments. It delivers data protection from discovery and classification to real-time monitoring and blocking, helping organizations understand data flows and stop threats before they result in loss.
Key features include:
- SaaS-based deployment: Rapidly deployable, cloud-native architecture that enables immediate visibility into sensitive data across endpoints, networks, and cloud applications.
- Comprehensive data protection: Covers the full data lifecycle with capabilities for discovery, classification, monitoring, alerting, and blocking of sensitive data activity.
- Managed DLP services: Offers expert-led hosting and administration to reduce the burden on internal cybersecurity teams while maintaining full data protection capabilities.
- Cloud and SaaS protection: Extends security to cloud apps and infrastructure with integrations such as CASB, DSPM, ZTNA, and SWG for full cloud visibility and control.
- Zero trust collaboration: Encrypts and controls access to shared files, enabling secure collaboration both internally and with external partners.
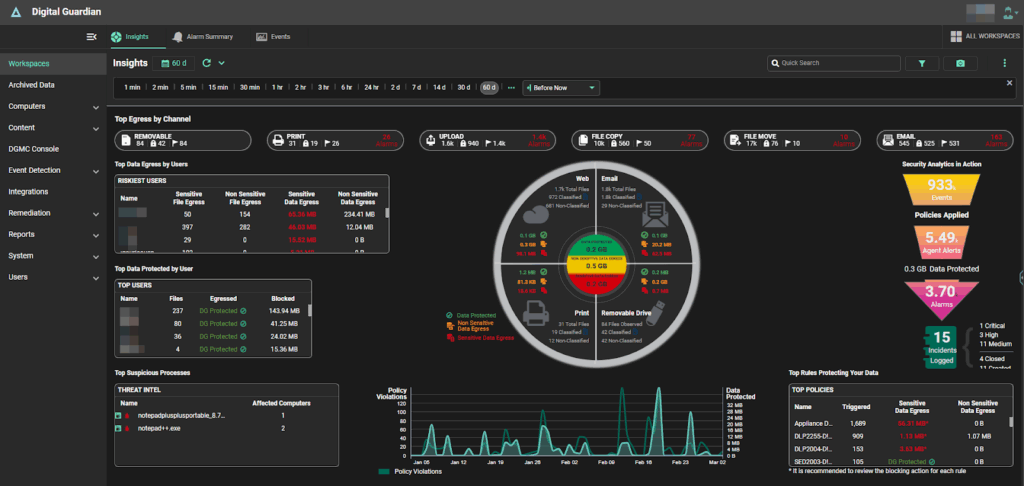
Source: Digital Guardian
7. Teramind DLP

Solution category: Endpoint DLP (with behavioral analytics and partial network DLP functions)
Teramind Data Loss Prevention takes a behavioral approach to protecting sensitive data, focusing on user actions and intent rather than static rules alone. Designed to secure data in motion across endpoints, applications, and networks, Teramind combines context-aware monitoring with real-time intervention and forensic-ready logging.
Key features include:
- Behavioral analytics engine: Builds user behavior baselines and detects deviations to uncover sophisticated data exfiltration attempts that traditional DLP tools might miss.
- Multi-channel monitoring: Tracks file activity, clipboard usage, messaging apps, email, web uploads, and cloud transfers across endpoints, networks, and applications.
- Real-time intervention: Automatically blocks, alerts, or terminates sessions based on configurable risk thresholds; delivers in-the-moment user guidance to reinforce policies.
- Content Analysis engine: Uses pattern matching, classification, and OCR to detect sensitive content, including in screenshots or non-searchable documents.
- Forensic-ready incident response: Captures logs, screen recordings, and event timelines to support investigations and audit readiness.
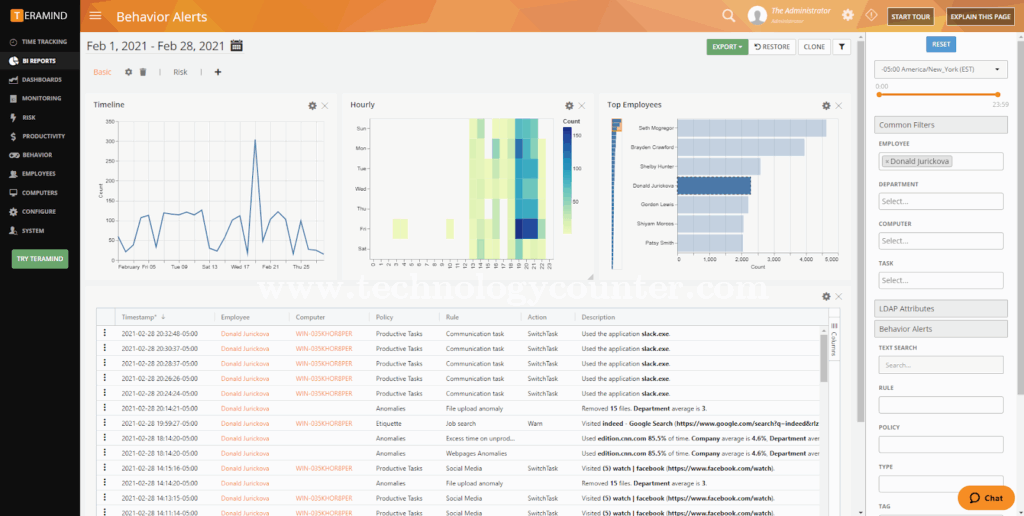
Source: Teramind
8. Proofpoint Enterprise DLP

Solution category: Enterprise DLP (focuses on email, endpoint, and cloud DLP)
Proofpoint Enterprise Data Loss Prevention is a people-centric solution to protect against data loss caused by negligent, compromised, or malicious insiders. It unifies DLP across email, cloud, and endpoint environments, correlating content, behavior, and threat telemetry to give security teams contextual insight into incidents.
Key features include:
- People-centric risk detection: Focuses on the user behind each alert by analyzing behavioral and threat data, helping teams determine if an incident stems from compromise, negligence, or malicious intent.
- Cross-channel policy enforcement: Extends unified DLP policies across email, cloud apps, and endpoints, reducing administrative effort and ensuring consistent data protection.
- Customizable detectors: Leverages sensitive data classifiers and allows custom policy creation using techniques like data matching, indexed document matching, and OCR.
- Unified investigation interface: Provides a timeline-based alert view that consolidates activity across channels, enabling faster triage, response, and user-focused remediation actions.
- AI-powered classification integration: Enhances detection through integration with Proofpoint Intelligent Classification and Protection, enabling automated discovery and labeling of sensitive data.
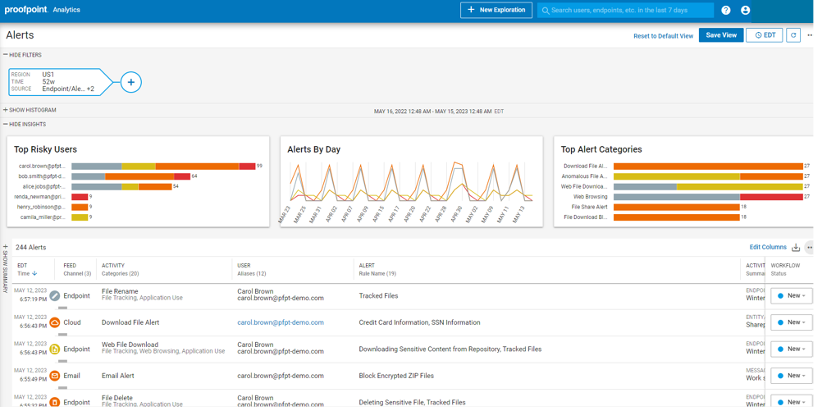
Source: Proofpoint
9. Nightfall

Solution category: Cloud DLP
Nightfall is an AI-native data loss prevention platform for the cloud-first, AI-driven workplace. Unlike traditional DLP tools, Nightfall uses large language models (LLMs) and behavioral analysis to automatically detect, classify, and block sensitive data across SaaS, Gen AI apps, endpoints, browsers, and cloud services.
Key features include:
- AI-powered detection and response: Uses LLMs and behavioral models to accurately identify sensitive data (e.g., PII, PHI, PCI, and NHIs) and understand context, reducing false positives.
- Exfiltration prevention: Automatically traces and blocks sensitive data from leaving the organization via email, SaaS, browsers, AI tools, removable media, and desktop applications.
- SaaS and Gen AI coverage: Protects data in platforms like Slack, Google Workspace, Microsoft 365, Salesforce, GitHub, and across Gen AI apps, monitoring prompts, uploads, and copy/paste actions.
- Autonomous analyst (Nyx): AI agent that investigates incidents with contextual awareness, providing intelligent decisions and user coaching before data exposure occurs.
- Data discovery and classification at rest: Continuously scans cloud apps to detect and remediate exposed sensitive data, even in stored files and misconfigured shares.
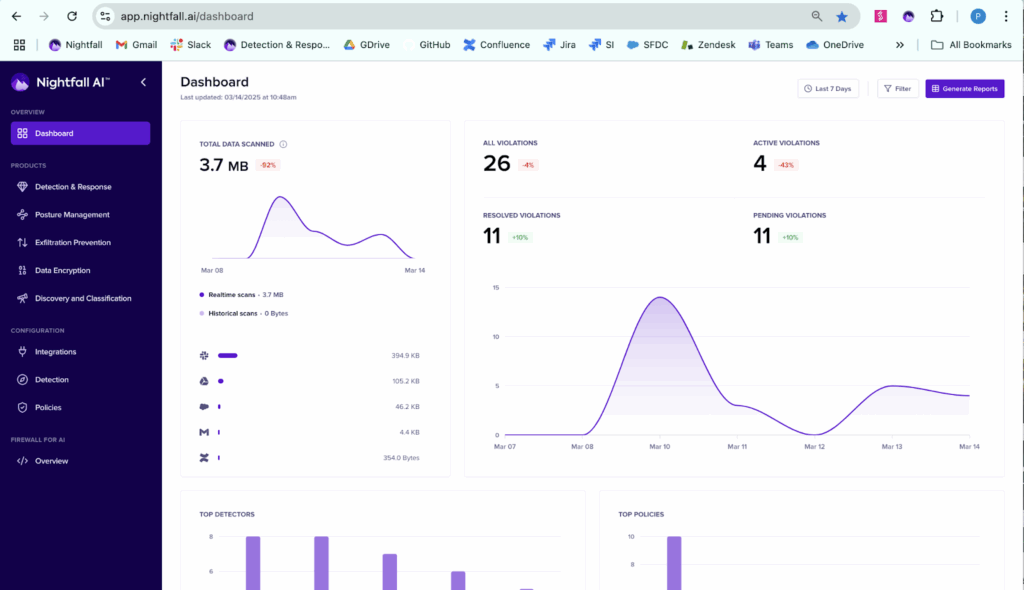
Source: Nightfall
10. Endpoint Protector DLP

Solution category: Endpoint DLP
Endpoint Protector is a cross-platform data loss prevention solution to protect sensitive data on Windows, macOS, and Linux endpoints. Designed for real-time monitoring and control, it prevents unauthorized data transfers, secures USB and peripheral devices, and helps enforce regulatory compliance. The solution applies content-aware protection to stop insider threats and data leakage at the endpoint level.
Key features include:
- Multi-OS endpoint protection: Secures Windows, macOS, and Linux systems using a lightweight agent managed through a centralized, web-based dashboard.
- Real-time file transfer control: Blocks or allows data transfers via email, cloud apps, and messaging platforms based on file type, content, and user policies.
- USB and peripheral device security: Locks down unauthorized USB devices, applies granular access controls, and enforces automatic encryption for approved media.
- Intellectual property protection: Uses advanced methods like N-gram-based text analysis to detect and prevent unauthorized transfers of source code and other IP.
- PIi discovery and protection: Scans and monitors endpoints for personally identifiable information, applying real-time controls to prevent unauthorized exposure.
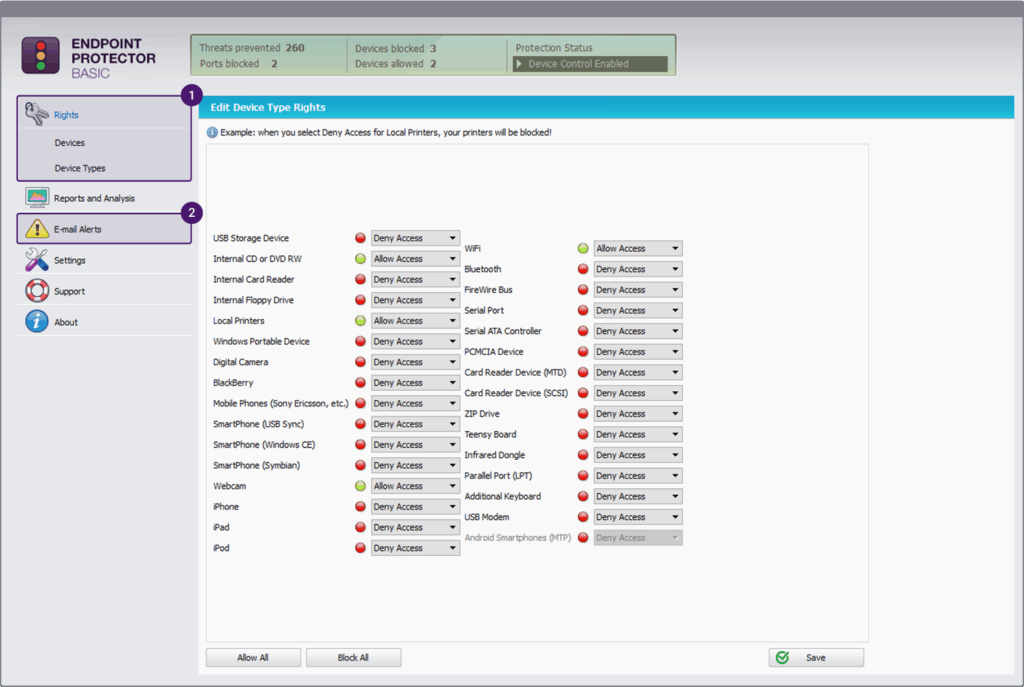
Source: Endpoint Protector