Best Unified Endpoint Management Tools: Top 5 Options in 2025

What Are Unified Endpoint Management Tools?
Unified Endpoint Management (UEM) tools are platforms that allow organizations to manage and secure all endpoints, such as laptops, desktops, mobile devices, tablets, and IoT systems, from a single console. They combine functions that were once handled separately by Mobile Device Management (MDM) and Client Management Tools (CMT), offering a unified approach to endpoint visibility and control.
UEM solutions simplify administration by providing centralized policy enforcement, configuration management, and monitoring across operating systems like Windows, macOS, Android, iOS, and Linux. This helps IT teams maintain consistent security standards and compliance while reducing management complexity.
By consolidating management and security across all endpoints, UEM tools reduce operational overhead, improve device security, and enable a more seamless user experience.
This is part of a series of articles about endpoint security.
In this article:
Core Features of Unified Endpoint Management Tools
Cross-Platform Device Management
Cross-platform device management is the foundation of UEM. It allows administrators to discover, enroll, and manage devices running different operating systems from a single interface. This eliminates the need for separate tools for each platform.
Administrators can apply consistent configurations, enforce security settings, and monitor compliance across Windows, macOS, Linux, iOS, and Android devices. Modern UEM platforms also integrate with device enrollment programs, such as Apple Business Manager and Android Enterprise, to automate provisioning and onboarding.
Application and Patch Management
UEM tools simplify the deployment, updating, and removal of applications across all managed endpoints. They support both system and user-level installations, automate software rollouts, and ensure that users always have the correct application versions.
Patch management features automatically identify and deploy security and feature updates for operating systems and third-party applications. This reduces exposure to vulnerabilities and ensures compliance with organizational and regulatory standards. By centralizing application and patch management, IT teams can reduce manual effort, prevent configuration drift, and minimize downtime caused by outdated or insecure software.
Identity and Access Management
UEM platforms integrate identity and access management (IAM) to secure endpoint authentication and enforce least-privilege access. They typically connect with directory services like Active Directory, Azure AD, or cloud identity providers to manage user credentials and device associations.
Using IAM features, organizations can implement multifactor authentication (MFA), conditional access policies, and single sign-on (SSO). Access can be dynamically adjusted based on device compliance status, user location, or risk score. This integration ensures that only trusted users and compliant devices can access corporate resources.
Endpoint Compliance and Policy Enforcement
Compliance management in UEM ensures that all devices adhere to corporate security and configuration policies. Administrators can define rules for encryption, password strength, OS versions, and installed applications, with automated monitoring to detect deviations.
When a device falls out of compliance, the UEM system can trigger remediation actions such as isolating the device from the network, pushing corrective configurations, or alerting administrators. This proactive enforcement helps maintain security hygiene across all endpoints and supports audits by providing detailed compliance reports and historical data.
Remote Content Distribution and Self-Healing
UEM tools enable IT teams to distribute files, scripts, and updates remotely without requiring user intervention. Content delivery networks or peer-to-peer distribution methods are often used to optimize bandwidth and speed up deployment.
Self-healing capabilities allow the system to automatically detect and correct issues such as missing configurations, failed updates, or corrupted files. Scripts or predefined workflows can restore functionality without manual input. These features improve endpoint reliability, reduce help desk tickets, and ensure that devices remain operational even in remote or bandwidth-constrained environments.
What Are the Limitations of UEM in a BYOD Environment?
While unified endpoint management platforms offer comprehensive control, they face challenges in bring-your-own-device (BYOD) scenarios due to the blurred line between personal and corporate ownership. Key limitations include:
- Privacy concerns: Employees may resist enrolling personal devices due to fears of invasive monitoring or data wiping, limiting IT visibility and control.
- Limited enforcement: UEM policies must strike a balance between security and user autonomy. This often leads to reduced enforcement capabilities compared to corporate-owned devices.
- Platform fragmentation: BYOD environments introduce a wider range of devices, OS versions, and configurations, increasing the complexity of consistent policy application.
- App and data segregation: Ensuring clear separation between personal and business data is critical, but not all UEM tools offer strong app sandboxing or containerization for this purpose.
- Enrollment resistance: Without incentives or clear communication, users may avoid device enrollment altogether, creating gaps in endpoint compliance and visibility.
Better Endpoint Security for Contractors – on Unmanaged Devices
Discover the top solutions for providing secure remote access to contractors on unmanaged laptops. No shipping hardware, no VDI.

Notable Unified Endpoint Management Tools
1. Venn: A UEM Alternative for BYOD

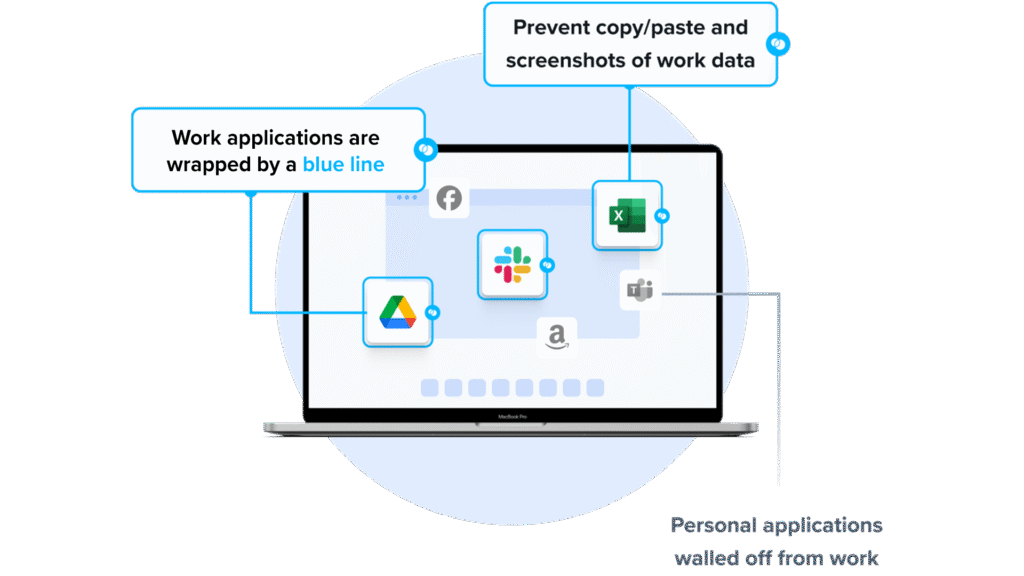
Venn’s Blue Border™ extends enterprise-grade endpoint security to BYOD and unmanaged laptops used by contractors, remote employees, and third-party workers. Unlike traditional UEM solutions, which require full device enrollment, Venn governs only access to sensitive company data and applications through its Secure Enclave, without impacting the device’s configuration. Inside the Enclave, data is encrypted, access is controlled, and work activity is visually separated from personal use, keeping corporate information secure while respecting employee privacy.
Key security controls include:
- Blocking copy/paste between work and personal apps
- Restricting file downloads and use of external storage
- Preventing or watermarking screenshots
- Enforcing consistent protections across both browser-based and local applications
You can book a quick demo here.
2. Microsoft Intune
Microsoft Intune is a cloud-based UEM solution to manage and protect endpoints across diverse platforms. Integrated with Microsoft 365, it supports Windows, macOS, iOS, Android, and Linux, offering cross-platform management for both corporate and bring-your-own devices.
Key features include:
- Endpoint management: Manage mobile, desktop, and virtual devices across Windows, macOS, iOS, Android, and Linux from a unified interface.
- Endpoint security: Apply security baselines, device compliance rules, and conditional access to protect data across all device types.
- Mobile application management (MAM): Secure and manage apps on both managed and unmanaged devices using app protection policies without requiring full device enrollment.
- Zero-touch deployment: Provision devices with minimal user interaction using automated enrollment options like Windows Autopilot and Apple Automated Device Enrollment.
- Endpoint analytics: Gain visibility into endpoint performance, startup times, app reliability, and compliance status with insights and recommendations.
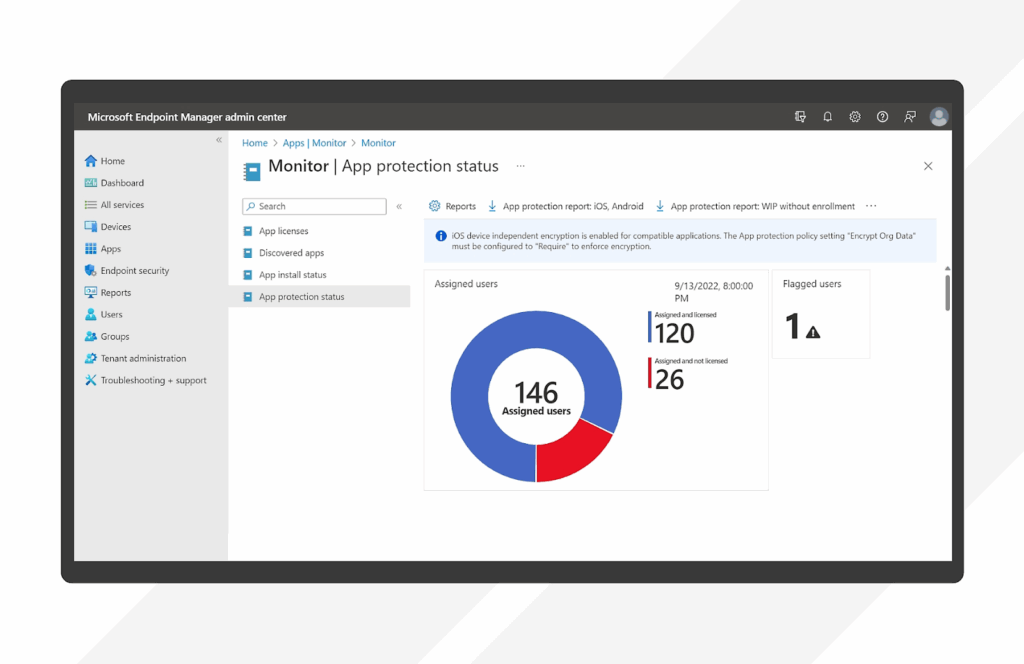
Source: Microsoft
3. IBM MaaS360

IBM MaaS360 is a cloud-based UEM platform that enables centralized management and security for a range of endpoints, including laptops, desktops, mobile devices, wearables, IoT, and purpose-built devices. Built on a multi-tenant SaaS architecture and hosted on IBM Cloud, MaaS360 integrates easily with both cloud-based and on-premises enterprise resources.
Key features include:
- Cross-platform management: Supports iOS, Android, Windows, macOS, and purpose-built devices from a unified portal. Offers over-the-air configuration, device visibility, and policy enforcement.
- SaaS architecture with Cloud Extender: Connects with corporate resources via cloud or on-premise using Cloud Extender, allowing seamless access to identity systems, file shares, and internal services.
- AI-driven analytics and threat management: Uses built-in AI to detect risks and automate remediation across apps and devices. Supports phishing detection, privilege misuse alerts, and integration with SIEM/SOAR platforms.
- Secure container architecture: Isolates corporate data in managed mobile apps, supporting secure content sharing, app-level policies, and personal/work data separation.
- Mobile application and content management: Enables app deployment via a curated app catalog, supports public and internal apps, and manages app security via SDK wrapping and containerization.
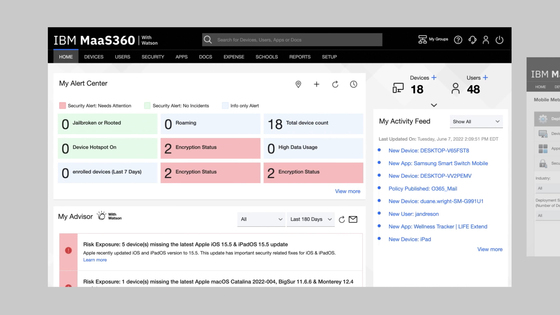
Source: IBM
4. BlackBerry UEM

BlackBerry UEM is a unified platform to secure and manage endpoints across the digital workplace. It enables organizations to support a range of devices while maintaining strong security and compliance. Built with a focus on privacy and usability, BlackBerry UEM allows IT teams to manage devices, apps, and data through a single console.
Key features include:
- Cross-platform Endpoint management: Supports centralized control and security for a wide array of devices across iOS, Android, Windows, macOS, and more, all from a single unified interface.
- Data protection: Provides encryption for data at rest and in transit, securing corporate assets across all devices and networks, including defense against unsecured connections and DoS attacks.
- Compliance and regulatory readiness: Meets stringent government and industry standards, including BSI certification, validating that communications and device operations are protected from unauthorized access and interception.
- Integrated threat defense: Proactively defends against evolving threats by enabling early detection and response, reducing the risk of data breaches and minimizing security gaps across endpoints.
- Seamless experience: Offers native system integration and privacy controls that separate personal and corporate data, requiring no extra apps or complex user training to maintain security and productivity.
5. ManageEngine Endpoint Central

ManageEngine Endpoint Central is an UEM platform that unifies device management, endpoint security, and user experience into a single console. Designed to support desktops, laptops, servers, and mobile devices, it offers IT teams centralized control across on-premises, remote, and hybrid environments.
Key features include:
- Cross-platform endpoint management: Manage Windows, macOS, Linux, iOS, Android, and Chrome OS devices through a unified console. Support for desktops, laptops, servers, and mobile endpoints ensures broad coverage.
- Automated patch management: Automate the deployment of OS and third-party patches across platforms to reduce vulnerabilities and maintain compliance with security standards.
- Threat detection and remediation: Continuously monitor endpoints to detect vulnerabilities, enforce over 75 CIS benchmarks, and trigger remediation workflows for faster response.
- Ransomware protection: Investigate root causes of ransomware attacks, respond immediately to incidents, and implement prevention strategies to block future threats.
- Asset management: Track software and hardware inventory, license usage, and warranty data, while receiving real-time alerts on asset changes.
Source: ManageEngine
Related content: Read our guide to unified endpoint management solutions
Conclusion
Despite their broad capabilities, Unified Endpoint Management tools struggle to deliver the same level of security and compliance in BYOD settings as they do for corporate-owned devices. Privacy concerns, limited control over personal devices, and user resistance to enrollment make full UEM adoption impractical for many organizations. This gap highlights the need for alternative solutions like Venn, which protect corporate data without requiring intrusive device management or compromising user privacy.