Jamf for BYOD: Features, Pricing, Limitations and Alternatives

What Is Jamf?
Jamf is a software platform that helps organizations manage Apple devices across their workforce. It provides tools for deploying, configuring, and securing iOS, macOS, iPadOS, and tvOS devices at scale. By using Jamf, IT teams can remotely configure settings, deploy applications, enforce security policies, and track device health from a centralized dashboard.
The system is used by enterprises, educational institutions, and organizations with significant Apple device fleets, enabling administration and compliance with company standards. In addition to device management, Jamf supports automated workflows that reduce manual IT workload.
Its capabilities allow for zero-touch deployment, making it easy to provision new devices for employees without requiring IT staff to physically handle each device. Administrators can push apps, set restrictions, and wipe or lock devices if they are lost or stolen.
This is part of a series of articles about BYOD
In this article:
How Does Jamf Support BYOD Scenarios?
Jamf supports BYOD by using Apple’s account-driven User Enrollment, which creates a clear boundary between personal and corporate data on employee-owned devices. This enrollment method is designed to preserve user privacy while allowing IT to manage only the business-related parts of the device.
When users enroll their personal iPhones, iPads, or Apple Vision Pro devices, they do so by signing in with a Managed Apple ID through the device settings. This action initiates a secure connection to Jamf’s enrollment portal. The process results in an unsupervised device state, meaning the user retains full control and can remove the management profile at any time.
Account-driven User Enrollment ensures that IT cannot access personal apps, data, or unique device identifiers. Instead, management is restricted to institutional apps, accounts, and configurations, such as corporate email, calendars, Wi-Fi, and VPN settings. This separation is enforced by the operating system itself, not just by Jamf policy.
The enrollment process is transparent: users can view the level of access and control the organization will have before completing enrollment. Once enrolled, Jamf can issue configuration profiles, deploy managed apps, and perform limited remote commands like data wipe for corporate content. However, it cannot affect personal files or settings.
Jamf BYOD Features
Jamf enables management of personal devices in a BYOD environment, ensuring corporate data protection while ensuring employee privacy. It integrates security measures directly into the device management workflow.
Key features:
- User enrollment for iOS and iPadOS: Employees can enroll their personal devices using Apple’s User Enrollment framework. This creates a managed work partition on the device where IT can apply policies, deploy apps, and enforce security without gaining access to personal files or apps. Limited Android support is available through similar enrollment workflows.
- Separation of work and personal data: Corporate data and applications are isolated from personal content. IT administrators can wipe company data without affecting personal photos, contacts, or other personal use, ensuring compliance while protecting employee privacy.
- Built-in secure connectivity: Jamf includes VPN and Zero Trust Network Access (ZTNA) capabilities that automatically route work traffic through secure connections. This enables employees to access internal applications and resources safely, whether on corporate networks or public Wi-Fi.
- Mobile threat defense: The platform includes phishing detection, app reputation checks, and on-device threat analysis to protect against malicious activity. It can block risky applications or unsafe URLs before they reach the user, reducing the risk of data breaches.
- On-device and network protection: Jamf enforces protection both locally on the device and at the network level. This includes monitoring for jailbreak/root exploits, unsafe networks, and anomalous activity on iPhones, iPads, and supported Android devices.
- Policy integration without performance impact: Security policies are applied in the background with minimal effect on device performance. Encryption, compliance checks, and access controls run seamlessly, so employees can use their devices normally without noticeable slowdowns.
Jamf Pricing for Business
Jamf offers tiered pricing based on device type and organizational needs.
For macOS devices, the cost is $10 per device, per month (billed annually) with a 25-device minimum. This plan includes core macOS management, workflow automation, endpoint protection, vulnerability management, content filtering, and identity and access management with Zero Trust Network Access.
For mobile devices, including iOS, iPadOS, visionOS, watchOS, tvOS, and limited Android, the price is $5.75 per device, per month (billed annually) with a 25-device minimum. It covers full mobile device management, mobile threat defense, and Zero Trust Network Access.
For small businesses, pricing starts at $4 per device, per month. This package supports macOS, iOS, iPadOS, and tvOS, with simplified management tools, simplified app distribution, and built-in macOS malware protection.
Key Jamf BYOD Limitations
The Jamf platform has some notable constraints that can impact usability and efficiency. Some stem from Apple’s device management restrictions, while others relate to gaps or delays in Jamf’s own feature set. These limitations were reported by users on the G2 platform:
- Limited control over certain system settings on Apple devices, requiring user admin credentials for tasks like enabling Zoom screen sharing
- Delays in adopting newer features such as Return to Service, Jamf SSO, and some Declarative Device Management (DDM) capabilities
- Lack of fine-grained permissions and access controls for administrators
- Interface quirks that can cause incomplete search results unless queries are structured in specific ways
- Dashboards lack flexible organization options, making navigation less intuitive
- Patch management lags behind, with app updates (e.g., antivirus, Chrome) sometimes appearing in Jamf days after release
- Reporting tools for application usage, such as tracking Adobe software across multiple devices, are cumbersome and require manual checks per device
Related content: Read our guide to BYOD policy
Notable Jamf BYOD Alternatives
1. Venn

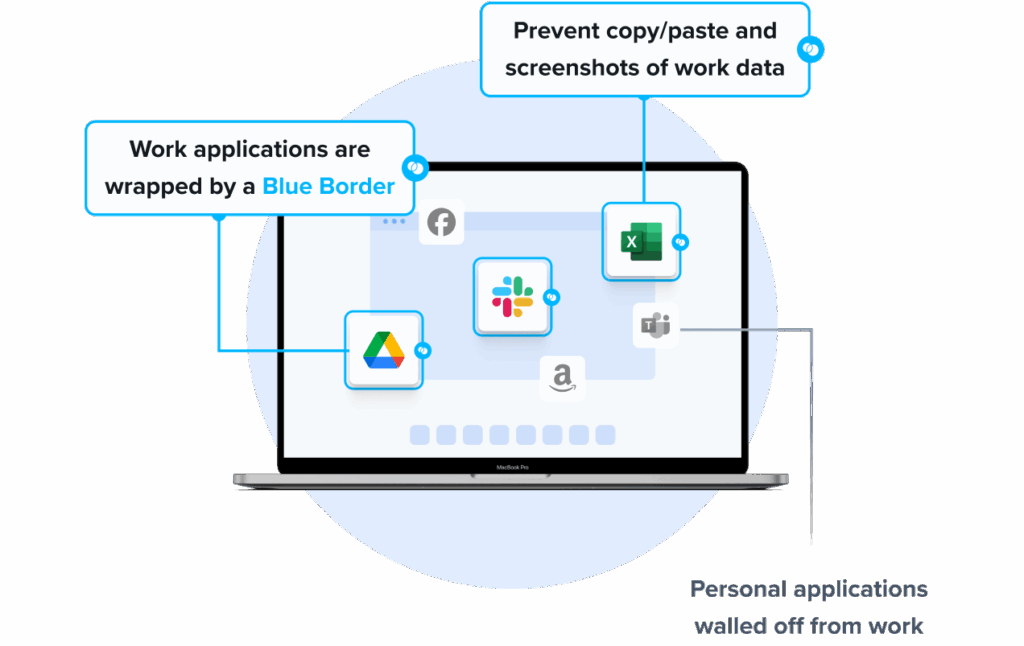
Venn is a secure BYOD workforce solution designed to protect company data on unmanaged and BYOD Mac and Windows laptops. Unlike Jamf, which focuses on device-level management within the Apple ecosystem, Venn creates a company-controlled Secure Enclave on the user’s computer (Mac or PC) that isolates work activity from personal use. This allows organizations to protect both browser-based and locally installed applications without requiring full device enrollment or control. Work apps run locally on the endpoint with no lag or latency, while Blue Border™ provides a clear visual distinction between work and personal activity. Venn is particularly well-suited for organizations with mixed device fleets and extended workforces that include contractors, freelancers, and offshore teams.
Key Features Include
- Secure Enclave technology: Encrypts and isolates work data on personal devices (both Mac and PC), both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
2. ManageEngine Mobile Device Manager Plus

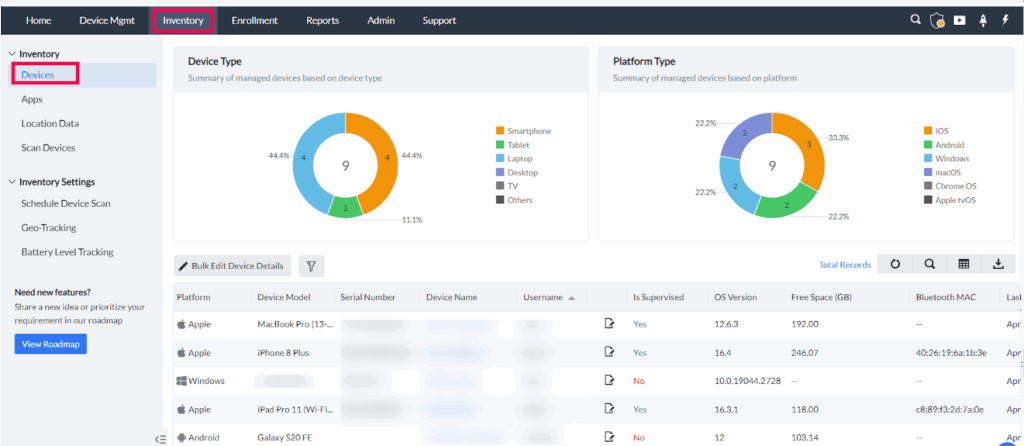
ManageEngine Mobile Device Manager Plus is a unified endpoint management solution to secure and manage devices across different platforms. It supports smartphones, tablets, laptops, desktops, TVs, and rugged devices running Android, iOS, iPadOS, tvOS, macOS, Windows, and Chrome OS.
Key features include:
- Cross-platform device management: Manage smartphones, tablets, laptops, desktops, TVs, and rugged devices from a single interface, supporting Android, iOS, iPadOS, tvOS, macOS, Windows, and Chrome OS.
- Enrollment options: Quickly bring devices under management with simple enrollment workflows for both corporate-owned and BYOD devices, including authentication steps to ensure secure onboarding.
- Unified dashboard: View the entire device ecosystem in one place through an intuitive dashboard, simplifying monitoring and administrative tasks.
- Policy enforcement: Configure profiles to automatically enforce settings for Wi-Fi, VPN, email, and other parameters to keep devices compliant with corporate standards.
- Remote troubleshooting: View and control devices to diagnose and fix issues without requiring physical access.
Source: ManageEngine
3. Hexnode UEM

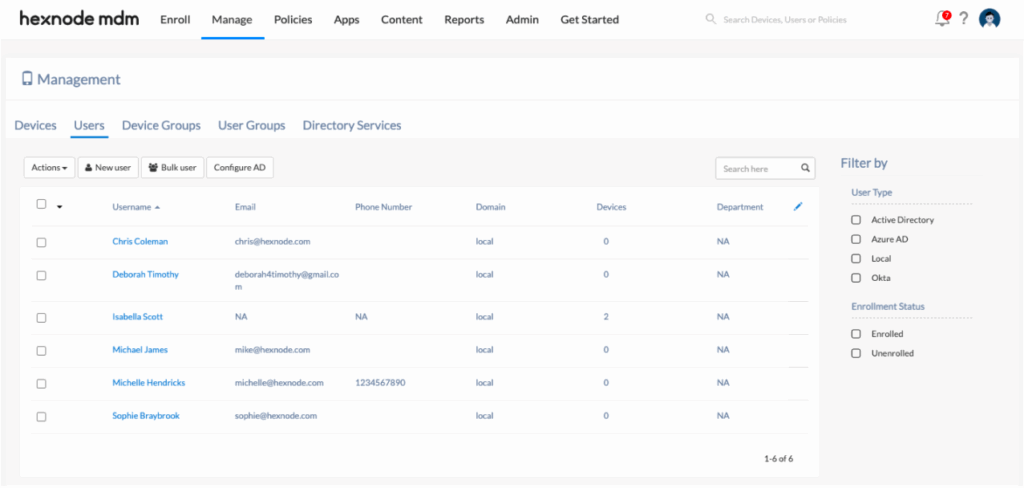
Hexnode UEM is a unified endpoint management platform to secure and manage desktops, mobile devices, rugged hardware, IoT endpoints, and digital signage from a single interface. It supports multiple operating systems and device types, enabling IT teams to enforce security policies, deploy applications, manage updates, and control access across endpoints.
Key features include:
- Cross-platform endpoint management: Manage desktops, smartphones, tablets, rugged devices, IoT hardware, and digital signage, with support for multiple operating systems.
- Identity and access integration: Connect with identity providers via Hexnode Access to synchronize user identity across devices and apps, ensuring only authorized users access corporate resources.
- Automated patch management: Define OS and application update rules once and ensure devices automatically stay on the latest versions without manual intervention.
- End-to-end automation: Use Hexnode Deployments to create trigger-based workflows for device provisioning, configuration, app deployment, and policy enforcement.
- Mobile device management: Enroll, configure, monitor, and secure mobile endpoints with centralized controls for apps, policies, and restrictions.
Source: Hexnode
4. IBM MaaS360

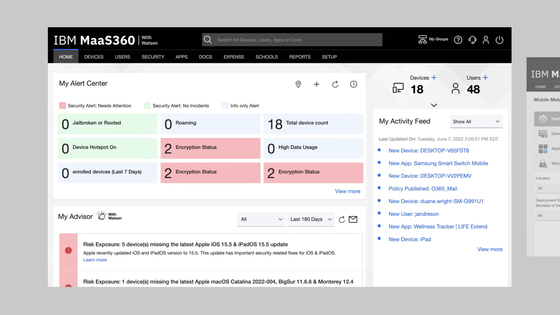
IBM MaaS360 is an AI-driven endpoint management platform that helps organizations manage and protect mobile devices, laptops, and other endpoints from a single console. It simplifies device enrollment, application deployment, and security enforcement to support hybrid and frontline workforces.
Key features include:
- Unified device management: Manage mobile devices, laptops, and wearables from one console, automating provisioning, configuration, and policy enforcement.
- Application management: Distribute productivity and business apps securely while maintaining compliance with corporate policies.
- BYOD containerization: Separate work and personal data with encrypted containers, ensuring company data remains protected while preserving employee privacy.
- Multifactor authentication (MFA): Enforce MFA to secure access to corporate resources across both company networks and public Wi-Fi.
- Continuous threat defense: Detect, block, and remediate security risks in near real time using AI dashboards and device protection.
Source: IBM
5. Scalefusion

Scalefusion is a unified BYOD management platform that helps balance employee freedom with corporate data protection. It supports a range of devices and operating systems, offering simple onboarding, containerization, security enforcement, and compliance monitoring. It helps organizations secure their data while keeping the BYOD experience seamless for employees.
Key features include:
- Cross-platform device support: Manages employee-owned devices regardless of operating system.
- Enrollment options: Enables self-onboarding via email, QR code, GSuite, Microsoft, PingOne, or Apple User Enrollment.
- Containerization for data separation: Isolates work apps and data from personal use to protect company information while preserving employee privacy.
- Security policy enforcement: Apply strong passcodes, configure VPN/Wi-Fi certificates, and enforce work-only data flow rules to prevent leaks.
- Compliance management: Performs compliance checks for standards like HIPAA and GDPR.
Source: Scalefusion
Conclusion
Managing BYOD environments requires balancing corporate security with employee privacy. Solutions like Jamf and its alternatives address this challenge by combining containerization, access controls, encryption, and automated policy enforcement. These approaches enable organizations to protect sensitive data while giving employees flexibility to use their own devices, ensuring security and compliance without disrupting the user experience.