Best Secure Remote Access Tools: Top 5 Options in 2025

What Are Secure Remote Access Tools?
Secure remote access tools enable users to access organizational systems, networks, and resources from remote locations, such as home offices or while traveling, without compromising security. These tools provide a controlled gateway for users to access files, applications, and internal services as if they were physically present in the office. The primary goal is to facilitate productivity and flexibility while ensuring the protection of sensitive data against unauthorized access.
These tools address modern work requirements, including hybrid and fully remote environments with bring your own device (BYOD) policies. They implement security controls that monitor, authenticate, and authorize every connection attempt. By using encryption, access control mechanisms, and threat detection capabilities, secure remote access tools reduce organizational risk while allowing employees to work securely from anywhere, on any device.
In this article:
Key Components and Capabilities of Secure Remote Access Tools
Separation Between Work and Personal Data on Endpoints
With the rise of bring your own device (BYOD) policies, employees and contractors often use personal laptops for work. This creates a key challenge: traditional device management tools like MDM or UEM were built for full control of the device, often intruding on the user’s personal apps, data, and settings. These tools are best suited for company-owned hardware, not personally owned endpoints.
To address this, modern remote access strategies now emphasize isolating business activity from the personal side of a device. Instead of managing the entire system, a lightweight agent or isolated compute layer is installed locally. This allows organizations to monitor device posture, enforce access policies, and secure work-related apps and data without touching personal files or settings.
This form of endpoint access isolation ensures compliance and protection of corporate resources on unmanaged Windows and macOS devices. It enables security teams to apply granular, business-only controls while preserving user privacy and autonomy. For organizations with remote or contract-based workforces, this approach offers an effective balance between security, usability, and trust.
Zero Trust Network Access (ZTNA)
Zero trust network access (ZTNA) represents a modern approach to remote access, based on the “never trust, always verify” principle. ZTNA solutions grant users access to specific applications and resources, instead of the entire corporate network, by continuously evaluating authentication and authorization parameters. This limits the attack surface and ensures that even if a device or user is compromised, the impact remains contained.
ZTNA has gained traction as organizations move beyond traditional network boundaries. It emphasizes identity, device health, and context, making access decisions on a case-by-case basis. ZTNA can also adapt dynamically to changing risk factors, such as user location or unusual behavior, providing continuous protection and granular control for remote workforces.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) requires users to verify their identity using two or more independent credentials, typically something they know (password), something they have (smartphone or token), and something they are (biometric). This greatly reduces the effectiveness of password-based attacks, including phishing and credential stuffing, because an attacker must compromise multiple factors to gain access.
MFA is often built into secure remote access tools or integrated via third-party solutions. Its implementation significantly enhances the security of remote connections, especially when paired with other controls like VPNs or ZTNA. Organizations should prioritize user-friendly MFA methods to minimize friction, as complex authentication processes can hinder adoption and productivity.
Encryption
Encryption is essential in secure remote access, ensuring that data transmitted between endpoints and corporate resources cannot be read by unauthorized parties. Transport layer security (TLS) is a commonly used protocol for encrypting data in transit, while strong encryption algorithms safeguard sensitive information against interception and tampering during remote sessions.
Encryption is not limited to data in transit; securing stored or cached data on remote endpoints is also critical. Some remote access solutions employ full-disk encryption or encrypted containers to prevent local data leakage if a device is lost or stolen. Implementing encryption strategies across all endpoints and communication channels is a foundational best practice for remote security.
Role-Based Access Control (RBAC)
Role-based access control (RBAC) allows administrators to define who can access specific resources based on their role within the organization. Rather than granting broad access, RBAC enforces the principle of least privilege, minimizing the potential impact if an account is compromised. This approach restricts each user’s connections to only what is necessary to perform their job functions.
RBAC simplifies access management by grouping permissions according to organizational roles, which is particularly useful when dealing with employees, contractors, or temporary staff. Combined with logging and audit capabilities, RBAC facilitates compliance with regulatory requirements and enables efficient response to security incidents by providing clear records of who accessed what and when.
Enable Remote Workers Without VDI or Issuing Devices
Secure your entire extended workforce without issuing devices or VDI. Keep your organization agile, compliant, and secure.

Notable Secure Remote Access Tools
1. Venn

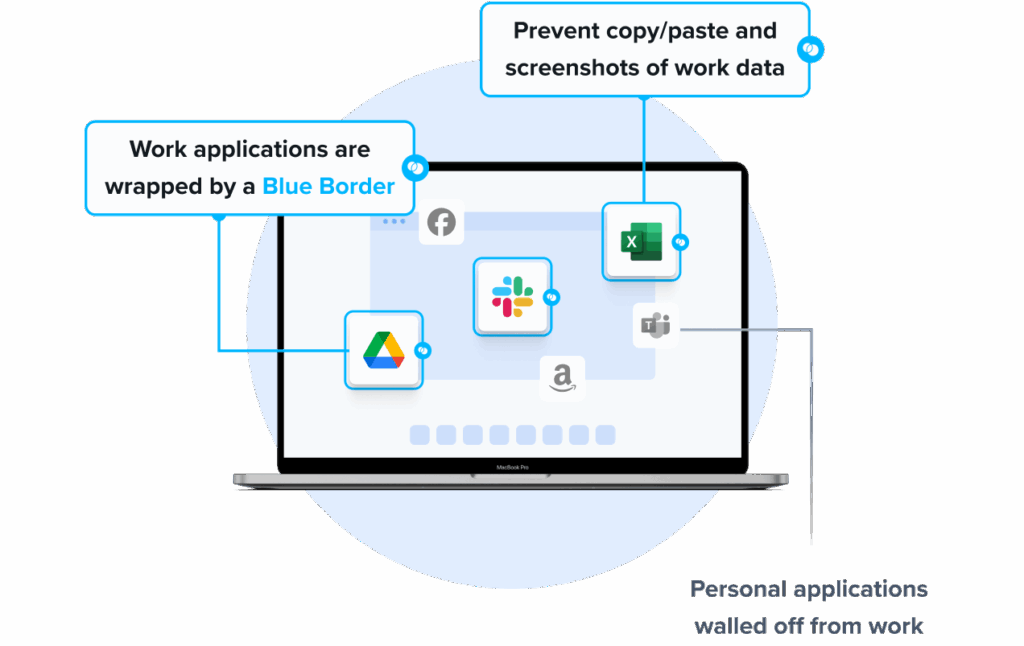
Venn’s Blue Border™ secures remote access by protecting company data and applications on BYOD computers used by contractors and remote employees. Similar to an MDM solution but for laptops – work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Key Features include:
- Seamless MFA integration: Works with Okta, Azure, and Duo for smooth, secure authentication
- Encrypted workspace: Protects all data and applications with robust encryption
- Context-aware access controls: Enforces policies based on user, device, and environment
- Comprehensive session logging: Tracks all activity with full audit visibility
- Unified Zero Trust solution: Combines endpoint protection, remote access, and Zero Trust security
- Faster, scalable alternative: Optimized performance compared with legacy VPNs and VDI
Schedule a demo of Blue Border™
2. Oracle Secure Global Desktop

Oracle Secure Global Desktop provides secure, centralized access to published applications and desktops running on Windows, Unix, mainframe, and IBM i systems. It enables users to connect from PCs, thin clients, and mobile devices through a web browser with Java or a native client. Sessions run on centralized servers, ensuring sensitive data stays within the data center.
Key features include:
- Broad client support: Works with Windows, macOS, Linux, Solaris, thin clients, and mobile devices using a browser or native client
- Adaptive internet protocol (AIP): Optimizes performance over varied bandwidths, from low-speed modems to high-speed LANs
- Session resumability and mobility: Allows users to move between devices and resume active sessions without disruption
- Centralized application hosting: Keeps applications and data in the data center, improving security and manageability
- Dynamic application delivery: Assigns applications to users or groups automatically via Object Manager and profiles
3. Ericom Connect

Ericom Connect is a remote desktop and application publishing solution that delivers secure, browser-based access to workplace apps and desktops from different devices and operating systems. Available as cloud-based or on-premises software, it provides centralized management for IT teams. It reduces administrative overhead while supporting MFA and VPN integration.
Key features include:
- Flexible deployment: Available as cloud service or on-premises software to fit different IT strategies
- Clientless access: Browser-based connectivity with no client software to install or maintain
- Centralized administration: Web-based console for publishing apps, desktops, and setting access policies
- Strong security: Supports MFA and SSL encryption for secure traffic across private or public networks
- VPN integration or offload: Works with existing VPNs or reduces VPN dependency with built-in secure tunneling
4. NinjaOne Remote

NinjaOne Remote is a fully integrated remote access solution for IT teams to manage endpoints across various environments. Accessible via a console, it helps connect to devices quickly without requiring separate tools. It offers strong encryption, flexible connection options, and built-in privacy controls.
Key features include:
- Instant connections: Launch remote sessions directly from the NinjaOne console or service tickets
- Cross-platform support: Full remote access for Windows, macOS, and Linux endpoints, plus Quick Connect for BYOD or off-network devices
- Enterprise-grade security: Sessions encrypted with modern standards and fully logged or recorded for compliance needs
- Privacy controls: Role-based access, auto-clearing clipboards, and “paste as keystrokes” to protect sensitive data
- Adaptive performance: Dynamic bandwidth adjustment, GPU acceleration, and grayscale mode for stable sessions on weak networks

Source: NinjaOne
5. Apache Guacamole

Apache Guacamole is a clientless remote desktop gateway that enables secure access to desktops and servers through standard protocols like RDP, VNC, and SSH. Powered by HTML5, Guacamole makes desktops and applications accessible from anywhere and on any device, including cloud-hosted environments.
Key features include:
- Clientless remote access: Users can access desktops directly through a web browser
- Protocol support: Compatible with RDP, VNC, and SSH for varied remote access needs
- HTML5 web client: Enables cross-platform access from any device with a modern browser
- Cloud-compatible: Works well with desktops hosted in the cloud for added resilience and scalability
- Extensible APIs: Provides well-documented APIs for integration with custom or third-party applications
Source: Apache Guacamole
Related content: Read our guide to secure remote access providers
Considerations for Choosing Secure Remote Access Tools
Choosing the right secure remote access tool involves more than evaluating feature lists. Organizations must assess their operational needs, security posture, and infrastructure constraints. Below are key factors to consider when selecting a tool to ensure both usability and robust protection:
- Security architecture compatibility: Ensure the tool aligns with your security model, whether perimeter-based, zero trust, or hybrid. Tools should integrate with existing identity providers, enforce least-privilege access, and support encryption, logging, and monitoring.
- User experience and accessibility: A solution that hinders productivity will struggle with adoption. Evaluate how easily users can connect, the need for client software, and cross-device support, especially for mobile and BYOD scenarios.
- Scalability and performance: Consider how the tool performs under load and how well it scales across distributed teams. Features like dynamic bandwidth management and session resiliency are important for maintaining performance in variable conditions.
- Granular access control: Look for tools that support detailed access policies—such as RBAC or context-aware access, allowing you to define who can access what, when, and under what conditions.
- Integration with security tools: Choose a solution that integrates with SIEMs, endpoint detection tools, MFA, and other components of your security stack. Centralized logging and alerting help in incident response and compliance audits.
- Deployment and maintenance requirements: Evaluate whether the solution is cloud-native, self-hosted, or hybrid. Consider the ongoing administrative effort, software updates, and infrastructure dependencies needed to keep the tool secure and available.
- Vendor support and community: Strong vendor support or an active open-source community can make a big difference in troubleshooting and long-term viability. Review update frequency, documentation quality, and support responsiveness.
- Regulatory and compliance fit: Ensure the tool helps meet regulatory requirements like HIPAA, GDPR, or ISO 27001. Features like session logging, encryption standards, and data residency controls may be critical depending on your industry.
Related content: Read our guide to secure remote access best practices
Conclusion
Secure remote access is no longer just about connectivity. It must also provide continuous security, adaptability, and control. The right solution balances strong protection with usability, enabling employees to work productively from any location while keeping corporate data safe. By focusing on principles like least-privilege access, encryption, and integration with broader security frameworks, organizations can support flexible work models without exposing themselves to unnecessary risk.