Best VDI Platforms and Alternatives: Top 7 in 2026

What Are Virtual Desktop Infrastructure (VDI) Platforms?
A VDI (Virtual Desktop Infrastructure) platform is a system that hosts operating systems and applications on a central server and delivers them to users as virtual desktops over a network. VDI platforms are a legacy technology used for consistency and security, but they are often lacking in user experience and cost efficiency. VDI is typically slow and unsuitable for modern work environments like BYOD (Bring Your Own Device).
Key providers of VDI alternatives include VMware (Omnissa), Citrix, Microsoft Azure, and Venn. VDI platforms offer centralized management, improved security by keeping data in the data center, and flexibility for a dynamic workforce by allowing users to access their virtual desktops from any device, anywhere.
How VDI platforms work:
- Centralized hosting: A hypervisor (a software layer) runs on a physical server in a data center to create and manage virtual machines (VMs).
- Virtual desktop creation: A “golden image” of an operating system (like Windows) is used to create multiple virtual desktops.
- Connection broker: When a user logs in, a connection broker within the VDI platform assigns them a virtual desktop from a pool of available VMs.
- Remote access: Users connect to their assigned virtual desktop from a physical device (like a laptop or tablet) using a remote desktop protocol (RDP) or a web interface.
In this article:
How VDI Platforms Work
Centralized Hosting
VDI centralizes computing resources like CPU, memory, and storage within a data center or cloud environment. While this structure provides centralized control, it also concentrates risk and cost. Running large-scale virtual desktop farms requires significant investment in servers, networking, storage arrays, and high-performance GPUs.
Maintenance tasks such as patching, hardware upgrades, and capacity expansion must be handled centrally, increasing operational overhead and dependency on specialized staff. Because every session depends on backend infrastructure, a single point of failure can disrupt access for hundreds or thousands of users simultaneously. Centralized hosting also introduces bandwidth bottlenecks and latency issues, particularly for remote or global users.
Virtual Desktop Creation
Virtual desktops are generated from preconfigured templates containing operating systems, applications, and policies. This allows for standardized environments, but also limits flexibility. Updating or patching base images can break dependencies or introduce compatibility problems across different user groups. Version control and template sprawl quickly become issues in large deployments, requiring careful synchronization to avoid inconsistent user environments.
Each virtual machine consumes compute and storage resources, so even idle sessions add to infrastructure costs. Organizations often overprovision capacity to maintain performance during peak usage, driving up expenses further. Cloning, refreshing, and resetting desktops are also resource-intensive operations that can degrade system performance during maintenance windows.
Connection Broker
The connection broker manages session assignments, user authentication, and load distribution. In practice, this adds another layer of complexity and a critical point of failure. Misconfiguration or overload at the broker level can prevent users from connecting entirely, even if backend servers are operational. Maintaining high availability requires redundant brokers and complex synchronization across multiple nodes.
Security policies enforced through the broker, such as MFA, session persistence, or contextual access rules, often require integration with third-party tools and directory services. These dependencies introduce compatibility issues and complicate troubleshooting. Logging and auditing capabilities also generate significant data, which must be stored, managed, and monitored continuously.
Remote Access
Remote access relies on display protocols like RDP, PCoIP, or Blast Extreme to transmit screen data and user inputs between the data center and endpoint. These protocols are bandwidth-sensitive, and performance can degrade quickly with suboptimal connections, high latency, or packet loss. Even on stable networks, users may encounter lag, low frame rates, or degraded multimedia performance, especially in video conferencing or design applications.
Security measures such as encryption and access controls protect data in transit, but they add processing overhead and can impact responsiveness. Supporting various endpoint devices, from laptops to tablets and thin clients, introduces compatibility challenges and inconsistent experiences. In environments with bring-your-own-device (BYOD) policies, maintaining security and usability across unmanaged devices becomes even more difficult.
Why VDI Is Unsuitable for Modern BYOD Environments
While virtual desktop infrastructure offers centralized control and security, it presents limitations when applied to modern bring-your-own-device (BYOD) environments. VDI platforms assume a high level of standardization and control over the endpoint, which conflicts with the diversity and unpredictability of user-owned devices.
VDI sessions often require specialized client software or rely on specific remote display protocols that may not perform consistently across all devices and operating systems. This can result in degraded user experiences on unmanaged or older personal hardware, especially when bandwidth or device capabilities are limited.
Additionally, VDI can create latency and performance issues for mobile users or those in regions with poor network quality. These challenges make it difficult to deliver a seamless and productive experience across a wide range of user scenarios, pushing organizations to explore alternative solutions like secure access service edge (SASE), containerized workspaces, or split-tunneling architectures designed specifically for BYOD.
Related content: Read our guide to VDI security
Frustrated by Lag and Latency from VDI/DaaS?
Discover how Venn’s local-first approach secures remote workforces without the complexity and latency of traditional VDI.

Notable VDI Alternatives
1. Venn

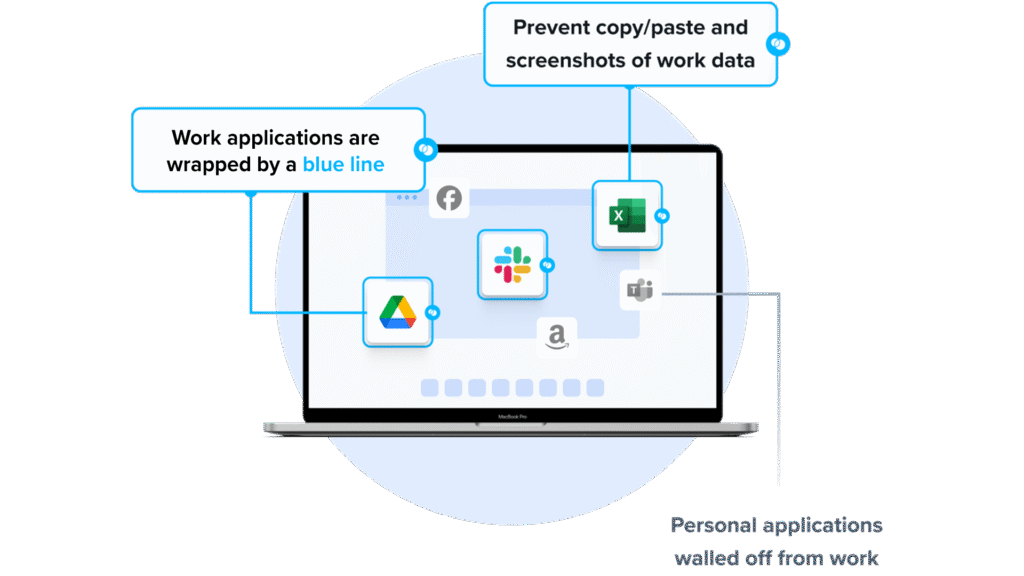
Venn’s Blue Border was purpose-built to protect company data and applications on BYOD computers used by contractors and remote employees.
Similar to an MDM solution but for laptops, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
With Venn, you can eliminate the burden of purchasing and securing laptops and managing virtual desktops (VDI.) Unlike virtual desktops, Venn keeps users working locally on natively installed applications without latency – all while extending corporate firewall protection to business activity only.
Key features include:
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
2. Menlo Secure Enterprise Browser

Menlo Secure Enterprise Browser applies isolation and zero trust controls at the browser layer. Built on network separation, browser isolation, and advanced malware defenses, it keeps active web content off endpoints and enforces least-privileged access to private and SaaS apps. Browser Posture Manager automates benchmark-aligned configurations, while HEAT Shield AI detects evasive phishing and malware.
Key features include:
- Isolation-based threat prevention: Uses network separation and browser isolation to keep active web content away from endpoints, reducing exposure to malware and phishing.
- Secure application access: Applies least-privileged, browser-based access to private web apps and SaaS, minimizing lateral movement risks from traditional VPN connections.
- Browser posture management: Automates policy configuration using benchmark-aligned settings, helping standardize Chrome and Edge security without manual tuning across numerous options.
- Threat detection with HEAT Shield AI: Detects highly evasive malware and zero-hour phishing attempts, providing protection against techniques that bypass legacy security tools.
- Forensics and data controls: Provides session-level visibility and last-mile data protections for uploads, downloads, clipboard, printing, and screen sharing through centrally managed policies.

Source: Menlo
3. Prisma Browser

Prisma Browser is a secure enterprise browser integrated with Prisma SASE. It extends zero trust access and granular data controls to managed and unmanaged devices, supports BYOD, provides visibility into GenAI usage, and enables a browser-centric approach that can reduce reliance on traditional VDI.
Key features include:
- SASE-native integration: Integrates directly with Prisma SASE to extend cloud-delivered security and policy enforcement into the browser on any device.
- Zero trust access and controls: Applies identity-based policies with granular data controls to govern application access and in-session actions for users and contractors.
- Managed and unmanaged device coverage: Delivers consistent protections and visibility across corporate endpoints and BYOD, avoiding separate tools to handle varying ownership models.
- GenAI usage governance: Adds visibility into activity within generative AI applications and restricts sensitive data sharing to reduce unsanctioned “shadow AI” risk.
- VDI reduction option: Provides a browser-centric workspace that supports secure application access, decreasing reliance on traditional VDI deployments for common use cases.
Source: Palo Alto Networks
Notable VDI Platforms
4. Microsoft Azure Virtual Desktop

Microsoft Azure Virtual Desktop (AVD) is a cloud-based desktop and app virtualization platform that runs on Azure, allowing organizations to deliver Windows desktops and applications to users from almost anywhere. Unlike traditional desktop setups, AVD provides centralized management and flexible deployment options, helping simplify IT operations, improve scalability, and strengthen security.
Key features include:
- Full Windows experience: Supports Windows 11, Windows 10, and Windows Server in both single-session and multi-session modes for flexibility and cost-efficiency
- RemoteApp delivery: Offers individual applications instead of full desktops when needed, reducing resource use and simplifying access
- Optimized Microsoft 365 integration: Delivers Microsoft 365 Apps with performance enhancements for multi-user scenarios
- Hybrid deployment: Allows hosting desktops on-premises with Azure Local, enabling hybrid cloud configurations
- Custom application support: Supports running Win32, MSIX, and Appx line-of-business applications from anywhere
Source: Microsoft
5. Citrix Virtual Apps and Desktops

Citrix Virtual Apps and Desktops, delivered through Citrix DaaS, is a virtualization platform that provides secure, centralized access to apps and desktops across hybrid and multi-cloud environments. It allows IT teams to control applications, desktops, policies, and security, while Citrix manages the underlying infrastructure, including updates and delivery components.
Key features include:
- Hybrid and multi-cloud support: Seamlessly deploy apps and desktops across public clouds (Azure, AWS, Google Cloud) and on-premises hypervisors like Hyper-V, VMware, and XenServer
- Flexible delivery methods: Support for full virtual desktops, published applications, or Remote PC access, depending on user needs and workloads
- Citrix Managed Azure: Option to offload infrastructure hosting to Citrix for simplified deployment and reduced management overhead
- Centralized management with Studio: Web-based console to configure and monitor deployments, manage machine catalogs and delivery groups, and simplify user assignments
- Secure user access: Integrates with Citrix Gateway to enable encrypted external access without exposing internal networks, using TLS-based connections
Source: Citrix
6. Omnissa Horizon

Omnissa Horizon (formerly VMware Horizon) is a desktop and application virtualization platform that delivers Windows, Linux, and macOS desktops from a centralized infrastructure to end-user devices. Built on VMware’s virtualization stack, Horizon provides secure remote access to virtual desktops and apps through various protocols and client platforms. It integrates with VMware vSphere for resource management and tools for provisioning, managing, and monitoring.
Key features include:
- VMware infrastructure integration: Built on VMware vSphere and managed via vCenter Server, Horizon leverages a mature virtualization ecosystem for performance and scalability
- Flexible protocol support: Supports VMware Blast Extreme, Microsoft RDP, and Teradici PCoIP to optimize user experience based on network conditions and endpoint capabilities
- Management tools: Includes View Manager for administration, View Composer for rapid provisioning and cloning, and Persona Management for user profile handling
- Application virtualization: VMware ThinApp enables isolation and delivery of Windows apps without conflicts or local installs
- Cross-platform client support: Horizon Client is available on Windows, macOS, Linux, Android, iOS, and ChromeOS (via browser), ensuring access across devices
Source: Omnissa
7. Windows 365

Windows 365 is a cloud-based desktop virtualization service from Microsoft that delivers a full Windows experience with apps, settings, and data, to any device via a Cloud PC. Unlike traditional VDI solutions that require complex infrastructure, Windows 365 simplifies provisioning and management by running entirely in the Microsoft Cloud.
Key features include:
- Persistent cloud PCs: Each user gets a personal Windows environment that retains settings, apps, and files across sessions
- Device-agnostic access: Use Cloud PCs from Windows, macOS, iOS, Android, or browser-based clients, enabling work from virtually any device
- Simple deployment and management: Provision and manage Cloud PCs using Microsoft Intune and Endpoint Manager with no need for traditional VDI infrastructure
- BYOPC support: Extend secure access to personal or unmanaged devices without compromising control or compliance
- Workforce enablement: Onboard temporary workers or remote staff with secure, policy-controlled virtual desktops
Source: Microsoft
Related content: Read our guide to VDI alternatives
Conclusion
VDI platforms offer organizations a powerful way to centralize desktop management, enhance data security, and support a flexible, location-independent workforce. By hosting desktops in the data center or cloud, IT teams gain control over resources and policies while users benefit from consistent, secure access to their work environment. As business needs evolve and remote work remains prevalent, VDI platforms provide the infrastructure to scale, adapt, and maintain operational continuity across diverse work scenarios.