Best Browser Security Solutions: Top 5 Providers in 2025

What Are Browser Security Solutions?
Browser security solutions include remote work solutions like Venn and dedicated enterprise browsers like Island. These are enterprise-focused platforms that protect against browser-based threats like malware, phishing, and data leaks, by employing features such as sandboxing, real-time threat detection, granular policy enforcement, and the separation of work and personal activities.
By integrating security mechanisms directly into browsers or working alongside them, they serve as a critical defense layer for organizations and individual users alike, minimizing risks without relying solely on traditional endpoint or network security measures. The fast-evolving nature of browser threats, ranging from drive-by downloads to advanced phishing kits, requires security tools that react in real time and adapt to emerging attack methods.
Browser security solutions provide this by combining proactive monitoring, strict policy enforcement, and advanced containment techniques. Their role has become increasingly important as more work is conducted in cloud environments, SaaS applications, and remote workforces relying on web-based tools, making the browser a frequent target for cyber threats.
Go Beyond the Browser. Secure All Apps.
Learn how Venn secures both browser-based AND locally installed apps on unmanaged devices.

In this article:
Key Features of Browser Security Solutions
Real-Time Threat Detection and Policy Enforcement
Browser security solutions employ real-time threat detection engines to identify and block malicious activity as it happens. These systems analyze web traffic for known malware signatures, suspicious scripts, and abnormal behavior patterns. Policy enforcement is integrated to restrict access to high-risk sites, prevent data exfiltration, and ensure adherence to organizational security guidelines.
Continuous monitoring allows for dynamic responses to emerging threats. Policies can be updated or refined automatically based on evolving risk landscapes. By enforcing controls at the browser layer, organizations reduce the window of exposure and can manage security more granularly, down to specific user actions or applications. This flexibility is vital for organizations that support BYOD (Bring Your Own Device) policies and remote work.
Isolation and Sandboxing Techniques
A central feature of modern browser security solutions is the use of isolation and sandboxing. Isolation separates potentially risky website content from the endpoints, often using containerization or remote execution technologies. By rendering web pages in isolated environments, either on the endpoint or in the cloud, browser security tools prevent malicious code from reaching the local operating system or accessing sensitive data.
Sandboxing accomplishes a similar goal by creating tightly controlled environments where websites are executed. If a threat is encountered, it is confined to the sandbox and cannot impact the host device. These methods are particularly effective against zero-day vulnerabilities, as even unidentified exploits are less likely to escape these secure containers.
Privacy-First and Hardened Browsers
Privacy-first browsers are designed with built-in protections against tracking, fingerprinting, and data collection by default. Hardened browsers take this further by enforcing strict security configurations, disabling unnecessary features, and integrating advanced protections like anti-exploit and anti-phishing technologies. These browsers often limit third-party cookies, block intrusive scripts, and filter out advertisements that can carry malicious payloads.
By standardizing privacy and security-focused policies, organizations can ensure that user sessions are better protected from data leakage and invasive tracking techniques common across the web. Hardened browsers are particularly valuable in environments where compliance and confidentiality are critical, as they reduce the attack surface while providing controls for both IT teams and end users.
Secure Cookie Handling
Browser security solutions incorporate robust cookie management to prevent theft or misuse of session data. Secure cookie handling involves enforcing policies such as secure flags, HttpOnly attributes, and proper domain scoping for cookies. This prevents attackers from accessing cookies through cross-site scripting (XSS) or cross-site request forgery (CSRF) attacks.
Encryption and automatic cookie expiration further enhance protection, making it difficult for malicious actors to hijack sessions. Controlling and monitoring cookie usage helps mitigate risks associated with credential theft and unauthorized access. Security solutions may also provide visibility into which trackers and third-party cookies are present on visited sites.
Script and Clickjacking Protections
Malicious scripts and clickjacking attacks represent significant threats to browser security. Solutions that offer script protection can block or control the execution of JavaScript, preventing unauthorized code from running on trusted websites. These tools use a combination of allowlisting, behavioral analysis, and script isolation to thwart injection attacks and scripting exploits, including those sourced from compromised ad networks or embedded widgets.
Clickjacking protection works by detecting and blocking hidden frames or deceptive overlays designed to trick users into clicking on something unintended. These defenses typically involve monitoring page structure, enforcing frame-busting headers, and analyzing user interactions for suspicious patterns.
Notable Browser Security Solutions
1. Venn

Venn is a notable enterprise browser security solution for organizations that need to secure company data on unmanaged or BYOD computers. Unlike some of the other solutions below, Venn protects both browser-based and locally installed apps within a company-controlled Secure Enclave on the user’s device, delivering native browser and application performance without lag or latency. Venn runs apps locally on the endpoint while isolating them from personal activity. Blue Border™ visually distinguishes work from personal use, helping users stay productive while ensuring IT maintains control over business activity. Venn supports turnkey compliance with HIPAA, PCI, SOC, SEC, and FINRA, making it ideal for regulated industries with remote or contract-based workforces.
Key Features Include
- Secure Enclave technology: Encrypts and isolates work data on personal devices, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cute that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.

2. Island

Island is an enterprise-focused browser designed to integrate security, access control, and productivity features directly into the browsing experience. Unlike traditional add-on solutions, Island embeds security in the browser architecture, providing organizations with control over user actions, data access, and application behavior.
Key features include:
- Universal application access control: Enforces conditional access policies based on identity, device, and context directly in the browser
- Built-in security: Protects against malware, phishing, session hijacking, and man-in-the-browser attacks
- Context-aware data protection: Dynamically applies data controls based on user behavior and environmental risk
- User analytics: Provides visibility into browser activity for auditing and threat detection
- Privileged access management: Restricts and monitors access to sensitive systems and data
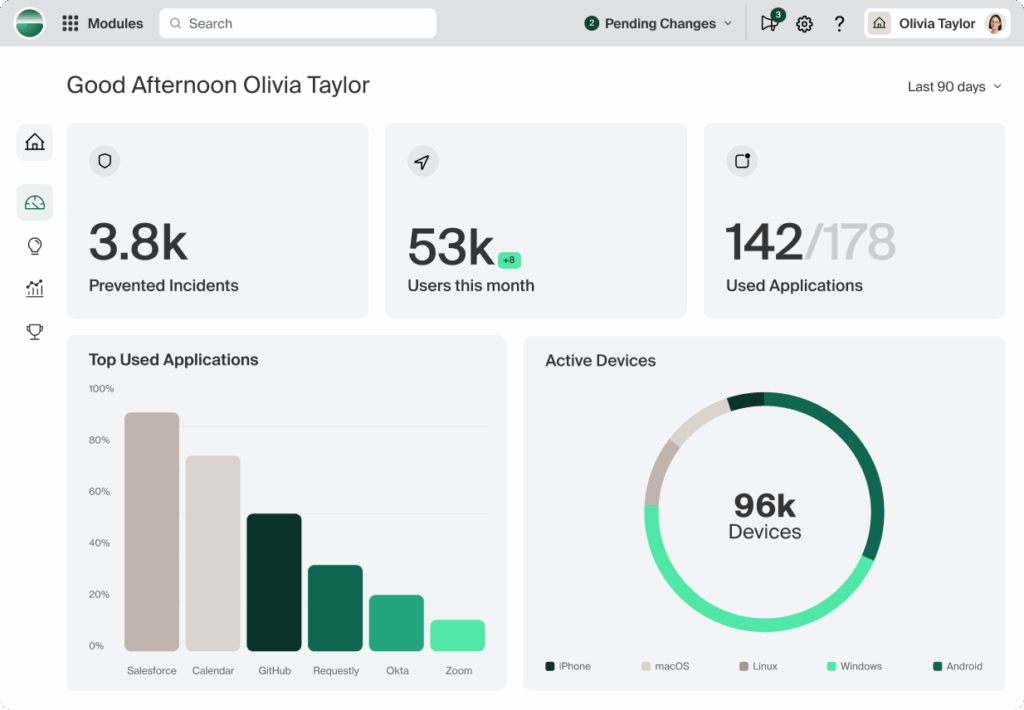
Source: Island
3. Prisma Access Browser

Prisma Access Browser by Palo Alto Networks is a secure enterprise browser natively integrated with SASE, built to protect both managed and unmanaged devices without requiring additional infrastructure. It enables secure access to corporate resources from personal or distributed endpoints by applying zero trust principles directly in the browser.
Key features include:
- SASE-native integration: Extends Prisma Access protection to the browser level with no additional agents or bolt-on tools
- Zero trust access enforcement: Applies contextual policies for identity, device, and application to control access from any location
- BYOD security: Secures access from personal devices while preventing data leakage through browser-based controls
- GenAI visibility and control: Monitors and restricts usage of GenAI tools to prevent unsanctioned data exposure
- Data controls: Manages user actions like copy/paste, screen sharing, and file transfers to prevent sensitive data loss
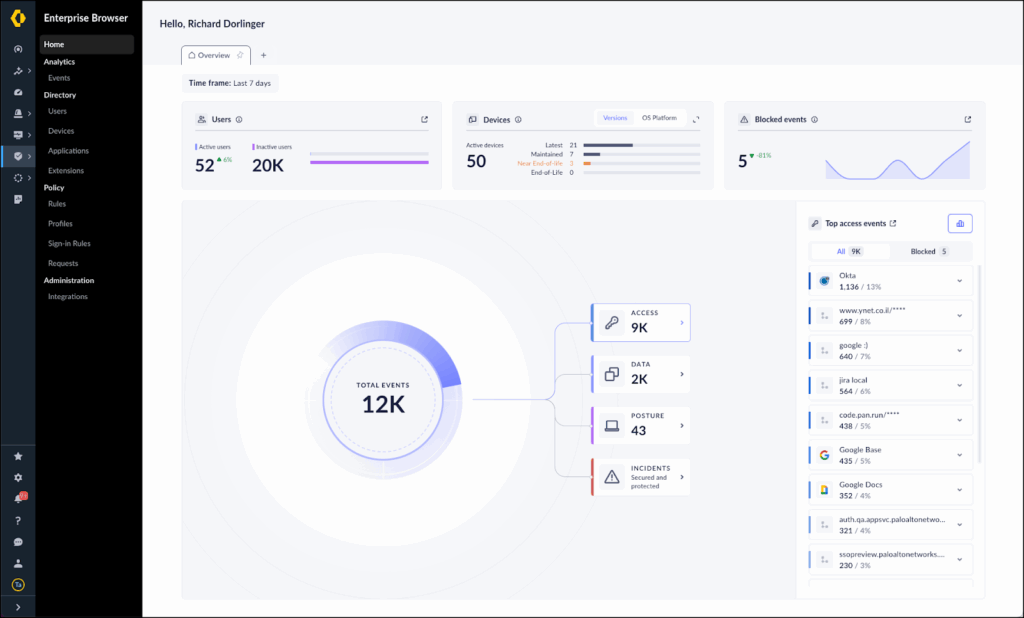
Source: Palo Alto Networks
4. Seraphic Security

Seraphic Security offers a browser-native protection platform that transforms mainstream browsers like Chrome, Edge, or Firefox into a secure enterprise-grade browser without changing the end-user experience. Rather than replacing the browser, Seraphic adds a lightweight agent that provides visibility and control within the browser environment.
Key features include:
- Bring your own browser (BYOB): Secures commonly used browsers without requiring users to switch or change browsing habits
- Threat prevention: Blocks phishing, malware, and browser-based attacks instantly without impacting performance
- Data protection: Controls actions like file uploads/downloads, copy-paste, screen sharing, and printing to prevent data leaks
- Browser visibility: Offers insights into browser activity for improved threat detection and policy enforcement
- Zero trust remote access: Enables secure access to enterprise applications from any device, location, or browser, no VPN or VDI needed
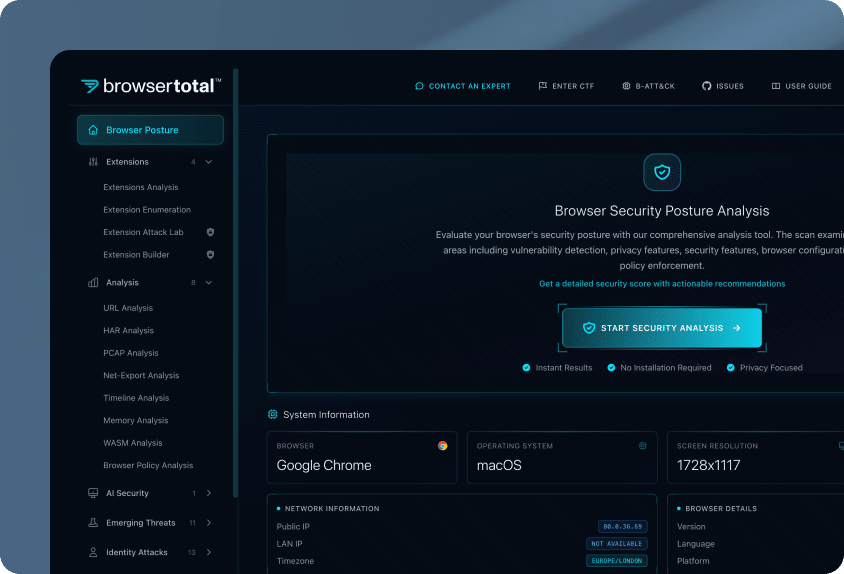
Source: Seraphic Security
5. Check Point Harmony Browse

Check Point Harmony Browse is a lightweight, enterprise browser extension that delivers protection against web threats across both managed and unmanaged devices. Designed to integrate into existing environments, it blocks phishing attacks, prevents data leakage, and neutralizes malware through multi-layered threat prevention.
Key features include:
- Phishing prevention: Actively blocks advanced phishing attempts before users can interact with malicious content
- Data loss prevention (DLP): Controls data sharing, including uploads, clipboard use, and GenAI interactions, to ensure sensitive data stays secure
- Multi-layer malware protection: Uses sandboxing and content disarm & reconstruction (CDR) to scan and sanitize files in 1.5 seconds or less
- GenAI security controls: Prevents unauthorized data input into AI tools and offers visibility into usage patterns
- Lightweight deployment: Easy to install across any device and browser, with minimal impact on performance

Source: Check Point
Related content: Read our guide to browser security tools (coming soon)
Conclusion
Remote work and browser security solutions strengthen enterprise defenses by securing the primary environment where most work now occurs: the browser. They combine real-time detection, isolation, policy enforcement, and data protection to mitigate risks that traditional endpoint and network security often miss. As organizations expand reliance on SaaS, remote work, and BYOD, these solutions provide the visibility and control needed to reduce browser-based attack surfaces while supporting flexible, cloud-first operations.