Top 13 Secure Browsers and Browser Security Alternatives in 2026

What Is a Secure Browser?
A secure browser is a web browser with built-in features that protect users’ online privacy and security, such as blocking trackers, preventing digital fingerprinting, and providing tools to control personal information.
Secure browsers are popular among users who want greater control over their browsing privacy, or organizations that need to ensure users are not exposed to cybersecurity threats. Rather than relying solely on third-party extensions for security, these browsers harden protections at the core code level, delivering risk mitigation.
Key features of secure browsers include:
- Tracker blocking: Prevents websites from tracking your online activity and collecting your data.
- Fingerprint protection: Stops websites from identifying you through unique browser settings and characteristics.
- Data control: Gives users tools to manage and control their personal information and online habits.
- Protection against malicious sites: Blocks dangerous and deceptive websites that may try to steal passwords or install malware.
- HTTPS enforcement and TLS 1.3: Automatically upgrades connections to encrypted HTTPS and uses modern cryptographic protocols to secure data in transit.
- Anti-phishing and anti-malware protection: Identifies and blocks access to fraudulent websites and malicious downloads using real-time threat intelligence.
- WebRTC and IP leak prevention: Prevents unintentional exposure of your real IP address or network data, especially when using VPNs.
- Cookie and tracking script controls: Offers fine-grained tools to block, isolate, or auto-delete cookies and disable invasive tracking scripts.
This article will cover the following categories of browser security technologies:
- BYOD management: Organizations with bring-your-own-device (BYOD) policies often secure browser activity by controlling device-level access rather than the browser itself. This involves applying security baselines, Conditional Access, and app-level protections using tools like Venn, Microsoft Intune, or Workspace ONE.
- Browser security extensions: For environments using standard browsers, security can be enhanced with extensions like uBlock Origin and Bitdefender TrafficLight. These tools block ads, trackers, phishing domains, and malware, offering layered protection without replacing the browser.
- Consumer-focused secure browsers: Browsers like Brave, Firefox, and DuckDuckGo provide privacy-by-default features such as tracker blocking, HTTPS enforcement, and minimal telemetry. These tools appeal to individual users and small teams prioritizing usability and control.
- Enterprise-focused secure browser platforms: Solutions like Island, Seraphic, and Prisma embed data controls, session isolation, and security policies directly into the browser environment. They offer visibility into user activity, integrate with zero trust frameworks, and support both managed and unmanaged endpoints.
Go Beyond the Browser. Secure All Apps.
Learn how Venn secures both browser-based AND locally installed apps on unmanaged devices.

In this article:
How Secure Browsers Differ from Standard Browsers
Secure browsers separate themselves from standard browsers by integrating privacy and security features as fundamental components rather than add-ons or optional settings. This includes enforcing stricter anti-tracking, anti-phishing, and sandboxing operations that are effective by default, without requiring manual configuration from users. Standard browsers typically offer some privacy options, but their focus is often on ease of use and wide compatibility, sometimes at the expense of underlying security.
Additionally, secure browsers update more aggressively, often with a faster release schedule for security fixes. They actively minimize data collection, limit the sharing of browsing statistics, and prevent websites from discovering device details that could be used for fingerprinting. Some secure browsers choose to restrict the use of browser plugins or scripting technologies, providing a safer environment out of the box compared to default mainstream browser builds.
Key Features of Secure Browsers
Tracker Blocking
Tracker blocking is a fundamental security feature in modern secure browsers. It prevents third-party entities from following your browsing habits across the internet. Most secure browsers rely on maintained blocklists, heuristics, or machine learning to automatically identify and stop web trackers, ad beacons, and social media pixels that collect user data without consent.
Effective tracker blocking helps pages load faster by eliminating unnecessary scripts and network requests. This reduces the likelihood of malware exposure since malicious ads and trackers are a leading vector for drive-by attacks. By isolating or blocking trackers, secure browsers help ensure users’ web footprints stay private and their devices remain protected against unwanted intrusion.
Fingerprint Protection
Unlike cookies, browser fingerprinting uses information about the user’s device, configuration, and software to create a unique profile. Secure browsers mitigate this by randomizing certain attributes or minimizing the amount of information exposed to websites. Techniques include spoofing screen resolutions, language settings, and plugin lists, which helps to obscure the browser’s unique fingerprint.
Fingerprint protection is critical as fingerprinting occurs silently, often without the user’s knowledge or ability to control it. Secure browsers work on limiting or standardizing browser characteristics so that users blend in with others. This approach reduces the effectiveness of tracking based on distinctive setups and makes persistent cross-site identification significantly more difficult.
Data Control
Secure browsers prioritize giving users detailed control over how their data is collected, stored, and shared. This includes options to disable telemetry, block third-party cookies by default, and configure privacy-focused settings such as clearing data on exit or disabling persistent storage. Many secure browsers also support containerized tabs or isolated profiles, allowing users to compartmentalize their browsing activity and limit cross-site tracking.
Beyond basic settings, advanced data control features include built-in dashboards that show who is tracking you, what data is being stored, and how it is being used. Users can manually delete cookies, local storage, and cached data per site, as well as revoke permissions granted to sites, such as access to camera, microphone, or location.
Protection Against Malicious Sites
Secure browsers actively defend against malicious sites by combining threat intelligence feeds with in-browser heuristics that evaluate risk. When a user attempts to visit a known phishing or malware-distributing domain, the browser will intervene with a full-page warning, advising the user to avoid proceeding. These checks are constantly updated in the background to include new threat indicators and attack vectors as they emerge.
In addition to static blocklists, some secure browsers employ real-time scanning techniques to detect anomalies in page content, such as obfuscated JavaScript or suspicious redirects. This adaptive protection guards against newly registered or compromised domains that may not yet be denylisted, offering broader defense coverage against zero-day and polymorphic threats.
HTTPS Enforcement and TLS 1.3
Enforcing HTTPS ensures that all connections between the browser and websites are encrypted, providing confidentiality and integrity for transmitted information. Secure browsers can automatically upgrade non-secure HTTP connections to HTTPS when possible. This prevents eavesdropping, tampering, and man-in-the-middle attacks, which are particularly important on public or untrusted networks.
Support for the latest encryption standards, such as tls 1.3, is another hallmark of secure browsers. TLS 1.3 removes obsolete and insecure cryptographic algorithms, reducing opportunities for attackers to intercept or decrypt traffic. By defaulting to secure protocols, these browsers protect sensitive data, such as passwords and personal messages, during every browsing session.
Anti-Phishing and Anti-Malware Protection
Secure browsers incorporate active anti-phishing mechanisms that analyze webpages and block access to known fraudulent or malicious sites. These defenses combine continuously updated threat databases with real-time scanning of web content to identify phishing attempts, malicious scripts, or fake login forms. Pop-up warnings or automatic redirects prevent users from inadvertently sharing personal credentials with attackers.
Anti-malware protection goes a step further by scanning downloads and web resources for malicious code or behaviors. Many secure browsers work in partnership with security services or maintain their own threat intelligence feeds. Combined, these built-in modules help prevent infection from malicious downloads or drive-by exploits, providing a line of defense for safe browsing.
WebRTC and IP Leak Prevention
WebRTC is a browser feature that supports real-time video and audio communication between users, but it can reveal a user’s real IP address in the presence of VPNs. Secure browsers address this risk by offering controls to disable WebRTC or to isolate it behind network security rules, ensuring that user IP addresses are not leaked through inadvertent browser behavior.
IP leak prevention also includes mechanisms to block DNS and other network requests that could bypass VPNs or proxies. By tightly controlling the browser’s network stack, secure browsers make sure that all outgoing connections respect privacy configurations, preserving both anonymity and data security across browsing sessions.
Cookie and Tracking Script Controls
Cookie control is central to protecting user privacy, especially as many trackers rely on persistent or third-party cookies to follow users across sites. Secure browsers offer granular settings to block, expire, or selectively allow cookies for specific sites. Some browsers isolate cookies between tabs or browsing sessions, preventing data from being shared outside of its intended context.
Managing tracking scripts, a common method for embedding surveillance code into webpages, is also critical. Secure browsers provide built-in script blockers or strict content security policies that prevent unauthorized scripts from running. This minimizes both the collection of personal information by trackers and the risk that malicious scripts could compromise browser security.
Architecture of a Secure Browser
Here are the main technical components at the basis of secure browser solutions.
Multi-Process Isolation and Sandboxing
A secure browser uses multi-process isolation to separate webpage processes from each other and from core browser functionality. This means that if a malicious site exploits a vulnerability in one tab, it cannot easily access information or resources in other tabs or escape to affect the rest of the system. Each site runs in its own container with clearly defined permissions.
Sandboxing complements this by restricting what each isolated process can do. Browsers set up virtual boundaries around processes, preventing them from reading or writing files, accessing hardware, or running arbitrary code outside of the browser. Combined, these technologies reduce the impact of zero-day exploits and help confine attacks to a minimal footprint.
Security Policy Engines and Trusted UI Layers
Security policy engines are responsible for enforcing rules regarding what each website or extension is allowed to do in a browser environment. For example, they prevent websites from accessing unauthorized APIs, launching unsanctioned downloads, or triggering sensitive browser functions. This central point of control allows secure browsers to adapt rapidly to new threats by rolling out updated policies without requiring software updates.
Trusted UI layers further protect users by ensuring that prompts, warnings, and security dialogs are authentic and untampered. By isolating user interface elements used for passwords, permissions, or payments, browsers make it nearly impossible for sites to spoof or intercept critical actions. This dual approach defends users both at the system and interaction layers.
Secure Extension Management
Extensions expand browser functionality but often introduce security and privacy risks. Secure browsers address this challenge by curating extension marketplaces, restricting the permissions available to extensions, and requiring rigorous code reviews before publishing. They may also allow users to manually approve or deny sensitive extension permissions on a per-site basis.
To further limit risk, many secure browsers isolate extension processes from browser tabs and the core engine. This means a compromised extension has limited scope for harm, and data access is strictly controlled. Some browsers automatically disable extensions during sensitive activities like private browsing, reducing exposure to potential spying or data leakage via third-party code.
Hardware-Assisted Browser Security (TPM)
Secure browsers leverage hardware security modules, such as Trusted Platform Modules (TPM), to protect encryption keys and sensitive computations. By delegating critical security operations to hardware components, browsers make it highly resistant to theft or tampering, even if the operating system is compromised, attackers cannot easily access protected secrets.
This hardware-layer protection extends to processes like biometric authentication, digital certificate handling, and storage of encryption credentials used for visiting secure sites. Integrating with TPM or secure enclave technology raises the bar for attackers, providing security that cannot be bypassed by software-only exploits and adding an extra layer of confidence for high-value or sensitive data use cases.
4 Categories of Secure Browser Technologies
Secure browser solutions can be grouped into four distinct categories based on how they deliver protections and manage risk: BYOD management, browser security extensions, consumer-focused secure browsers, and enterprise-focused secure browser platforms.
1. BYOD Management
This approach secures browser activity on personal devices without managing the entire device. It creates isolated workspaces where organizational policies apply, enforcing data protection, app controls, and access restrictions. Security is enforced locally or through cloud-based policy engines, keeping corporate data separate from personal content. This model is ideal for organizations supporting hybrid or contractor-heavy workforces where device ownership cannot be standardized.
2. Browser Security Extensions
Security extensions run inside mainstream browsers to provide additional defenses such as ad blocking, phishing protection, or script control. These are widely used in environments where replacing the default browser is not feasible. They offer flexibility but rely on the integrity of the host browser and are limited by its extension APIs. Effective as a first layer of defense, extensions are often used in combination with endpoint security tools.
3. Consumer-Focused Secure Browsers
These browsers are designed with default privacy and security settings that require minimal user configuration. They include built-in tracking protection, script blockers, and cookie isolation. Intended for individuals or small teams, they emphasize usability while reducing the need for third-party extensions. Updates and privacy enhancements are prioritized over full enterprise manageability or integration.
4. Enterprise-Focused Secure Browser Platforms
These platforms embed policy enforcement, data loss prevention, and access controls directly into the browser. They are built for managed and unmanaged environments, providing visibility and centralized governance over user activity. Some integrate with zero trust architectures, support advanced threat prevention, and extend protections to AI tools or unmanaged devices. They are used to replace or supplement traditional VDI or VPN models with a browser-native alternative.
BYOD Management
1. Venn

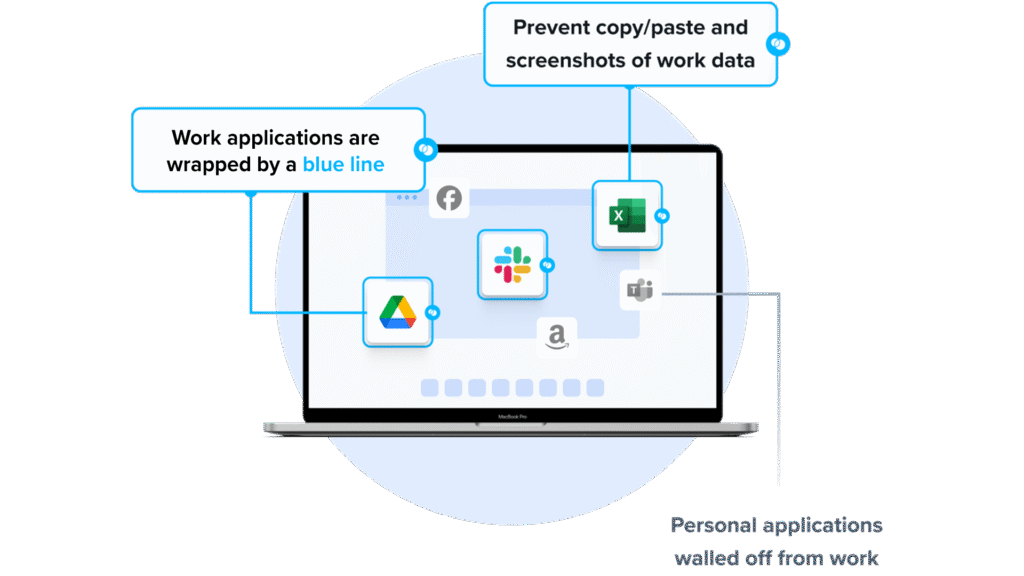
Venn’s Blue Border was purpose-built to protect company data and applications on BYOD computers used by contractors and remote employees.
Similar to an MDM solution but for laptops, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy. With Venn, you can eliminate the burden of purchasing and securing laptops and managing virtual desktops (VDI).
Key features include:
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
2. Microsoft Intune

Microsoft Intune provides BYOD update and access controls for personal Android and iOS/iPadOS devices. Administrators set enrollment restrictions, enforce compliance baselines, apply Conditional Access, and use app protection to gate access on unmanaged devices. Custom notifications inform users about required OS versions and upcoming deadlines.
Key features include:
- Enrollment restrictions: Enforce minimum and maximum OS versions during enrollment, blocking personal devices outside policy to establish a consistent baseline.
- Compliance policies and reporting: Mark out-of-date devices noncompliant, use built-in reports to identify gaps, and apply grace periods before enforcement begins.
- Conditional Access enforcement: Combine compliance with Conditional Access to block resource access until devices meet required OS versions defined by administrators.
- App protection policies: On unmanaged devices, require minimum OS and patch levels at app launch, prompting upgrades or blocking access when versions lag.
- Custom notifications: Send targeted messages about upcoming OS requirements so users update proactively when forced updates are not possible on BYOD.
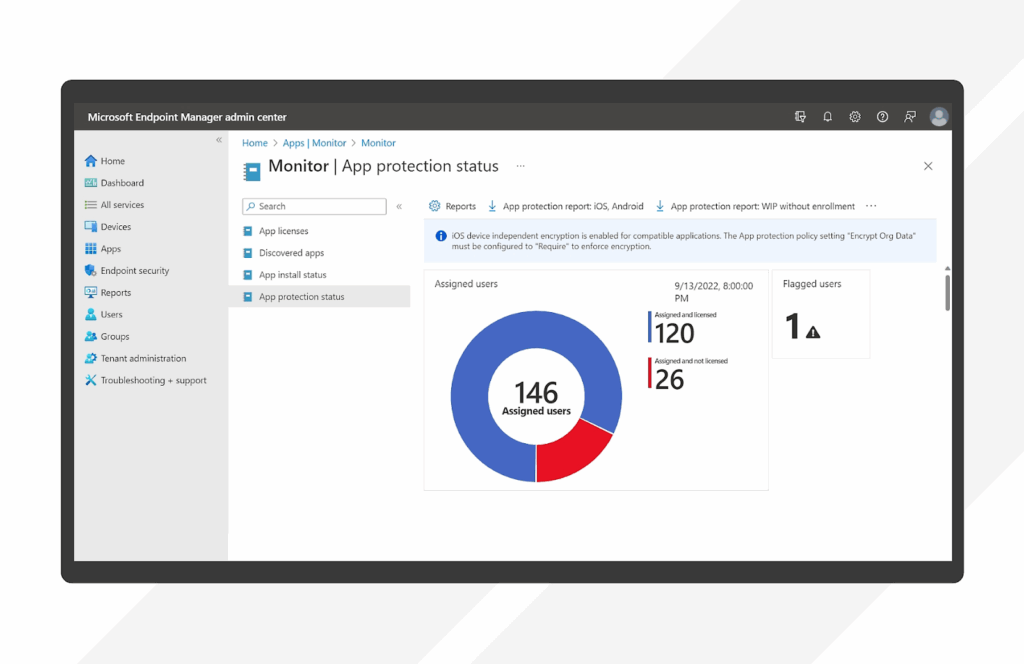
Source: Microsoft
3. Workspace ONE

Workspace ONE UEM is a cloud-native unified endpoint management platform. It centralizes management for any device or ownership model and applies zero trust controls. Multi-tenant architecture, low/no-code orchestration, lifecycle management, and role-based access support large, distributed environments with varied use cases, including BYOD and shared devices.
Key features include:
- Multi-tenant architecture: Define and inherit policies across organizational levels, enabling granular control with the option to override settings when necessary.
- IT orchestration: Automate complex, time-consuming tasks through an easy-to-use low/no-code platform, standardizing operational workflows across device fleets.
- Zero trust security: Assess compliance and behavioral anomalies before granting access, with options to deny, remediate, or wipe devices based on policy.
- App lifecycle and catalog: Deliver applications with a unified self-service catalog and single sign-on, supporting desktop and mobile app distribution and updates.
- Remote onboarding: Provision new devices without imaging, enabling zero-touch setup so employees can start from anywhere with required configurations applied.
Source: Omnissa
Browser Security Extensions
4. Bitdefender TrafficLight

Bitdefender TrafficLight is a free, cross-browser add-on that intercepts and filters web traffic. It blocks pages carrying phishing or malware threats, identifies trackers, and scans links. Inspection occurs at browse time to prevent access to dangerous content.
Key features include:
- Web traffic interception: Processes and filters all browser traffic, blocking malicious content before rendering to reduce exposure to drive-by and embedded threats.
- Phishing protection: Evaluates visited pages in real time and blocks credential-stealing sites, reducing risk from deceptive login and payment pages.
- Malware filtering: Analyzes requested resources and prevents downloads of known malicious files directly within supported browser environments.
- Tracker identification: Detects tracking elements on pages and surfaces their presence, improving visibility into embedded surveillance components.
- Link scanning: Flags search results and embedded links with safety indicators, helping users avoid risky destinations before clicking through.
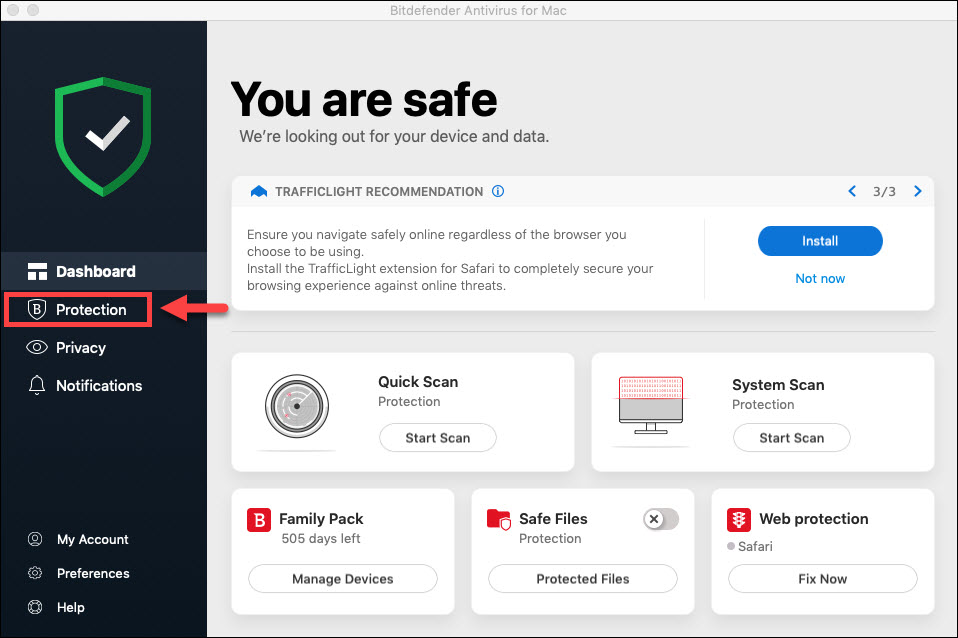
Source: Bitdefender
5. uBlock Origin

uBlock Origin is a free, open-source, wide-spectrum content blocker emphasizing CPU and memory efficiency. It filters ads, trackers, and malicious domains before they load. The project is actively maintained, supports multiple browsers, and offers options for Manifest V3 environments through uBlock Origin Lite.
Key features include:
- Wide-spectrum blocking: Blocks ads, trackers, and unwanted requests efficiently, reducing page noise by filtering network activity before content is rendered.
- Cross-browser support: Available for Chrome/Chromium, Microsoft Edge, Opera, and Firefox, with compatibility for Safari versions prior to 13.
- Manifest V3 adaptations: Addresses MV3 limitations by offering uBlock Origin Lite using declarativeNetRequest rules within Chrome’s revised extension model.
- Open-source development: Actively maintained by Raymond Hill under GPL-3.0, with public source code, issue tracking, and documentation on GitHub repositories.
- Filter lists and rules: Uses community-maintained lists like EasyList and EasyPrivacy, plus malicious URL blocklists, with support for custom user filters.
Consumer-Focused Secure Browsers
6. Brave

Brave is a secure browser focused on user privacy and performance by default, without requiring any configuration. It blocks ads and trackers out of the box, reducing page load times and limiting data exposure. Unlike traditional browsers, Brave doesn’t rely on third-party extensions for core privacy functions. Instead, features like ad blocking, tracking protection, and anonymous browsing are integrated into its foundation.
Key features include:
- Default ad and tracker blocking: Automatically stops invasive scripts and third-party trackers, improving privacy and performance.
- Private search engine: Brave Search delivers results without profiling users or storing search histories.
- Firewall + VPN: Secures internet traffic across all apps and services on the device, not just the browser.
- Built-in security by default: No need for additional extensions; security and privacy protections are preconfigured and always on.
- AI assistant (Leo): Operates within the browser to provide assistance while respecting privacy controls.
Source: Brave
7. Google Chrome

Google Chrome Enterprise is a managed version of Chrome for business environments, offering centralized policy control, enterprise integrations, and security features. It builds on the familiar Chrome experience but adds administrative tools for managing browser settings, extensions, and user behavior across devices and platforms.
Key features include:
- Safe browsing protections: Blocks access to known malicious and phishing websites in real time to protect users from online threats.
- Extension management: Controls extension installations and permissions, reducing exposure to unvetted third-party code.
- Malware deep scanning: Analyzes unknown or high-risk files for potential threats before they reach the user.
- Password protections: Prevents reuse of corporate credentials across websites, helping to limit the impact of password leaks.
- Data loss prevention (Premium): Enforces granular DLP policies to reduce accidental or intentional data exfiltration.
Source: Google Chrome
8. Mozilla Firefox

Mozilla Firefox is a privacy-focused browser intended to give users speed, control, and security without sacrificing usability. Developed by Mozilla, a nonprofit organization, Firefox blocks third-party trackers by default, reducing load times and limiting background surveillance. Unlike browsers that monetize user data, Firefox collects minimal information and provides accessible privacy policies.
Key features include:
- Default tracker blocking: Stops third-party cookies and trackers automatically to reduce surveillance and improve speed.
- Minimal data collection: Stores only basic technical information, avoiding unnecessary personal data that could be exposed in a breach.
- Frequent security updates: Keeps users protected with the latest security technology and patches vulnerabilities quickly.
- Mozilla Monitor: Notifies users if their email appears in known data breaches and helps track past security incidents.
- Secure connection indicators: Uses a green lock icon to show when websites are encrypted, helping users avoid insecure connections.

Source: Mozilla Firefox
9. DuckDuckGo

DuckDuckGo is a privacy-focused browser and search engine that aims to stop online tracking and data collection at the source. Unlike traditional browsers that require manual configuration or paid add-ons for privacy, DuckDuckGo blocks third-party trackers, targeted ads, and cookie pop-ups by default.
Key features include:
- Third-party tracker blocking: Automatically stops trackers from companies like Google and Facebook across websites.
- Ad and cookie pop-up blocking: Prevents most ads and cookie notices from loading, minimizing interruptions and data exposure.
- One-click data deletion: Clears all tabs, history, and browsing data instantly with a single action.
- Private search and chat: Built-in DuckDuckGo Search offers anonymous queries; optional support for private AI chatbot use.
- Email and identity protection: Blocks email trackers and helps remove personal data from data broker sites.
Source: DuckDuckGo
Enterprise-Focused Secure Browsers
10. Island Enterprise Browser

Island Enterprise Browser embeds security, networking, data protection, and identity controls directly into the browser. It provides policy-driven access to applications, blocks phishing and data leakage, accelerates contractor onboarding, enables BYOD, and gives administrators visibility into organization-wide browsing activity.
Key features include:
- Built-in enterprise controls: Integrates security, networking, data protection, and identity within the browser, removing dependence on external add-ons.
- Policy-driven app access: Enforces granular policies for accessing SaaS and internal applications, aligning browsing activity with enterprise governance.
- Threat and data protection: Blocks phishing, malware, and data leakage at the browser layer to secure everyday user interactions with web resources.
- Contractor and BYOD support: Onboards third parties quickly and enables personal devices while maintaining administrative control over data handling.
- Activity visibility: Provides organization-wide insight into browsing activity to monitor use and apply zero trust-aligned enforcement consistently.
Source: Island
11. Seraphic Security

Seraphic Security is a browser security platform that adds enterprise controls to any standard or AI-enabled browser. A single agent provides real-time threat prevention, data controls, AI governance, and secure remote access without VPN or VDI. It supports managed, BYOD, VDI, and third-party devices.
Key features include:
- Single agent, any platform: Deploy once to secure Chrome, Edge, Firefox, Safari, and Electron-based apps across managed, BYOD, and third-party endpoints.
- Real-time threat prevention: Block phishing, malware, and advanced browser-borne attacks without traffic backhauling, minimizing latency and user disruption.
- Granular data controls: Enforce policies on uploads, downloads, clipboard, screen sharing, and printing to reduce data exfiltration across browser workflows.
- AI visibility and guardrails: Monitor AI interactions, restrict sensitive data sharing, and mitigate prompt injection and shadow AI risks within browser sessions.
- Secure remote access: Provide identity-aware, browser-level access to corporate apps without VPN or VDI, enforcing policy directly in the session.
Source: Seraphic Security
12. Prisma Browser

Prisma Browser is a secure enterprise browser natively integrated with Prisma SASE. It applies zero trust access and granular data controls across managed and unmanaged devices. Use cases include securing independent workers, governing GenAI usage, and reducing reliance on VDI by enabling secure, policy-enforced application access.
Key features include:
- SASE-native integration: Extends Prisma SASE protections directly into the browser, unifying policy enforcement with existing cloud-delivered security.
- Zero trust access: Applies identity-based access policies and fine-grained data controls to secure remote work for employees, contractors, and BYOD.
- Managed and unmanaged coverage: Delivers consistent protections and visibility across corporate endpoints and personal devices without separate tooling.
- GenAI usage governance: Adds visibility and controls for activity within GenAI applications, limiting shadow AI and reducing sensitive data exposure.
- VDI reduction: Enables secure work in applications inside the browser, lowering dependence on traditional VDI while maintaining centralized control.
Source: Palo Alto Networks
13. Check Point Enterprise Browser

Check Point Enterprise Browser is a secure, Chromium-based browser providing controlled access from unmanaged devices. It isolates corporate sessions, enforces DLP, verifies device posture without an agent, and records detailed session activity. Sensitive data is cleared at session end to reduce endpoint risk.
Key features include:
- Strong data isolation: Segregates corporate browsing activity from the host environment to prevent unauthorized transfers between enterprise and personal contexts.
- Integrated DLP controls: Restricts uploads, downloads, clipboard, printing, and screen capture, with options like on-screen watermarking for deterrence.
- Agentless posture checks: Verifies device security posture before granting access, avoiding persistent agents on personal or contractor devices.
- Session visibility and auditing: Captures activity logs for compliance and investigations, maintaining oversight of high-risk actions during sessions.
- Isolated workspace: Runs corporate sessions in a contained Chromium-based environment and clears sensitive data when sessions end on the device.
Source: Check Point
Best Practices for Secure Browser Configuration
Here are some best practices for individuals and organizations seeking to improve their browser security, whether they use consumer-focused or enterprise-focused secure browsers.
Disable Third-Party Cookies
Disabling third-party cookies is a technique to reduce tracking across the internet. By blocking cookies set by domains other than the one the user is actively visiting, you deny advertisers and data brokers the means of building detailed profiles over time. Secure browsers typically allow this setting or enforce it by default.
Beyond privacy concerns, blocking third-party cookies also improves security by reducing the risk that malicious code could leverage tracking scripts to initiate attacks. It is a way to harden the browser without significant usability trade-offs, especially as more sites move away from reliance on third-party cookies for core functionality.
Enforce Strict Site Isolation
Strict site isolation ensures that each website runs in a separate browser process. This means a malicious site can’t read or interfere with data loaded from another website, providing defense against cross-site scripting (XSS) and side-channel attacks like Spectre and Meltdown. Enabling site isolation is a best practice for organizations that handle multiple sensitive workflows.
Users benefit from site isolation as it helps contain security breaches. Even if a compromise occurs, site-specific process boundaries prevent attackers from hopping between sessions or stealing authentication tokens for other services. This setting is especially critical for high-risk users dealing with corporate, financial, or medical data in the browser.
Control Browser Extensions and Plugins
Controlling which extensions and plugins are installed, and what permissions they have, is essential for a secure browsing environment. Each extension introduces potential vulnerabilities, and some have been found to collect or leak sensitive data. Regularly auditing granted permissions and disabling unnecessary extensions reduces risk.
Secure browsers may limit what extensions can do by default, sandbox their execution, and prevent them from running during private sessions. Users should prioritize extensions from trusted sources with transparent policies, keeping their extension list as short and purpose-specific as possible to minimize attack surface.
Use Privacy-Focused Search Engines
Setting the default search engine to a privacy-focused provider, such as DuckDuckGo or Startpage, complements browser-based defenses. These search engines don’t log users’ queries, track searches over time, or build user profiles for advertising purposes. Switching search engines is a low-effort, high-impact way to cut down on web tracking.
Integrating a private search engine aligns all browser-driven queries with end-to-end privacy policies. Combined with secure browser features, this prevents both search providers and intermediaries from harvesting data or correlating searches with user identities, offering a more confidential browsing experience throughout the user’s workflow.
Update Frequently and Verify Build Integrity
Maintaining a secure browser requires regular updates, as vulnerabilities are discovered and patched continuously. Secure browsers often have automated update features, but users and organizations should still verify that updates are happening and confirm the authenticity of downloaded browser builds. Signing and checksum verification protect against supply chain attacks.
Verifying build integrity is particularly important in enterprise and regulated environments. Malware-laden builds or compromised update channels could undermine all other security practices. By regularly updating and checking that binaries are legitimate and untampered, users protect themselves from emerging threats and ensure the browser’s security protections remain effective.
Related content: Read our guide to browser security best practices
Conclusion
Secure browsers serve as a critical line of defense in an environment where online threats and privacy intrusions are constantly evolving. By embedding protections like tracker blocking, data isolation, and real-time threat detection directly into their architecture, these browsers reduce reliance on user configuration or third-party tools.
While secure browsers provide robust built-in defenses, organizations and individuals should also consider complementary security strategies. Combining secure browsers with trusted hardware features and endpoint-level controls creates a more resilient security posture across diverse threat scenarios.