Secure Remote Access Solutions: Key Features and Top 5 Tools in 2025

What Are Secure Remote Access Solutions?
Secure remote access solutions enable users to connect to a network or system from a remote location while ensuring the confidentiality and integrity of data and resources. These solutions typically involve a combination of technologies like VPNs, multi-factor authentication (MFA), and endpoint security, working together to create a secure connection.
They typically combine authentication, encryption, access controls, and continuous monitoring to ensure that only authorized individuals can reach sensitive resources, regardless of where they are located. The goal is to support productivity and flexibility without compromising security, ensuring compliance with various regulations and organizational policies at all times.
Enable Remote Workers Without VDI or Issuing Devices
Secure your entire extended workforce without issuing devices or VDI. Keep your organization agile, compliant, and secure.

In this article:
Key Features of Secure Remote Access Solutions
Granular Access Control and Least Privilege
Granular access control is essential in secure remote access, as it allows administrators to define detailed rules governing who can access specific resources. This fine-tuned control reduces the attack surface by restricting access to only what is absolutely necessary for each user or group, based on their role, location, or device. Policies are often dynamic, adapting to changing risk factors such as login time, device status, or user behavior.
The principle of least privilege is closely intertwined with granular access control. By ensuring users and systems operate with only the permissions required to perform their tasks, organizations minimize the potential damage of compromised accounts or insider threats. Implementation of least privilege also makes it easier to audit and review permissions.
Encryption
Encryption is a cornerstone of secure remote access, as it protects data in transit between endpoints and corporate resources. By encrypting traffic, typically using protocols such as TLS or IPsec, organizations prevent attackers from intercepting sensitive information such as credentials, internal communications, or intellectual property. Strong encryption ensures confidentiality even if internet channels or intermediary networks are not trusted.
Beyond transit encryption, some solutions also support persistent encryption for sensitive files or communications, ensuring that data remains secure even outside the immediate connection. This layer of defense significantly reduces the risk of data breaches and is often necessary to comply with regulations like GDPR, HIPAA, or PCI-DSS.
Comprehensive Logging and Monitoring
Comprehensive logging and monitoring provide visibility into all remote access activities. Secure remote access solutions should generate detailed logs of connection attempts, successful authentications, resource access, and policy enforcement actions. This level of detail assists security teams in detecting abnormal behavior, investigating security incidents, and maintaining an audit trail for compliance purposes.
Effective monitoring also enables real-time alerts and automated responses to suspicious activities. By actively scanning for unusual login patterns, unauthorized access attempts, or deviations from typical usage, organizations can quickly respond to threats and mitigate risks before they escalate into larger incidents.
Zero Trust Network Access
Zero Trust Network Access (ZTNA) represents a modern shift from traditional perimeter-based security models. It assumes no inherent trust for users or devices, requiring continuous verification every time access to a resource is requested. ZTNA applies strict identity validation, device health checks, and context-driven access policies, regardless of whether a user is inside or outside the corporate network.
This approach mitigates lateral movement threats, where attackers attempt to expand their access within a network after initial compromise. By granting access only to explicitly authorized resources based on verified criteria, ZTNA reduces the potential for internal threats, privilege escalation, or data exfiltration commonly seen in breaches of legacy VPN-based architectures.
Endpoint Protection
Endpoint protection is vital, as compromised user devices can serve as gateways for attackers. Secure remote access solutions often integrate endpoint security checks, ensuring devices are free of malware, have updated software, and conform to security policies before allowing access. This reduces the risk that an attacker could leverage an insecure laptop or smartphone to gain network entry.
Many solutions extend endpoint protection by enforcing security posture even after access is granted. Features such as remote isolation, file access controls, and monitoring of risky behaviors prevent data loss or exploitation of vulnerabilities. Incorporating endpoint protection into remote access workflows is crucial for organizations that permit (BYOD) arrangements.
Scalability and Performance
Scalability is a critical requirement for remote access solutions in modern organizations, as remote workforces and resource demands can fluctuate rapidly. Effective solutions must handle increases in user volume without causing service degradation or introducing new security bottlenecks. This often involves elastic cloud-based architectures, load balancing, and session management capabilities.
Performance is equally important; remote access should not create noticeable latency or reduced functionality for users. Modern solutions leverage optimized protocols, intelligent routing, and caching to ensure that users obtain reliable, fast, and seamless connections to needed resources.
Read our guide to remote work solutions
Notable Secure Remote Access Solutions
1. Venn

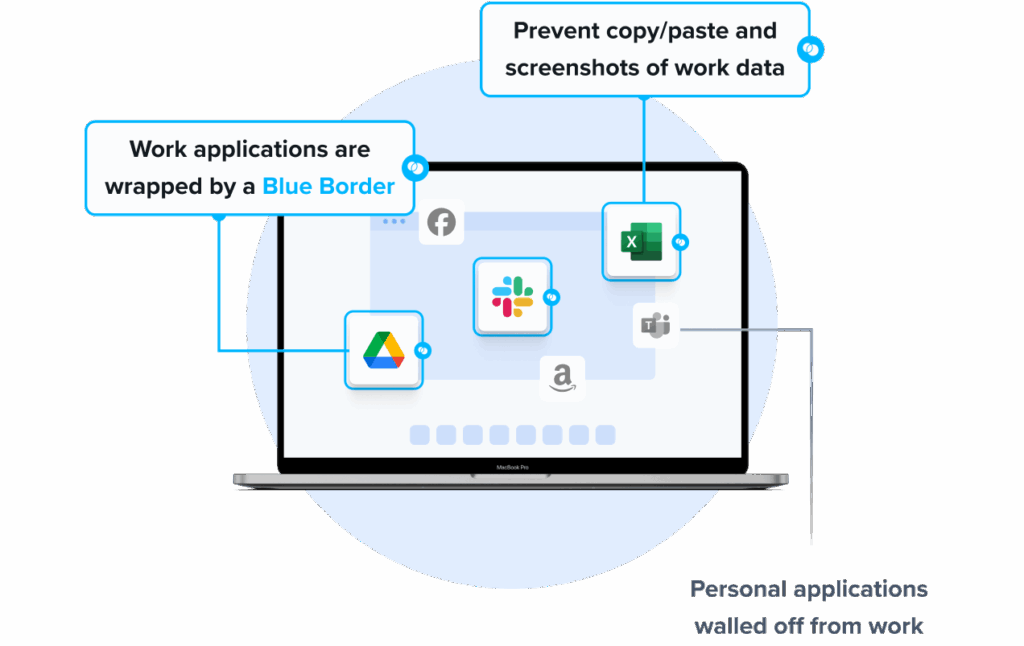
Venn’s Blue Border™ protects company data and applications on BYOD computers used by contractors and remote employees. Similar to an MDM solution but for laptops – work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Key Features include:
- Seamless MFA integration: Works with Okta, Azure, and Duo for smooth, secure authentication
- Encrypted workspace: Protects all data and applications with robust encryption
- Context-aware access controls: Enforces policies based on user, device, and environment
- Comprehensive session logging: Tracks all activity with full audit visibility
- Unified Zero Trust solution: Combines endpoint protection, remote access, and Zero Trust security
- Faster, scalable alternative: Optimized performance compared with legacy VPNs and VDI
Schedule a demo of Blue Border™
2. NinjaOne Remote

NinjaOne Remote is a secure, fully integrated remote access solution for IT teams and MSPs managing mixed operating system environments. It allows one-click remote access to Windows, macOS, and Linux endpoints directly from the NinjaOne console. Sessions launch in seconds, support technician tools, and deliver security without requiring VPNs or complex setup.
Key features include:
- One-click remote access: Technicians can launch remote sessions to a Windows or Mac device from the NinjaOne console or ticketing interface.
- Cross-platform support: Native support for Windows, macOS, and Linux endpoints ensures compatibility. Remote access is also available for Android and iOS, including the ability to view iOS screens and control Android devices.
- Quick connect for unmanaged devices: Secure access to off-network or BYOD devices, such as contractor laptops or third-party systems. is available without requiring installation.
- Enterprise encryption: Uses the x25519+XSalsa20+Poly1305 encryption suite to secure all session data.
- Privacy and data protection controls: Admins can disable clipboard syncing, enforce auto-clear clipboard policies, and use “Paste as Keystrokes” to prevent data leaks. Role-based access ensures users only see and do what they’re permitted to.
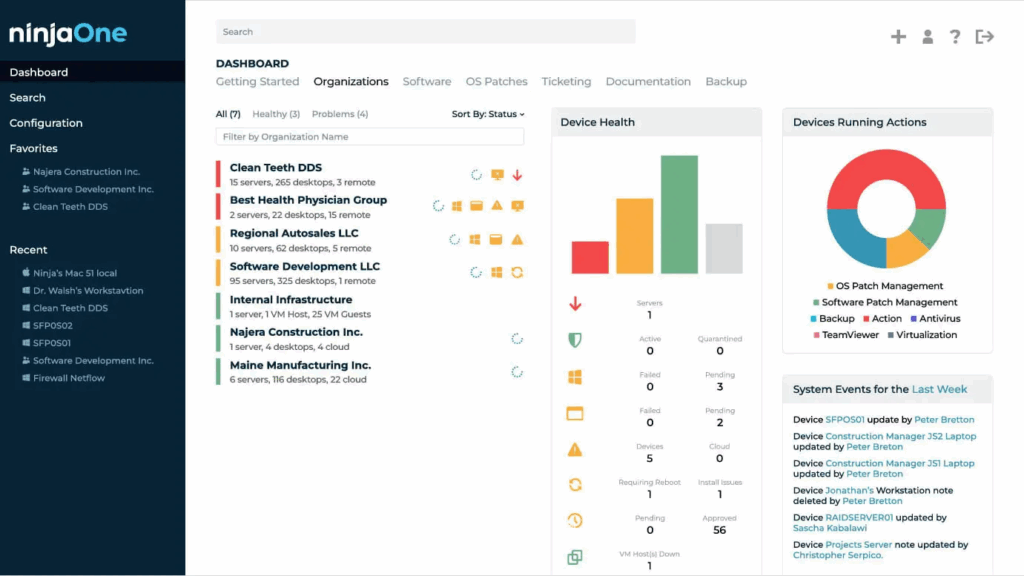
Source: NinjaOne
3. Check Point Harmony

Check Point Harmony is an integrated security solution to protect hybrid and remote workforces against cyber threats across endpoints, emails, browsers, applications, and remote access channels. It offers AI-powered threat prevention with a security layer that spans devices, networks, and user activity.
Key features include:
- Threat prevention across the workspace: Protects users from threats across major attack vectors, including email, collaboration tools, browsers, and unmanaged devices.
- Anti-phishing and anti-ransomware: Machine learning detects and blocks phishing attempts, including brand impersonation and SMS phishing, as well as ransomware attacks that target remote and hybrid users.
- Secure remote access: Includes built-in secure access capabilities that protect remote connections to corporate resources without relying on traditional VPNs.
- Data loss prevention (DLP): Integrated DLP capabilities identify and prevent the unauthorized sharing or leakage of sensitive data across emails, web uploads, and applications.
- Threat exposure management: Continuously assesses device posture and exposure levels, identifying vulnerabilities, misconfigurations, and potential entry points that could be exploited by attackers.
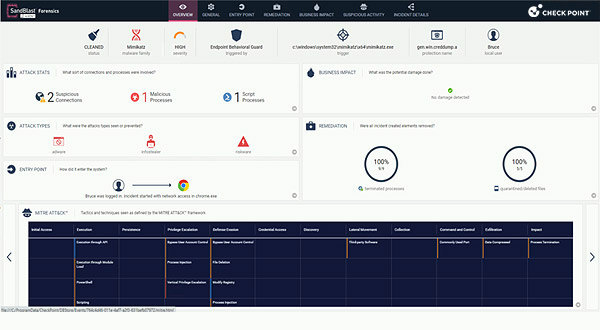
Source: Check Point
4. Citrix Secure Private Access

Citrix Secure Private Access is a zero trust network access (ZTNA) solution that replaces traditional VPNs by delivering secure, identity-aware access to applications from managed or unmanaged devices. Intended for hybrid and remote work environments, it ensures access is continuously verified using contextual and adaptive controls.
Key features include:
- Zero trust access for all applications: Applies zero trust principles (deny-by-default, least privilege, and continuous verification) to secure access to on-premises, cloud, SaaS, and virtualized applications.
- Granular and contextual access controls: Access decisions are based on real-time evaluation of user identity, location, device posture, and risk level.
- Seamless VPN replacement: Provides an easy path from VPN to ZTNA using the same Citrix Secure Access Client. Organizations using NetScaler Gateway can enable ZTNA without requiring new infrastructure.
- Integrated with Citrix StoreFront: Users access assigned applications through a single interface with single sign-on (SSO).
- Adaptive and multi-factor authentication (MFA): Supports adaptive authentication, prompting additional verification based on risk context. MFA and device posture checks are enforced before granting access.
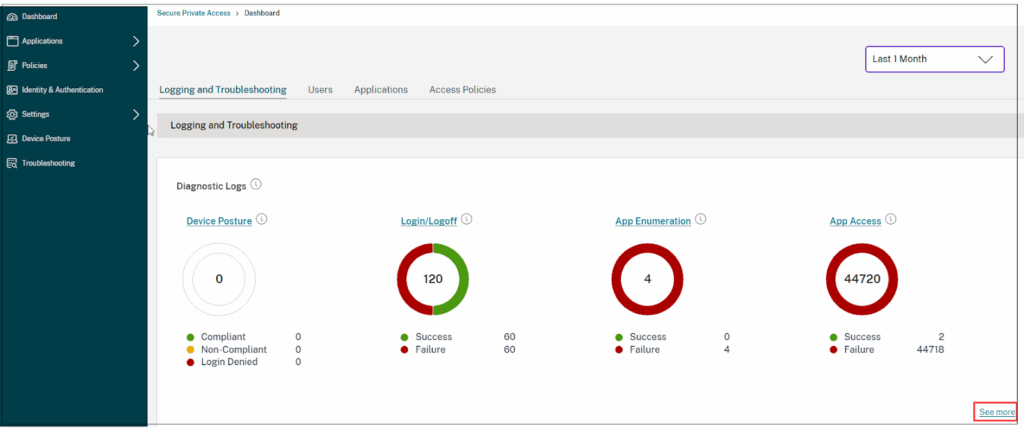
Source: Citrix
5. NordLayer

NordLayer is a secure remote access platform that helps protect distributed workforces and hybrid environments by combining business VPN, zero trust network access (ZTNA), and threat prevention technologies. It enables encrypted access to corporate resources regardless of user location or device type.
Key features include:
- Encrypted business VPN: Provides VPN functionality to securely connect users to internal networks. Encryption shields data in transit, while IP masking helps maintain privacy and reduces exposure to external threats.
- Zero trust network access (ZTNA): Enforces identity-based access policies using zero trust principles. Users are authenticated and authorized per session, ensuring access is limited to the resources they need.
- Multilayered authentication and access control: Integrates MFA and user verification mechanisms to ensure that only authorized users can access corporate resources. Role-based access controls help enforce the principle of least privilege.
- Cloud LAN for resource segmentation: Supports creation of isolated virtual networks (Cloud LANs), allowing remote teams or departments to securely access only the services or assets they are assigned.
- Threat protection: Blocks access to malicious websites and prevents phishing and malware attacks before they reach endpoints.
Source: NordLayer
Related content: Read our guide to secure remote access providers
Considerations for Choosing Secure Remote Access Solutions
When selecting a secure remote access solution, organizations need to balance security requirements, user experience, and operational overhead. Several key factors should guide the decision.
Security Capabilities
The solution must provide strong authentication, encryption, and access control mechanisms. Zero trust support, continuous verification, and integration with endpoint protection are critical to defending against modern threats. Organizations should also consider whether the solution includes built-in data loss prevention (DLP), threat detection, and compliance logging.
Compatibility and Integration
Solutions should integrate seamlessly with existing infrastructure, including identity providers, security information and event management (SIEM) systems, and cloud applications. Compatibility with different operating systems, mobile devices, and bring-your-own-device (BYOD) policies is also important to avoid gaps in coverage.
Scalability and Performance
Remote access must scale as the workforce grows or shifts to hybrid models. Cloud-native or elastic architectures can handle traffic spikes and large user volumes without performance degradation. Latency-sensitive applications, such as video conferencing or virtual desktops, require optimized routing and low overhead.
User Experience
Adoption depends on ease of use. Complicated login processes, frequent disconnections, or noticeable slowdowns can lead to user frustration and workarounds that undermine security. Solutions that provide seamless authentication, single sign-on, and fast connections encourage compliance with security policies.
Operational Management
Administration should not introduce unnecessary complexity. Centralized dashboards, policy automation, and detailed reporting reduce the burden on IT and security teams. Granular control over access policies and the ability to rapidly respond to incidents are also important.
Cost and Licensing Model
Pricing structures vary, from per-user licensing to consumption-based billing. Organizations should evaluate both upfront and ongoing costs, including infrastructure requirements, support, and maintenance. The total cost of ownership should be weighed against security, flexibility, and productivity gains.
Regulatory and Compliance Requirements
Industries with strict data protection standards (e.g., healthcare, finance) must ensure that remote access solutions comply with frameworks such as HIPAA, PCI-DSS, or GDPR. Built-in compliance reporting, audit trails, and data handling safeguards simplify meeting regulatory obligations.
Conclusion
Secure remote access solutions have become a core component of modern IT infrastructure, enabling organizations to balance productivity with strong security. By integrating identity verification, encryption, monitoring, and adaptive access policies, they ensure that critical resources remain protected regardless of user location or device. As remote and hybrid work continue to expand, these solutions provide the framework needed to maintain resilience against evolving threats while supporting the flexibility demanded by today’s workforce.
Learn more in our detailed guide for secure remote access best practices