Best VDI Providers and Alternatives: Top 8 in 2026

What Are Virtual Desktop Infrastructure (VDI) Providers?
Virtual desktop infrastructure (VDI) providers deliver platforms that enable organizations to deploy and manage virtual desktops hosted on centralized servers or clouds. These providers supply the resources, software, and management tools required to provision, monitor, and secure employee desktops, offering an alternative to traditional desktop computing models.
The best VDI provider for your organization depends on specific needs, with options ranging from cloud-agnostic solutions and specialized tools for complex environments to simpler services for smaller businesses. VDI providers should supply not just the virtualization technology but also integration, support, and security capabilities.
Frustrated by Lag and Latency from VDI/DaaS?
Discover how Venn’s local-first approach secures remote workforces without the complexity and latency of traditional VDI.

In this article:
Key Features of VDI Providers
Scalability and Deployment Options
VDI platforms claim to offer scalability, but expanding capacity typically involves navigating licensing constraints, hardware limitations, and unpredictable costs. Scaling on-premises infrastructure often requires time-consuming procurement cycles and upfront investment in servers, storage, and networking. Even in cloud-based models, unexpected surges in demand can result in performance degradation or cost overruns.
Deployment flexibility is another advertised benefit, but each model introduces trade-offs. On-premises deployments demand extensive in-house expertise and capital investment, while cloud-based solutions may lead to vendor lock-in and recurring operational costs.
Performance and User Experience
Despite vendor claims, VDI rarely delivers a consistent experience across all user types or device configurations. Latency, graphical lag, and input delay remain common issues, particularly over congested networks or from remote locations. These problems are exacerbated in graphics-intensive workloads, where VDI struggles to match the responsiveness of physical desktops.
Peripheral compatibility and multimedia performance are also frequent pain points. Users often experience dropped frames, audio/video sync issues, or limited support for devices like webcams, printers, and smart card readers. Personalization features such as roaming profiles or application layering introduce further complexity and may cause login delays or inconsistent behavior between sessions.
Security and Compliance
While centralizing desktops can reduce endpoint risks, VDI introduces its own attack surfaces, particularly at the hypervisor, broker, and session layers. Misconfiguration, weak access controls, or unpatched infrastructure can expose sensitive systems to exploitation. Managing security across multiple layers (network, storage, hypervisor, and guest OS) adds operational burden and increases the chance of oversight.
Compliance enforcement within VDI is also complex. Ensuring data residency, auditability, and secure access across multiple jurisdictions and infrastructure types requires deep customization. These systems often depend on manual configuration and third-party tools, increasing the chance of drift from compliance baselines or failure to enforce policies effectively.
Management and Monitoring
Managing VDI at scale introduces significant administrative overhead. IT teams must maintain a stack that includes hypervisors, connection brokers, profile management systems, and patching workflows, all of which must be tightly coordinated. Automation tools often require custom scripting or vendor-specific training, making day-to-day operations labor-intensive.
Monitoring tools provide visibility but add cost and complexity. Gaining accurate, actionable insights often requires integration with external analytics platforms. Diagnosing performance issues or pinpointing the root cause of a degraded session can be difficult due to the number of interdependent components, increasing mean time to resolution and user frustration.
High Availability and Disaster Recovery
Achieving high availability in VDI environments requires building redundancy across the full stack (storage arrays, network paths, hypervisors, session brokers) which increases both cost and configuration complexity. Even with failover mechanisms in place, recovery is not always seamless, and users may experience session interruptions or data loss.
Disaster recovery planning in VDI environments is particularly demanding. Ensuring synchronization across multiple data centers, validating replica integrity, and orchestrating failovers without impacting user experience demands sophisticated infrastructure and planning. Recovery testing is resource-intensive and often deferred, leading to untested assumptions about failover reliability in actual disaster scenarios.
Challenges and Limitations of VDI Providers
While VDI is a common choice for organizations, it presents technical and operational challenges that organizations must account for during planning and deployment.
- High initial setup and licensing costs: VDI infrastructure demands significant upfront investment in servers, storage, networking, and software licenses. Licensing models can be complex and may vary between vendors, making budgeting unpredictable. Even in cloud-hosted models, operational expenses can accumulate quickly with increased usage or poor resource management.
- Latency and performance bottlenecks: Without careful resource allocation, VDI environments can suffer from latency, slow application performance, or degraded user experience, especially during peak usage or with graphics-heavy workloads. Misconfigured storage, network congestion, or inadequate GPU provisioning can all impact performance.
- Complexity of implementation and management: VDI deployment involves integrating multiple components: hypervisors, connection brokers, storage systems, and security layers, which can be complex to design and maintain. Organizations need specialized expertise to implement and manage these environments effectively, which may not be readily available in-house.
- Dependency on network connectivity: Since VDI desktops are accessed over the network, any disruption in connectivity, either locally or with the hosting provider, can render desktops inaccessible. This dependency makes robust, low-latency networking critical and adds pressure on IT teams to ensure consistent availability.
- Scalability constraints in on-premises setups: Scaling an on-premises VDI environment often requires additional hardware procurement, which introduces delays and capital expenditure. Cloud-based models ease this issue but may introduce other constraints such as vendor lock-in or unpredictable costs.
- Vendor lock-in and interoperability issues: Some VDI solutions may not easily integrate with third-party tools or allow seamless migration between platforms. Organizations tied to proprietary management tools or protocols may face restrictions when trying to adapt or switch providers.
- User training and adoption challenges: Transitioning from physical desktops to virtual environments can lead to user resistance or require training, particularly if users face changes in login procedures, peripheral support, or application performance.
Related content: Read our guide to virtual desktop latency
Why VDI Doesn’t Work in a BYOD Environment
VDI assumes tight control over the device and network, but BYOD environments offer neither. Employees use personal devices with varying hardware, software, and security postures, which can break compatibility with VDI agents or degrade performance. Troubleshooting device-specific issues also becomes more difficult without control over the endpoint.
Security is another constraint. While VDI centralizes data, it still relies on session-level controls that may not fully account for clipboard sharing, screen captures, or unsanctioned browser activity. Inconsistent enforcement of policies across unmanaged devices creates exposure that VDI is not well-equipped to mitigate, especially compared to newer zero trust or browser-based models.
Notable VDI Alternatives
1. Venn

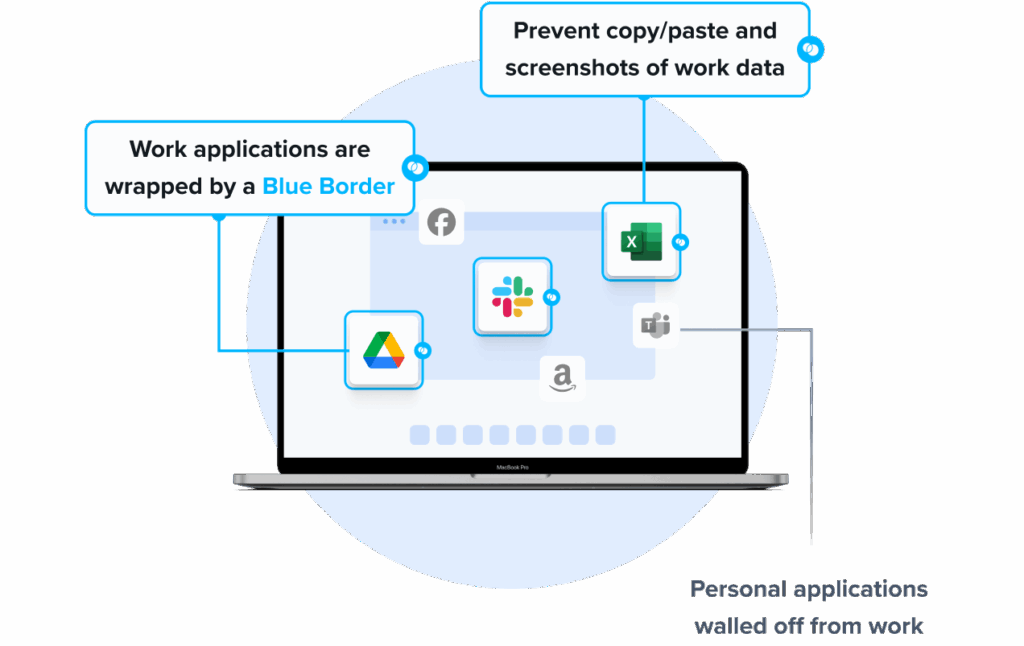
Venn’s Blue Border was purpose-built to protect company data and applications on BYOD computers used by contractors and remote employees – without VDI.
Similar to an MDM solution but for laptops, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
With Venn, you can eliminate the burden of purchasing and securing laptops and managing virtual desktops (VDI.) Unlike virtual desktops, Venn keeps users working locally on natively installed applications without latency – all while extending corporate firewall protection to business activity only.
Key features include:
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
2. Prisma Access

Prisma Access is a cloud-delivered zero trust service within Prisma SASE that secures remote access across managed and unmanaged devices. It applies identity-based policies and granular data controls, supports BYOD scenarios, governs GenAI usage, and offers a browser-centric path to reduce dependence on traditional VDI.
Key features include:
- Zero trust access policies: Apply identity-based access and granular data controls to secure remote access for employees, contractors, and third parties across environments.
- Managed and unmanaged device coverage: Enforce consistent protections and visibility on corporate endpoints and BYOD, enabling secure work without installing heavy agents or controlling devices.
- GenAI usage governance: Gain visibility into GenAI application activity, restrict sensitive data sharing, and curb shadow AI risks at the browser and session level.
- VDI reduction path: Provide a policy-enforced workspace that can replace many VDI use cases, lowering complexity while maintaining centralized control over applications and data.
- SASE integration: Leverage Prisma SASE capabilities to extend cloud-delivered security to the access layer, unifying enforcement and simplifying deployment across distributed organizations and devices.
Source: Palo Alto Networks
3. Zscaler Zero Trust Exchange Platform

Zscaler Zero Trust Exchange is a cloud-native platform that brokers one-to-one, least-privileged connections between users and applications. Its proxy architecture performs TLS inspection, hides applications from the internet, prevents lateral movement, and applies data protection controls. It supports replacing VPNs and some VDI patterns.
Key features include:
- Proxy-based architecture: Brokers one-to-one connections using identity, context, and policy, enabling TLS inspection at scale without exposing applications to the internet.
- Least-privileged access: Connects users or workloads directly to applications rather than networks, reducing reachable surfaces and eliminating traditional lateral movement pathways inside environments.
- Attack surface reduction: Hides private applications behind the platform, making them invisible to unsolicited discovery, scanning, and direct inbound connections from untrusted networks.
- Data protection controls: Identifies and protects sensitive data in motion, at rest, and in use, applying DLP policies across web and SaaS channels.
- VPN and VDI replacement: Enables replacing legacy VPN and many VDI use cases with zero trust access, simplifying architectures and reducing reliance on perimeter firewalls.
Source: Zscaler
Notable VDI Providers
4. Omnissa Horizon

Omnissa Horizon (formerly VMware Horizon) is a virtual desktop and application platform built on VMware’s enterprise-grade virtualization stack. It allows organizations to deliver Windows, Linux, or macOS desktops from centralized data centers or clouds using VMware vSphere and related technologies.
Key features include:
- VMware vSphere integration: Utilizes the vSphere hypervisor (ESXi) and vCenter Server for efficient and scalable virtual desktop deployment and infrastructure management.
- Protocol support: Supports multiple remote display protocols including VMware Blast Extreme, Microsoft RDP, and Teradici PCoIP to optimize performance across varying network conditions.
- App and profile virtualization: Includes tools like ThinApp for application virtualization and View Persona Management for user profile persistence across sessions.
- Management tools: Features such as View Manager and View Composer allow administrators to automate desktop provisioning, manage user sessions, and simplify clone-based deployments.
- Security features: Integrates vShield Endpoint for antivirus offloading and secure endpoint interaction, reducing overhead on virtual machines.
Source: Omnissa
5. Inuvika OVD Enterprise

Inuvika OVD Enterprise is a Linux-based virtual desktop and application delivery platform designed as a cost-effective alternative to Citrix and VMware Horizon (Omnissa Horizon). It enables secure delivery of Windows and Linux applications and virtual desktops to any device, over any hypervisor or cloud platform.
Key features include:
- Platform and hypervisor agnostic: Runs on any major hypervisor (vSphere, KVM, Hyper-V, Proxmox, Nutanix AHV) and deploys in public or private clouds including AWS, Azure, and GCP.
- Unified app delivery: Delivers both Windows and Linux applications through web browsers, shared or dedicated desktops (VDI), or as apps integrated into the local desktop environment.
- Optimized user experience: Offers native support for Microsoft Teams and Zoom, USB redirection, and high-performance video streaming across desktops, laptops, and mobile devices.
- Built-in security features: Designed on zero trust principles, includes built-in multi-factor authentication (2FA), granular access controls, and encrypted data transmission, eliminating the need for external VPNs or separate MFA services.
- No proprietary infrastructure dependencies: Eliminates the need for Microsoft SQL Server licenses and third-party gateways like Citrix NetScaler by including its own Enterprise Secure Gateway.

Source: Inuvika
6. Ericom

Ericom offers a suite of VDI solutions that enable secure, centralized access to Windows desktops and applications from almost any device or location. Designed to reduce IT overhead while improving manageability and data security, Ericom’s platform supports a range of deployment environments, including VDI, remote desktop services (RDS), and Blade PCs.
Key features include:
- Broad device and platform support: Access virtual desktops securely from PCs, Macs, Linux machines, Chromebooks, tablets, and smartphones, suitable for BYOD and remote work scenarios.
- Flexible client options: Offers native RDP clients and Ericom AccessNow, an HTML5-based client that runs in any modern browser with no plugins or installations, enabling zero-maintenance endpoint access.
- Enhanced RDP performance: Ericom Blaze accelerates RDP display rendering to improve responsiveness and user experience, particularly on slower networks or lower-spec devices.
- Secure and centralized management: PowerTerm WebConnect DeskView provides a centralized admin console for managing desktops, servers, and users. Includes session auditing, access controls, and universal printing.
- Efficient desktop delivery: Enables rapid deployment, updates, and maintenance of virtual desktops by centralizing operations in the data center, reducing time, complexity, and support overhead.
7. V2 Cloud

V2 Cloud is a fully managed cloud-based virtual desktop infrastructure solution to deliver fast remote access to Windows applications and desktops. Built for simplicity and performance, V2 Cloud enables organizations to support remote and hybrid workforces without requiring deep technical expertise or complex infrastructure.
Key features include:
- Quick and simple deployment: Launch virtual desktops in just a few clicks and manage everything through a centralized, user-friendly web dashboard, no specialized IT staff required.
- Secure access anywhere: Enables secure remote access from any device, with built-in location-based security policies and proprietary controls that protect sensitive data and support compliance efforts.
- Cloud-native architecture: Delivers virtual desktops from the cloud, eliminating the need for on-premises infrastructure while allowing flexible access to applications and files from anywhere.
- Flexible deployment models: Supports various deployment needs, from fully cloud-hosted desktops to hybrid environments, making it adaptable to startups, SMBs, and enterprise use cases alike.
- Cost-effective virtual desktops: Offers priced plans with predictable costs, reducing capital expenditure while ensuring strong performance and data protection.