Citrix Enterprise Browser: Pros/Cons and Top 8 Alternatives in 2025
What Is Citrix Enterprise Browser (formerly Citrix Workspace Browser)?
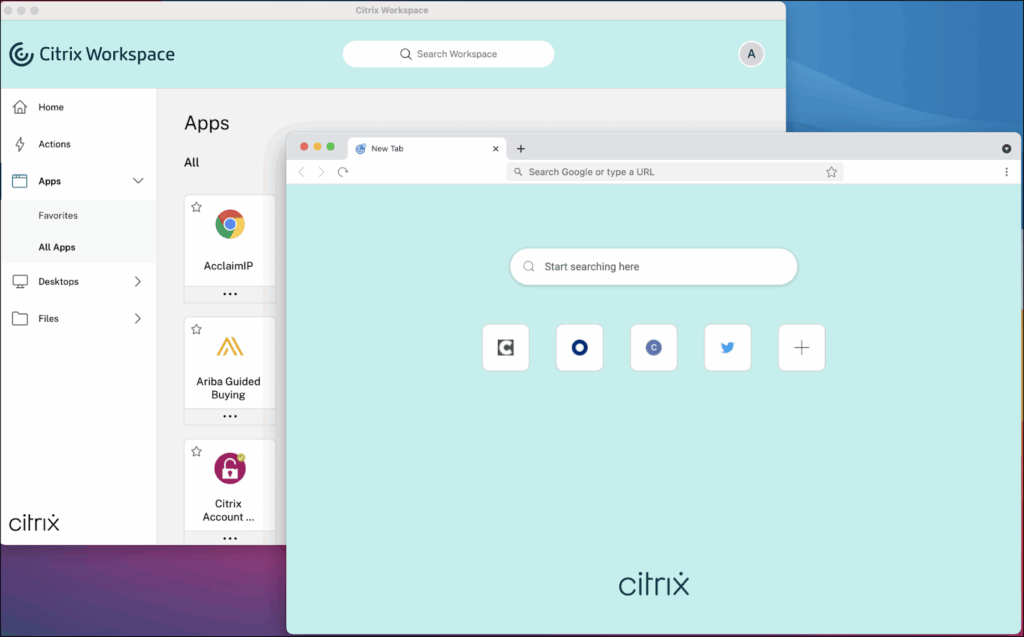
Citrix Enterprise Browser, previously called Citrix Workspace Browser, is a Chromium-based browser that runs locally on the user’s device. It is integrated with the Citrix Workspace app for Windows and Mac, and is used to securely open web or SaaS applications launched from the Workspace app.
When a supported app is opened in Citrix Workspace, the Enterprise Browser launches in a separate window. It can access internal web applications without requiring a VPN and can also open external SaaS apps when Secure Private Access policies are applied. Without these policies, external apps open in the user’s default native browser.
The browser adds an additional security layer, helping protect both the endpoint and the organization’s network from unsafe user actions. However, it forces users to switch from a familiar browser environment to a dedicated secure browser, which can reduce user productivity and satisfaction.
Source: Citrix
This is part of a series of articles about Citrix VDI
In this article:
Key Features of Citrix Enterprise Browser
Citrix Enterprise Browser provides the following features when used in tandem with the Citrix Workspace app:
- VPN-less access to internal apps: Enables direct access to internal web applications without connecting to a VPN, reducing latency and simplifying remote access.
- Tabs and multiple windows: Supports multiple tabs and separate windows for different applications. New Workspace-launched apps open in their own tabs, with options to group or pin tabs. Tabs can be moved to a separate window by dragging them out of the current window.
- Progressive web app (PWA) support: Allows installation and use of PWAs for faster load times and near-native desktop app behavior. Installed PWAs require Workspace app authentication before use.
- Editable Omnibox: Lets users enter URLs or perform searches directly from the address bar. Google is the default search engine.
- Bookmarks: Enables saving frequently visited sites for quick access. Bookmarks can be imported from other browsers as HTML files, but cannot be exported.
- Microphone and webcam support: Compatible with popular conferencing platforms, including Microsoft Teams, Google Meet, Zoom, GoToMeeting, and Cisco Webex.
- Proxy authentication: Provides one-time authentication for proxy servers using credentials stored in Windows Credential Manager. On unsupported configurations or macOS, credentials are requested and cached in memory until the browser is closed.
- Analytics integration: When Citrix Analytics Service is enabled, administrators can capture usage data and security insights. Certain event reporting is limited on macOS when the Workspace app is closed directly.
Key Limitations of Citrix Enterprise Browser
While Citrix Enterprise Browser provides secure, policy-driven access to internal and SaaS applications, it comes with certain challenges that can impact deployment, integration, and day-to-day use. These limitations were reported by users via Gartner Peer Insights:
- Performance and connectivity issues: Under heavy internet traffic or unstable network conditions, users may experience slow performance or session timeouts. In some cases, a full page refresh or reconnect is required, disrupting workflows.
- Learning curve for users and IT teams: Adopting the browser requires training and adjustment. Users unfamiliar with Citrix or accustomed to personal browsers may resist switching, especially if benefits are not immediately clear.
- User experience drawbacks: Some users find the security and management controls overly restrictive compared to consumer browsers, and interface elements like the landing page may not meet personal preferences.
- Complex deployment and administration: Integrating the browser into an enterprise environment can be time-consuming, requiring significant IT expertise and often multiple dedicated staff to manage configuration, updates, and troubleshooting.
- Limited integration flexibility: The browser is optimized for the Citrix ecosystem, which can limit compatibility with third-party tools or workflows outside this environment. Organizations heavily invested in other platforms may find it less adaptable.
- Dependency on Citrix infrastructure: Functionality and performance are tightly coupled with Citrix services, reducing flexibility for organizations that operate in mixed or non-Citrix environments.
- Configuration complexity: Fine-tuning advanced settings and adapting the browser for specific environments can be cumbersome, particularly for teams without deep Citrix expertise.
- Change management challenges: Switching from a familiar personal browser to Citrix Enterprise Browser can create resistance, especially if the perceived advantages are minimal from an end-user perspective.
Break Free from Citrix VDI’s Limitations
Discover how Venn enables secure BYOD access without the complexity, cost, and latency of Citrix VDI.

Notable Citrix Enterprise Browser Alternatives
In light of the above limitations, many organizations are seeking alternatives to the Citrix Enterprise Browser. Here are some popular options.
1. Venn

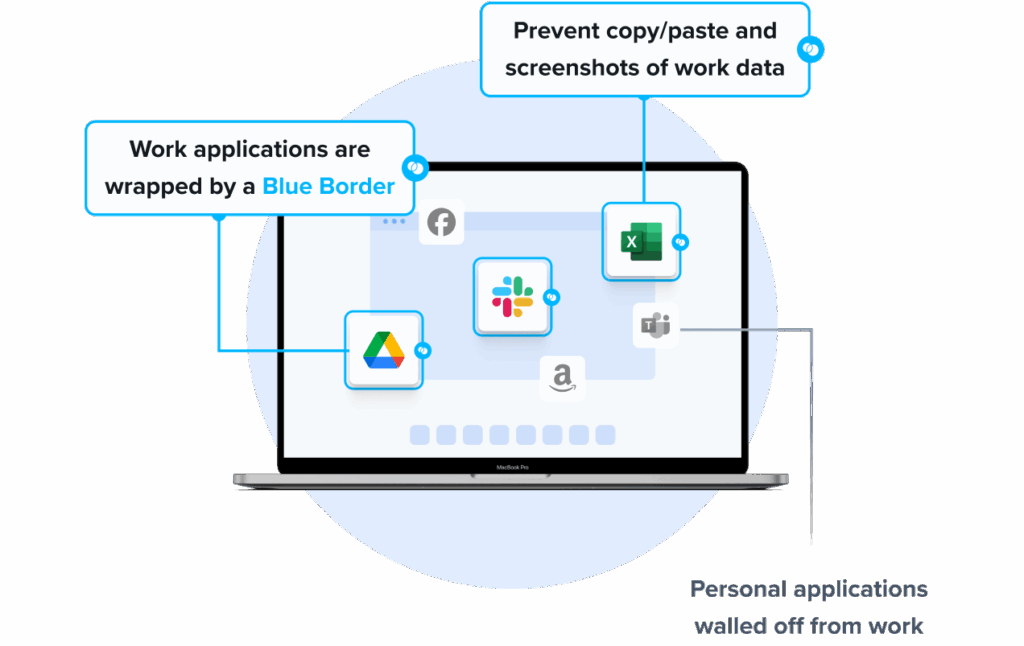
Venn’s Blue Border was purpose-built to protect company data and applications on BYOD computers used by contractors and remote employees without VDI.
Similar to an MDM solution but for laptops, work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Unlike Citrix, which often requires heavy backend setup, constant maintenance, and high licensing costs, Venn eliminates back-end dependencies altogether. With no VDI infrastructure to buy or maintain, Venn lowers total cost of ownership while improving the user experience.
Key features include:
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
2. Google Chrome Enterprise

Google Chrome Enterprise is a business-focused version of the Chrome browser, designed to provide organizations with security, centralized management, and a familiar user experience. Built on Chromium, it combines speed and reliability with enterprise-grade controls, making it easier for IT teams to deploy, secure, and maintain across devices and operating systems.
Key features include:
- Familiar user experience: Employees use the same Chrome interface they know, reducing training needs and supporting adoption.
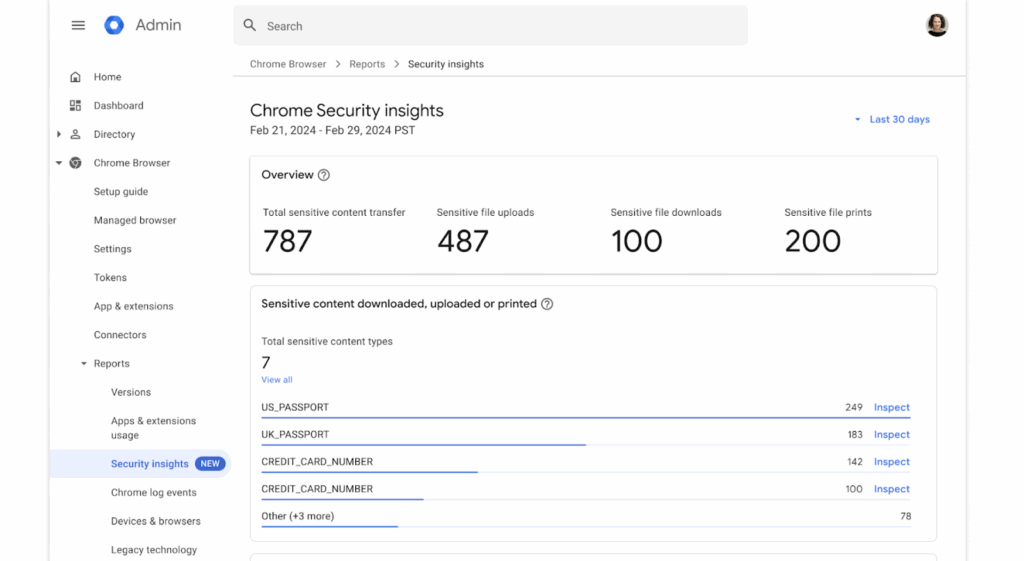
- Centralized management: Cloud-based admin console enables quick deployment, policy enforcement, and browser customization across all endpoints.
- Security: Built-in zero trust policies, threat protection, and data controls protect against internal and external risks.
- Cross-platform support: Works consistently across Windows, macOS, Linux, and ChromeOS, adapting to remote and hybrid work requirements.
- Open ecosystem integration: Designed to work with existing business applications and IT infrastructure without vendor lock-in.
Source: Google
3. Island Browser

Island Browser is a Chromium-based enterprise browser for secure corporate environments. Instead of relying on add-ons or external gateways, it embeds security, access controls, and productivity features into the browser itself. Organizations can manage application access, protect sensitive data, and automate workflows while offering a familiar browsing experience to employees.
Key features include:
- Application access control: Conditional access rules assess identity, device, network, location, and application before granting resource access.
- Device visibility and management: Monitors endpoint posture and enforces security configurations.
- Application automation: Automates repetitive workflows directly within the browser to improve efficiency.
- Zero trust network access: Provides secure, policy-driven connectivity to internal and cloud applications without relying on VPNs.
- Security: Defends against phishing, malware, session hijacking, and other browser-based threats without third-party extensions.
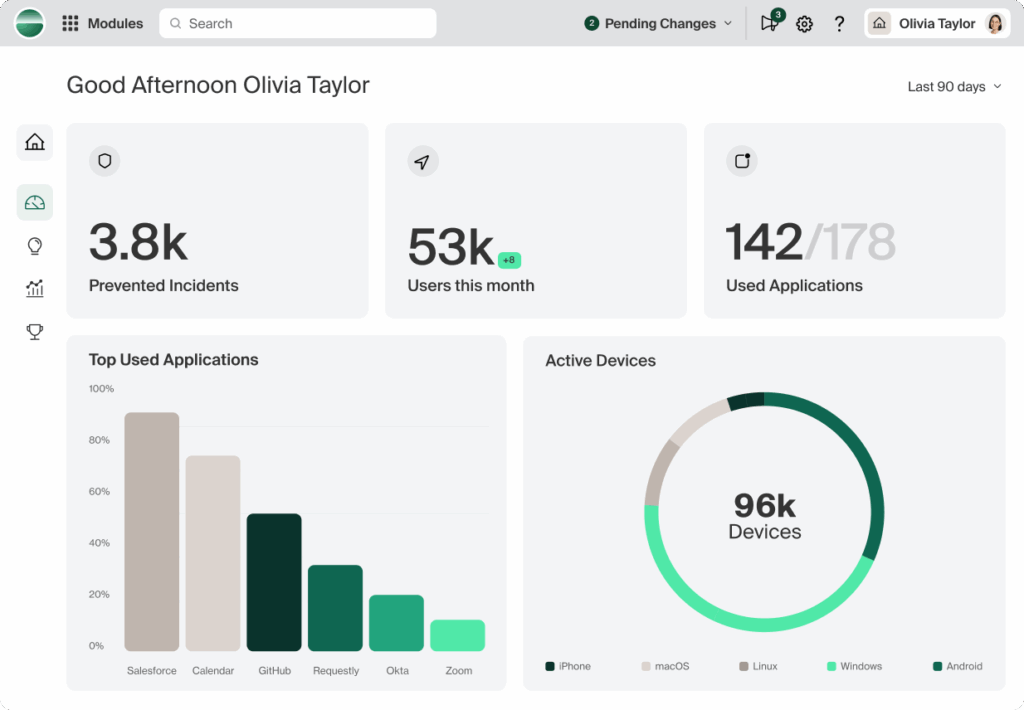
4. Prisma Access Browser

Prisma Access Browser is a secure, SASE-native browser to extend enterprise-grade protection to all devices, whether managed or unmanaged. By integrating with Prisma Access, it delivers zero trust access, data controls, and threat prevention without requiring additional agents or complex setups.
Key features include:
- SASE-native integration: Extends Prisma Access security and policies to every browser session without extra agents.
- Zero trust access policies: Enforces authentication and authorization rules based on user identity, device type, and activity.
- BYOD security: Protects sensitive data on personal devices without requiring full device management.
- GenAI data protection: Provides visibility into AI application usage and blocks Shadow AI to prevent unauthorized data exposure.
- Independent worker enablement: Offers secure remote access without shipping corporate laptops, helping reduce costs.
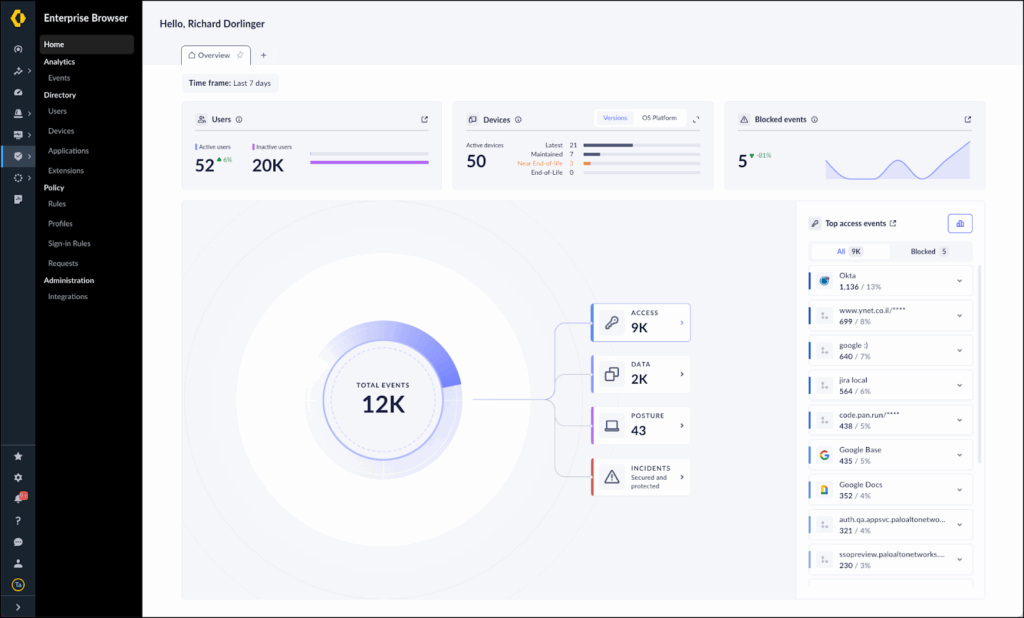
Source: Palo Alto Networks
5. SURF Zero Trust Browser

SURF Zero Trust Browser is a Chromium-based enterprise browser to secure access to company resources from various locations and devices without compromising user experience. It combines zero trust principles with data control, device posture verification, and integrated threat prevention and is intended for both managed and unmanaged endpoints.
Key features include:
- Data loss prevention controls: Enable or disable copy, paste, printing, screen sharing, and other actions to prevent unauthorized data use.
- Secure download management: Applies encryption, watermarking, malware scanning, and secure storage to protect downloaded files.
- Phishing protection: Uses trusted domain lists, SSL certificate validation, SaaS reputation checks, and other techniques to block social engineering threats.
- Access control & device posture checks: Enforces role-based permissions and verifies device security posture, including antivirus, disk encryption, OS version, and certificate checks.
- Browser management: Gives administrators control over add-ons, extensions, web filtering, content rendering, and transactional MFA.
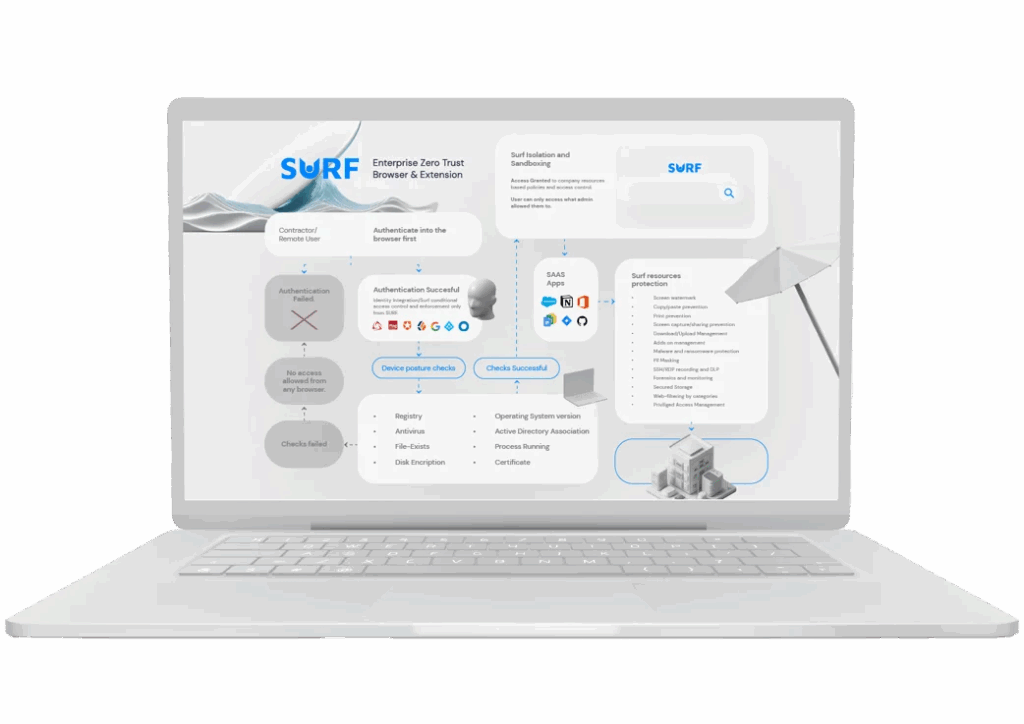
Source: SURF
6. Microsoft Edge for Business

Microsoft Edge for Business is a dedicated work browsing experience that separates work and personal activity into different windows. It is activated with a Microsoft Entra ID login and is available on Edge version 116 or later. It supports managed and unmanaged devices and preserves enterprise controls and policy enforcement.
Key features include:
- Work–personal separation: Opens distinct work and personal windows with separate caches, storage, and favorites; automatically switches work URLs into the work window.
- Activation and availability: Enabled by Microsoft Entra ID login; available on managed devices with Edge 116+, preview support for unmanaged devices via Windows MAM.
- MAM for Windows: Uses Intune application configuration and protection policies, conditional access, and Windows Security Center integration to secure organizational data on personal Windows devices.
- MAM for mobile: Applies Intune configuration and protection policies to Edge for iOS and Android, enabling secure access to work resources on personal mobile devices.
- Organization branding and controls: Supports company branding in the work window and lightly managed personal browsing, with user-configurable automatic switching and policy-based restrictions.
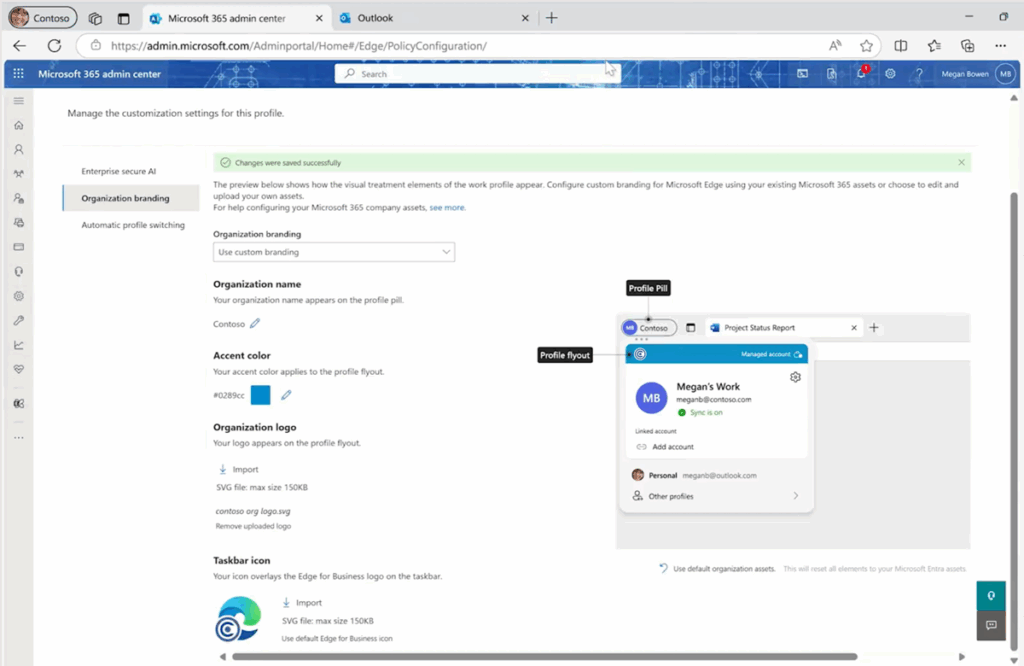
Source: Microsoft
7. Check Point Harmony Browse

Harmony Browse is a browser extension that provides multi-layer web threat prevention on managed or unmanaged devices. It focuses on phishing defense, data loss prevention, and malware sanitization while enabling centralized management across browsers.
Key features include:
- Phishing protection: Detects and blocks sophisticated phishing attempts as users browse, aiming to reduce credential theft and session hijacking risks.
- DLP: Prevents unauthorized data sharing across web apps, protects passwords, and scans files on upload and download to support compliance requirements.
- Multi-layer malware defense: Uses sandboxing and content disarm and reconstruction with approximately 1.5-second sanitization to block malicious downloads and active content.
- GenAI safeguards: Restricts sensitive inputs into AI tools, monitors and manages usage, and provides visibility and policies tailored to generative AI applications.
- Lightweight deployment and management: Delivers browser protection as an extension with unified, fast deployment on managed or unmanaged devices and centralized policy administration across browsers.
Source: Check Point
8. Seraphic Security
Seraphic Security is a browser security platform that works with any browser and device using a single agent or lightweight extensions. It enforces data policies, blocks phishing and malware, and enables secure access to corporate apps without traditional VPN or VDI. It integrates with existing security tools and extends protections to Electron-based desktop applications.
Key features include:
- Single agent across environments: Provides visibility and control over browser activity on managed, BYOD, VDI, and third-party devices without forcing users to switch browsers.
- Granular data protections: Controls uploads, downloads, clipboard, screen sharing, and printing to limit data leakage while maintaining governance over web and SaaS activity.
- In-browser threat prevention: Blocks phishing, malware, and advanced browser-based attacks in real time, addressing gaps not covered by EDR, SSE, or legacy extensions.
- Identity-aware access: Enables secure access to corporate applications without traditional VPN or VDI, creating isolated workspaces and enforcing policy on managed and unmanaged endpoints.
- Ecosystem integration and desktop coverage: Integrates with SSO, EDR, sandboxing, malware scanning, SIEM, and CDR, and extends protections to Electron-based desktop applications.
Source: Seraphic Security
Related content: Read our guide to Citrix alternatives
Conclusion
Enterprise browsers are increasingly critical for organizations aiming to secure access to web and SaaS applications in remote and hybrid environments. These browsers embed security controls directly into the browsing layer, enabling zero trust access, data protection, and policy enforcement without requiring traditional endpoint agents or VPNs. By centralizing browser management and integrating with existing infrastructure, they reduce complexity for IT teams while maintaining productivity and flexibility for users across devices and locations.