Citrix VPN Alternative: Citrix Secure Private Access and Competitors

Does Citrix Offer a VPN?
While Citrix doesn’t offer a VPN solution, it provides technology that serves as a more secure VPN alternative. The Citrix Workspace platform includes the Citrix Secure Private Access client, which provides secure remote access to corporate applications, desktops, and data by creating an encrypted tunnel between a user’s device and the company network. It uses NetScaler Gateway as the secure endpoint.
While traditional VPNs offer network-level access, Citrix offers a Zero Trust Network Access (ZTNA) approach that provides more granular, browser-based access to applications without the need for device management. Administrators can use the Citrix platform to control permissions, monitor usage, deploy updates, and ensure compliance.
This is part of a series of articles about Citrix VDI
In this article:
What Is the Difference Between Citrix and VPNs?
Citrix and VPNs share a similar goal: providing secure remote access to organizational resources. However, they fundamentally differ in architecture and function. A VPN creates an encrypted tunnel between the user’s device and a private network, granting broad access to internal resources as if the user were physically present at the office. In contrast, Citrix delivers specific applications or desktops virtually, without exposing the entire network or directly connecting endpoints to sensitive infrastructure.
While VPNs offer a straightforward way to connect remote users to a network, they can introduce security risks by providing excessive access. Citrix mitigates this by isolating applications and enforcing robust access controls. This distinction is vital for organizations concerned about lateral movement within the network and those aiming to implement a Zero Trust security model. With Citrix, IT teams can limit the scope of user access and monitor activity without giving users a full network connection, providing better segmentation and control.
How Citrix Secure Private Access Works
Citrix Secure Private Access, offered as an integral part of the Citrix Workspace platform, but sometimes sold separately, is a zero trust network access (ZTNA) solution that replaces traditional VPNs by providing secure, identity-aware access to applications without exposing the entire network. Unlike VPNs, which create a full tunnel into a corporate network, Citrix Secure Private Access restricts access to only the specific applications a user is authorized to use. This reduces the attack surface and prevents lateral movement across internal systems.
Built for hybrid and remote work, the solution supports both managed and unmanaged devices, and enables secure access to virtual, web, and SaaS applications. It continuously verifies user identity and device posture using adaptive authentication methods such as multi-factor authentication (MFA) and context-based access controls. These zero trust principles (deny by default and least-privilege access) ensure stronger security than VPNs, especially in distributed environments.
Citrix Secure Private Access also offers advantages in performance and scalability. It connects users directly to the applications they need, bypassing the latency introduced by VPN backhauling. This results in faster and more reliable access, particularly important for remote and mobile users. As part of the broader Citrix platform, it integrates with tools like Citrix StoreFront and Citrix Director, enabling centralized policy enforcement.
Organizations already using NetScaler Gateway or the Citrix Secure Access Client can transition from VPN to ZTNA with minimal disruption.
Key Citrix Secure Private Access Limitations
While Citrix Secure Private Access offers strong security compared to traditional VPNs, several limitations can affect user experience, performance, and ease of management. Below are the main challenges organizations and users have reported on the G2 platform:
- Frequent connection drops and lag: The platform can experience disconnections or slow performance when network bandwidth is limited. Users often face lag or timeouts during remote sessions, especially over unstable connections.
- High resource consumption: Citrix processes tend to use a significant amount of system resources on host machines, which can impact overall performance on lower-end devices.
- Complex setup and integration: Initial setup, configuration, and integration, especially when deploying Citrix ADC, can be complex and time-consuming for administrators unfamiliar with the system.
- Interface limitations: The user interface lacks intuitiveness and modern design elements, making navigation and management more difficult for some users.
- Limited customization options: The platform offers restricted flexibility in dashboard customization and user experience tailoring, which can limit visibility and control for IT teams.
- Dependency on network quality: Performance is heavily dependent on network speed and stability. Bandwidth constraints can lead to session interruptions and reduced responsiveness.
- Manual updates and debugging issues: Users may not receive automatic update notifications and need to manually check for new versions. Debugging and troubleshooting tools are also less optimized compared to other remote workspace solutions.
- Support responsiveness: Customer support has been reported as slow or inconsistent in addressing issues, delaying problem resolution in production environments.
- Application compatibility: Some applications do not integrate smoothly with Citrix Secure Access, leading to interruptions or requiring additional installation steps on the user side.
Considering Citrix? Discover the Top Modern Alternatives
Discover the top Citrix alternatives for enabling seamless and secure remote work on unmanaged laptops. No latency, no complexity.

Notable Competitors of Citrix Secure Private Access
1. Venn

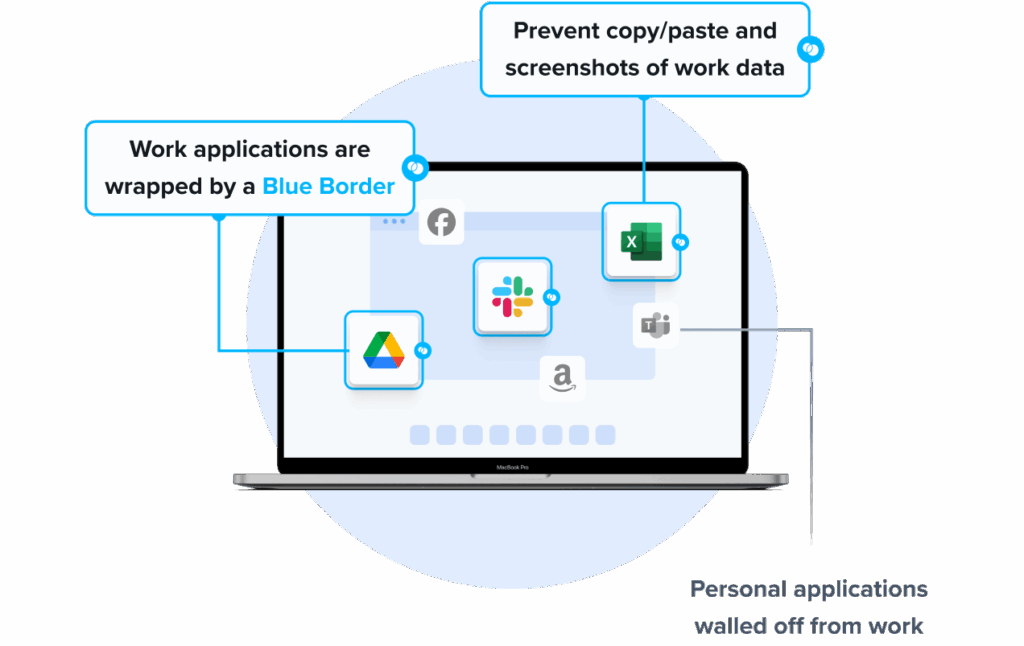
Venn’s Blue Border™ was purpose-built to secure company data and applications on BYOD computers used by contractors and remote employees without VDI.
Venn includes a secure private company gateway that provides the same Zero Trust network access layer as Citrix Secure Private Access or a VPN, but that’s only the beginning. Beyond protecting the network, Venn extends security all the way to the unmanaged endpoint itself; protecting sensitive company data and apps.
Similar to an MDM solution but for laptops, work lives inside a company-controlled Secure Enclave installed on the user’s PC or Mac. Within this Enclave, all data is encrypted, access is managed, and work applications run locally. With Venn, IT teams can eliminate the burden of purchasing and locking down corporate laptops or managing virtual desktops. Users work locally on native applications — with no virtualization, no latency, and no remote hosting — while company data stays protected within Blue Border.
Key features include:
- Secure Enclave technology: Encrypts and isolates work data on personal Mac or PC computers, both for browser-based and local applications.
- Zero trust architecture: Uses a zero trust approach to secure company data, limiting access based on validation of devices and users.
- Visual separation via Blue Border: Visual cue that distinguishes work vs. personal sessions for users.
- Supports turnkey compliance: Using Venn helps companies maintain compliance on unmanaged Macs with a range of regulatory mandates, including HIPAA, PCI, SOC, SEC, FINRA and more.
- Granular, customizable restrictions: IT teams can define restrictions for copy/paste, download, upload, screenshots, watermarks, and DLP per user.
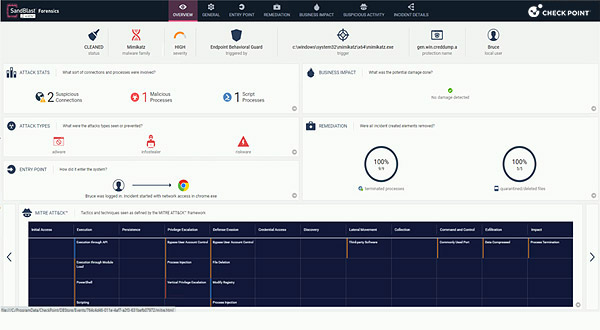
2. Check Point Harmony SASE

Check Point Harmony SASE is a unified Secure Access Service Edge (SASE) solution that integrates network security, zero trust access, and optimized connectivity into a cloud-native platform. It helps simplify secure access for distributed users while improving manageability, combining threat prevention, private access, SaaS protection, and SD-WAN optimization.
Key features include:
- Hybrid SASE architecture: Combines cloud-based network security with high-performance zero trust access to deliver a seamless user experience.
- Full-mesh connectivity: Enables secure any-to-any connections (user to resource, data center to cloud, or cloud to cloud) for global operations.
- Zero trust private access: Enforces identity-centric access controls and granular policies for users, third parties, and branch offices.
- Threat prevention: Achieves a 99% block rate against modern cyber threats, backed by Check Point’s ThreatCloud AI technology.
- SaaS security: Provides visibility into SaaS applications, detects misconfigurations, and uses AI to prevent unauthorized access.
Source: Check Point
3. Palo Alto Prisma Access

Palo Alto Networks Prisma Access is a cloud-delivered Secure Access Service Edge (SASE) solution that protects users, applications, data, and devices. Built on the Precision AI® engine, Prisma Access delivers inline threat prevention, zero trust access, and connectivity across environments. It combines the capabilities of ZTNA, CASB, SWG, and FWaaS.
Key features include:
- Zero trust network access (ZTNA): Enables least-privileged, identity-based access to all applications, removing implicit trust and eliminating the need for traditional VPNs.
- Secure web gateway (SWG): Protects users from advanced web threats in real time using Precision AI for dynamic threat detection and prevention.
- Cloud access security broker (CASB): Provides deep visibility and control over SaaS applications through inline and API-based policies, preventing data exposure and misconfigurations.
- Firewall as a service (FWaaS): Extends next-generation firewall capabilities to the cloud, providing application control, intrusion prevention, and consistent security policies across locations.
- Remote browser isolation (RBI): Creates a secure browsing environment that isolates potential malware and prevents threats from reaching endpoints.
Source: Palo Alto Networks
4. Zscaler Private Access

Zscaler Private Access (ZPA) is a cloud-delivered ZTNA solution that enables fast and secure access to private applications for users without the need for traditional VPNs. Built on the Zscaler Zero Trust Exchange™, ZPA brokers direct, one-to-one user-to-application connections, ensuring apps remain invisible to the public internet and users never gain full network access.
Key features include:
- Zero trust architecture: Enforces identity-based, least-privileged access by connecting users directly to authorized applications, not the network, eliminating lateral movement.
- Application segmentation: Automatically discovers and categorizes applications, using AI-driven recommendations to simplify policy creation and reduce exposure risks.
- Workload-to-workload protection: Secures communications between workloads across hybrid and multicloud environments, including AWS, Azure, and private data centers.
- Privileged remote access: Provides clientless access to sensitive systems such as RDP, SSH, and VNC for employees, contractors, and third-party vendors.
- Browser-based access: Enables secure, infrastructure-agnostic user-to-app connectivity through browser-based access, minimizing client footprint.
Source: Zscaler
5. Cloudflare Connectivity Cloud

Cloudflare’s Connectivity Cloud is a unified, cloud-native Secure Access Service Edge (SASE) and Security Service Edge (SSE) platform that connects and protects users, applications, and AI systems through a single, globally distributed network. Designed to replace fragmented legacy solutions, it delivers zero trust security, scalable networking, and high-performance access.
Key features include:
- Unified SASE architecture: Integrates networking and security services, including zero trust access, CASB, SWG, and DLP, within a globally managed platform.
- Zero trust access control: Replaces VPNs by connecting users directly to internal applications through Cloudflare Access, enforcing least-privilege policies across all devices and locations.
- Secure third-party and privileged access: Provides fast, policy-driven access for contractors, partners, and developers without requiring complex VPN or credential management.
- Web and email security: Protects users from phishing, malware, and multi-channel threats using Cloudflare Gateway, Email Security, and Browser Isolation technologies.
- Shadow IT and SaaS visibility: Detects and manages usage of unauthorized SaaS and AI tools with Cloudflare CASB and DLP for better governance and data protection.
Source: Cloudflare
Related content: Read our guide to Citrix alternatives
Conclusion
Organizations navigating hybrid and remote work environments increasingly require secure, scalable, and application-aware access solutions that go beyond the broad access granted by traditional VPNs. Modern alternatives like zero trust network access (ZTNA) and remote work platforms deliver finer control, better security posture, and improved user experience by minimizing attack surfaces and enabling direct, policy-based application access.
As threats evolve and network perimeters disappear, shifting from legacy VPN models to purpose-built secure access architectures is critical for maintaining operational continuity, compliance, and user productivity.