Best Zero Trust Solutions: Top 12 Options in 2026

What Are Zero Trust Solutions?
Zero trust solutions are security architectures that assume no user, device, or network should be trusted by default, regardless of whether they originate from inside or outside the organizational perimeter. Traditional security models relied on establishing a trusted internal network and focusing most defenses on stopping threats at the perimeter.
Zero trust, however, demands all access requests be verified and authorized continually, emphasizing that threats can come from both outside and inside the network. This paradigm shift addresses the reality of modern attacks, where perimeter defenses are often bypassed, and lateral movement inside networks is a significant risk.
In practice, zero trust involves granular controls on identity, access, and data flow, applying principles such as least privilege and continuous validation. With cloud adoption, remote work, and increased use of mobile devices, traditional boundaries are less relevant, making zero trust essential for risk mitigation.
Implement Zero Trust on Unmanaged Laptops
Discover how to implement zero trust on unmanaged laptops – without VDI or managing the entire device.

In this article:
Key Features of Zero Trust Solutions
Continuous Verification of Identities and Devices
Continuous verification lies at the heart of zero trust, requiring systems to authenticate users and devices at every access attempt, not just at initial login. This means that even after initial authentication, users must prove their identity and the integrity of their device each time they try to access resources. By checking credentials, device health, and access context, organizations limit the chances of compromised accounts or devices moving laterally within the network.
Implementing continuous verification requires integrating identity providers, endpoint security, and monitoring systems to provide real-time decision-making. Automated workflows check for suspicious activities, out-of-date security patches, or non-compliant device configurations, prompting re-authentication or access denial as needed.
Least Privilege Access Enforcement
Enforcing least privilege means users and devices receive only the access necessary for their roles or functions, nothing more. By limiting each entity’s permissions, even if an attacker compromises an account, their access to critical systems and data is minimized. Zero trust solutions implement this through granular access policies, segmenting resources and continuously evaluating whether access still aligns with business needs.
Regular review and adjustment of permissions are vital to least privilege enforcement. Zero trust solutions offer automated policy management, which enables organizations to adapt quickly to changes in user responsibilities or business processes. This reduces the attack surface and curbs the impact of insider threats or credential misuse.
Context-Aware Risk Assessment
Zero trust frameworks incorporate context-aware risk assessment, analyzing a broad range of variables before permitting access. This goes beyond standard identity checks, considering aspects like device health, user location, time of request, and the sensitivity of sought resources. By dynamically evaluating risk, systems can prompt for additional validation or restrict access when anomalies are detected.
Sophisticated zero trust solutions leverage machine learning and analytics to improve risk assessments. They identify behavioral patterns, flag unusual activity, and respond adaptively to potential dangers, such as access attempts from unfamiliar locations or at odd hours. This level of contextual analysis helps organizations make nuanced access decisions.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) requires users to provide at least two forms of evidence to verify their identity, significantly reducing the likelihood of unauthorized access due to compromised credentials. In a zero trust architecture, MFA acts as a fundamental defense, often required whenever users attempt to access sensitive applications or resources.
Typical factors include something users know (password), something they have (token or device), and something they are (biometric data). Zero trust solutions differentiate themselves by deploying adaptive MFA that responds to contextual risk indicators. For example, access attempts from unknown devices or networks may trigger stricter MFA challenges.
Zero Trust Network Access (ZTNA) and Microsegmentation
Zero trust network access (ZTNA) replaces legacy VPNs and perimeter-based controls with granular policies that grant access to specific resources, not entire networks. This means users or devices only see and interact with the applications they are authorized for, drastically limiting lateral movement if credentials are compromised. ZTNA typically authenticates every session and incorporates identity, device health, and context before granting resource access.
Microsegmentation further improves security by dividing networks into small, isolated segments. Each segment enforces its own access controls, making it harder for attackers to pivot within the infrastructure.
Encrypted, Least-Exposed Connections
Zero trust solutions mandate end-to-end encryption for all connections, both at rest and in transit. This ensures that sensitive data remains protected from eavesdropping or interception, even on unsecured networks. Encryption standards such as TLS and IPsec are enforced across all channels, with regular updates to protocols and keys to address evolving threats.
Least-exposed connections also limit network exposure, so services are not broadly visible or accessible to unauthorized entities. Techniques like just-in-time access and one-time, ephemeral connectivity further restrict potential attack vectors. Applications and workloads are not reachable by default and only become accessible after strict validation.
Endpoint and Device Trust Enforcement
Device trust enforcement involves assessing and validating the security posture of endpoints before granting them resource access. Zero trust solutions verify device characteristics, configurations, patch status, and the presence of required security agents. Devices that fail to meet baseline security requirements are automatically quarantined or blocked from network access, mitigating the risk from compromised or outdated hardware.
Continuous monitoring of device status helps organizations detect anomalies and rapidly isolate suspicious endpoints. Automated remediation workflows can prompt users to update software, install patches, or enable security controls before they regain access.
Notable Zero Trust Solutions
BYOD and Device Enforcement
1. Venn

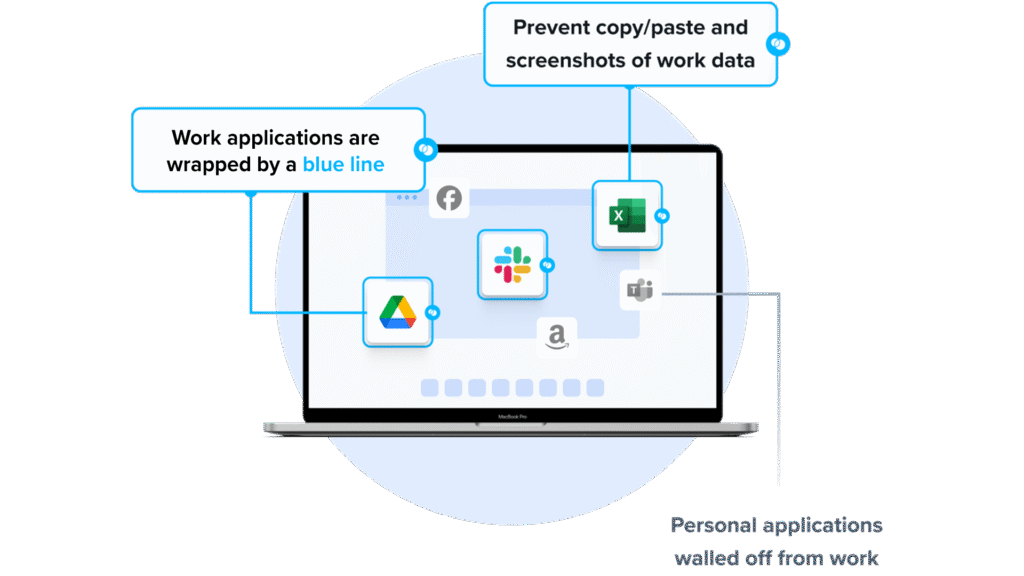
Venn brings zero trust security to remote and BYOD environments by containing company apps and data inside a secure, isolated workspace on any PC or Mac. Instead of relying on traditional VPNs, VDI, or MDM, Venn enforces Zero Trust principles directly on the endpoint — ensuring that every user, device, and action is verified, and company resources are never left exposed.
Similar to an MDM solution but for laptops – work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the Enclave – visually indicated by Venn’s Blue Border™ – protecting and isolating business activity while ensuring end-user privacy.
Zero Trust in Action with Venn:
- Seamless MFA integration – Works with Okta, Azure, and Duo for strong identity verification
- Encrypted workspace – Ensures all corporate apps and data are secured in transit and at rest
- Context-aware access controls – Policies adapt by user, device health, and environment
- Unified Zero Trust platform – Endpoint security, remote access, and Zero Trust enforcement in one
- Faster, scalable alternative – Delivers superior performance compared to legacy VDI
You can schedule a demo of Blue Border here
2. Citrix Device Posture

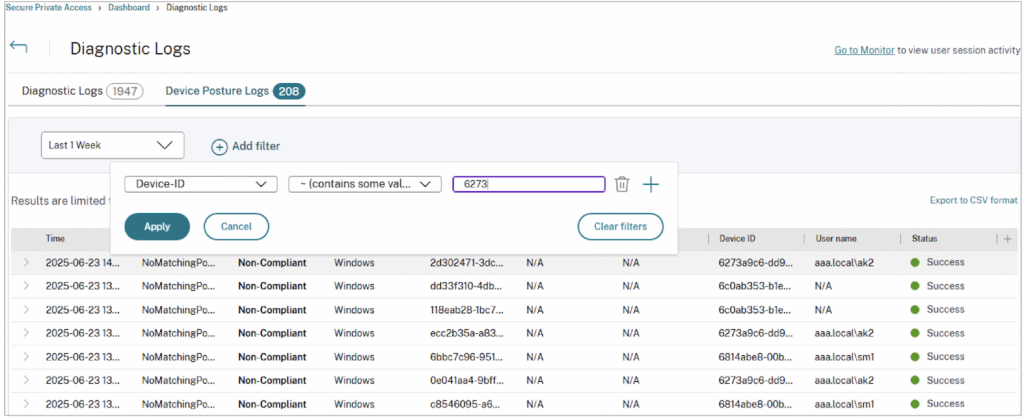
Citrix Device Posture is a cloud-based service used to evaluate endpoint compliance before granting access to Citrix DaaS and Citrix Secure Private Access resources. It supports zero trust access by validating device posture during pre-authentication and classifying devices as compliant, non-compliant, or denied login.
Key features include:
- Pre-authentication posture checks: Evaluates device posture before login, ensuring access decisions are made prior to session establishment
- Policy-based device classification: Classifies devices as compliant, non-compliant, or denied login based on administrator-defined rules
- Broad posture scan support: Checks attributes such as OS version, files, processes, antivirus status, certificates, network location, and windows update status
- Third-party integrations: Integrates with tools like Microsoft Intune and CrowdStrike to incorporate external compliance signals
- Cross-platform coverage: Supports windows, macOS, iOS, and linux, with unsupported platforms marked non-compliant by default
- EPA client enforcement: Uses a lightweight endpoint posture assessment (EPA) client that runs scans without requiring local admin rights in most cases
Source: Citrix
3. Workspace ONE

Workspace ONE provides unified endpoint management and zero trust access across device types, making it useful for BYOD security. It helps enforce device compliance before access, supports remote provisioning, and enables role-based access control.
Key features include:
- Device compliance enforcement: Evaluates posture and compliance before granting access, including OS version and security settings
- Zero trust security model: Applies access policies based on identity, behavior, and device health
- Unified device management: Supports all major operating systems across BYOD, corporate, and specialty devices
- Remote onboarding: Enables zero-touch provisioning for employees across locations and device types
- Role-based access control: Customizes access levels based on user roles and group membership
- IT automation: Simplifies onboarding, updates, and compliance workflows with low-code orchestration tools
Source: Omnissa
Zero Trust and ZTNA Solutions
4. Zscaler Zero Trust Exchange

Zscaler Zero Trust Exchange is a cloud-native platform that replaces traditional network security architectures with a scalable, AI-enhanced zero trust model. Built around least-privileged access and proxy-based traffic inspection, it brokers secure, direct connections between users and applications without placing users on the network.
Key features include:
- Cloud-native proxy architecture: Establishes one-to-one connections between users and apps, enforcing least-privilege access without exposing the network.
- TLS/SSL traffic inspection: Inspects encrypted traffic at scale, identifying and blocking threats in without degrading performance.
- Application-invisible design: Keeps internal applications hidden from the public internet, minimizing the attack surface.
- Lateral movement prevention: Eliminates the need for network access, preventing attackers from moving laterally across systems once inside.
- Integrated data loss prevention: Automatically detects and protects sensitive data in motion, at rest, and in use.
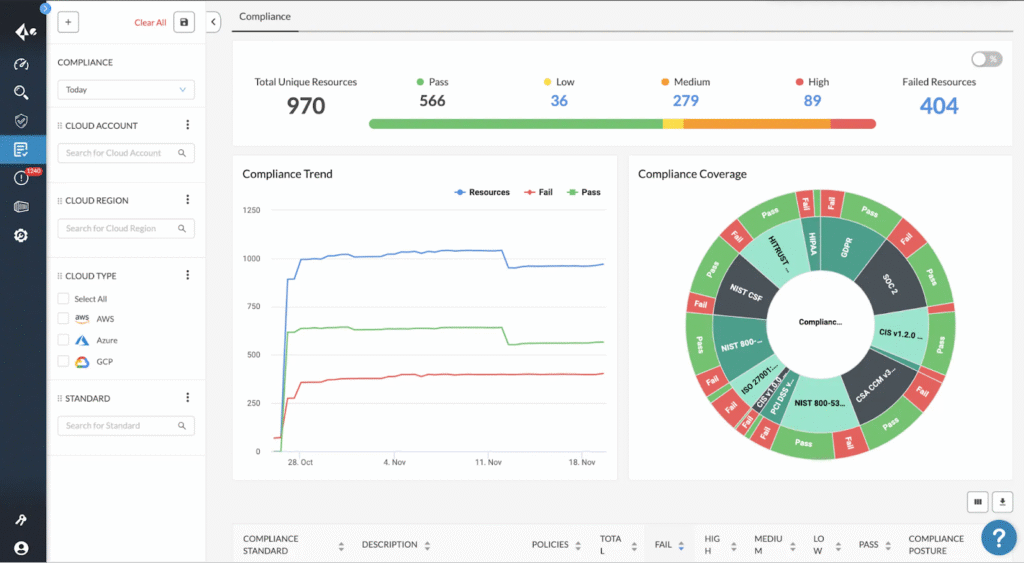
5. Palo Alto Networks Prisma Access

Prisma Access from Palo Alto Networks is a cloud-delivered platform that secures users, applications, devices, and data regardless of location, through a zero trust architecture. It replaces legacy VPNs and on-premises appliances with a scalable solution that delivers secure, least-privileged access to resources without relying on implicit trust.
Key features include:
- Zero trust network access (ZTNA): Enforces identity-based, least-privileged access to applications, removing the risks of implicit trust and reducing the attack surface without the complexity of traditional VPNs.
- Cloud access security broker (CASB): Provides visibility and control over SaaS applications and data, with contextual, inline, and API-based policies to prevent data leakage.
- Secure web gateway (SWG): Inspects and filters web traffic in real time to block sophisticated web-based threats using AI-driven analysis.
- Remote browser isolation (RBI): Isolates web sessions in a secure environment, ensuring malware and web exploits never reach the endpoint.
- Firewall as a service (FWaaS): Delivers cloud-native network security, including threat prevention, application control, and zero trust enforcement, across the network.
Source: Prisma Access
6. NordLayer Zero Trust

NordLayer delivers a modular and scalable zero trust solution built for distributed, cloud-based workplaces. Designed to secure both on-site and remote users, it verifies every connection before granting access, whether it’s from a user, device, or application.
Key features include:
- Identity and device verification: Requires all users and devices to be authenticated and validated before access is granted, ensuring only authorized entities connect to corporate resources.
- Microsegmentation and access control: Limits access to apps or systems through policy enforcement, blocking lateral movement inside the network.
- Encrypted tunnels for all connections: Uses secure VPN tunnels to encrypt traffic between endpoints and internal resources, protecting data in transit across remote and hybrid work environments.
- Rapid deployment and centralized management: Enables fast rollout across the organization with a control panel for managing teams, access rules, and security features.
- Endpoint and web protection: Enhances endpoint security by detecting rooted or non-compliant devices and blocking harmful content before it reaches users.
7. ThreatLocker

ThreatLocker provides a unified zero trust platform focused on prevention, access control, and containment of cyber threats. It uses a “default deny” approach to restrict what applications, users, and devices can do inside an environment. It includes modules such as allowlisting, application ringfencing, network access control, and elevation management.
Key features include:
- Application allowlisting: Blocks all unauthorized executables by default and allows only approved applications, scripts, and libraries to run, preventing both known and unknown malware from executing.
- Ringfencing™: Controls how permitted applications interact with other software and system resources, stopping exploits and fileless malware by restricting access to networks, registries, and internal tools like PowerShell.
- Network control: Replaces traditional VPNs with cloud-managed, dynamic firewall policies at the endpoint level, enabling precise control over inbound network traffic based on IPs or keywords.
- Elevation control: Removes local admin rights while allowing users to run apps with elevated privileges, preventing privilege abuse while maintaining workflow continuity.
- Storage control: Offers control over USB devices and network shares, allowing IT to monitor, restrict, and audit access to files based on user, device, file type, or application.
Source: ThreatLocker
8. Fortinet Zero Trust Access

Fortinet Zero Trust Access (ZTA) delivers identity- and device-aware access controls across applications, endpoints, and networks, enforcing the principle of least privilege in on-premises and remote environments.
Key features include:
- Continuous verification: Authenticates and authorizes users and devices before granting access, regardless of network location, reducing implicit trust and unauthorized lateral movement.
- Zero trust network access (ZTNA): Replaces traditional VPNs with per-session access to individual applications, applying zero trust policies consistently for on-network and off-network users.
- Endpoint security with FortiClient: Integrates endpoint visibility, control, and threat protection, ensuring devices meet security standards before access is allowed.
- Identity and access management: Uses FortiAuthenticator for centralized user verification, SSO, certificate-based authentication, and guest access management, with MFA support via FortiToken.
- IoT and device control: Identifies and monitors IoT devices entering the network, applying controls to limit risk from unmanaged or unknown endpoints.
Source: Fortinet Zero Trust
Identity and Access Management Focused Solutions
9. Microsoft Entra ID

Microsoft Entra ID is a component of Microsoft’s zero trust architecture, providing cloud-based identity and access management to secure users, devices, and applications. It enables organizations to enforce identity verification, conditional access, and least privilege policies across hybrid and cloud environments.
Key features include:
- Identity and access management: Provides centralized control over user and device authentication, supporting single sign-on and secure access to cloud and on-premises resources.
- Conditional access policies: Enables risk-based access control based on user behavior, device compliance, and real-time context.
- Integrated MFA and risk detection: Uses Microsoft Entra ID Protection to detect identity threats and enforce multifactor authentication when risk thresholds are exceeded.
- Access governance automation: Offers Microsoft Entra ID Governance for automating access reviews, entitlement management, and lifecycle provisioning.
- Secure external access: Supports Microsoft Entra External ID for safely managing partner and customer access to business apps and services.
Source: Microsoft Entra ID
10. Okta Zero Trust

Okta Zero Trust is an identity-focused approach to security that places identity at the core of access decisions across users, devices, and applications. Rather than relying on network location or static credentials, it enforces context-aware access policies based on signals such as user behavior, device posture, and risk levels.
Key features include:
- Identity as the foundation: Uses identity as the primary control plane for zero trust, enabling adaptive access decisions that go beyond network perimeters.
- Context-aware access management: Evaluates login context such as device security, location, time, and behavior patterns to determine risk and apply appropriate policies.
- Seamless integration: Connects with a range of applications, infrastructure, and security tools to deliver consistent zero trust enforcement across the IT environment.
- Access control: Grants least-privilege access using role-based policies and continuous authentication, ensuring users only access what they need.
- Risk-based authentication: Applies dynamic authentication requirements using threat intelligence and behavior analytics to minimize friction for low-risk access and challenge high-risk events.
Source: Okta Zero Trust
11. JumpCloud

JumpCloud delivers a zero trust security model through an open cloud directory platform that centralizes identity, device, and access management. It enables organizations to verify user identity at every access point by enforcing dynamic access policies, least privilege controls, and continuous authentication.
Key features include:
- Unified cloud directory: Acts as the central identity and access platform, connecting users to systems, applications, and networks securely across major operating systems.
- Dynamic conditional access: Enforces access decisions based on identity, group membership, device health, and geolocation, aligning with zero trust principles.
- Least privilege enforcement: Limits user permissions to only the necessary resources, reducing exposure from compromised accounts or insider threats.
- Multi-factor authentication (MFA): Integrates MFA into access points, reducing risk from credential-based attacks.
- Single sign-on (SSO): Provides secure access to SAML and OIDC-based web applications through one centralized login.
Source: JumpCloud
12. Cisco Duo

Cisco Duo is a security-focused identity and access management (IAM) platform that enforces zero trust by verifying user identities, assessing device health, and blocking unauthorized access before it happens. It integrates multi-factor authentication (MFA), secure single sign-on (SSO), and real-time risk detection into a unified solution.
Key features include:
- Phishing-resistant MFA: Enforces strong authentication using methods like FIDO2/WebAuthn, reducing the risk of credential theft and eliminating reliance on easily phished methods like SMS or OTP.
- Single sign-on (SSO): Offers seamless access to multiple cloud and on-premises applications with a single login, reducing password fatigue while maintaining strong security.
- Duo directory & identity integration: Functions as a full IAM directory or integrates with existing identity providers to extend zero trust controls across the enterprise.
- Identity intelligence: Monitors login patterns and user behavior to detect risks in real time, helping security teams act proactively before threats escalate.
- Risk-based access policies: Evaluates contextual signals such as login location, device trust, and time of access to enforce adaptive authentication and block risky access attempts.
Source: CISCO Duo
Considerations for Choosing Zero Trust Solutions
Selecting a zero trust solution involves evaluating how well it aligns with your organization’s existing infrastructure, security goals, and operational needs. Not all solutions are created equal; some focus heavily on identity, while others specialize in network controls, endpoint visibility, or data protection. Below are key considerations to guide your selection:
- Integration with existing infrastructure: Choose a solution that integrates seamlessly with your current identity providers, cloud environments, endpoint management systems, and security tools. Poor integration can increase complexity and reduce the effectiveness of zero trust policies.
- Scalability and deployment flexibility: Evaluate whether the solution can scale with your organization’s growth and support hybrid or multi-cloud environments. Consider deployment models (cloud-native, on-premises, or hybrid) that best fit your operational model.
- Granular policy control: Ensure the solution allows fine-tuned control over access policies based on user roles, device state, location, and behavior. Look for support for just-in-time access, adaptive authentication, and detailed segmentation.
- Continuous monitoring and visibility: Effective zero trust requires continuous assessment of user and device behavior. Look for solutions that provide real-time monitoring, anomaly detection, and integration with SIEM or XDR platforms for threat response.
- Identity and access management capabilities: Strong identity capabilities, such as multi-factor authentication, single sign-on, and identity governance, are foundational. Prioritize vendors with mature IAM offerings that enforce identity verification at every access point.
- Support for device posture assessment: Ensure the platform can assess device health, security compliance, and trust levels before granting access. This is essential for environments with BYOD, remote users, or unmanaged devices.
- Data protection and compliance: Consider how the solution handles data encryption, access logging, and governance controls. Support for regulatory compliance (e.g., HIPAA, GDPR, SOC 2) may be critical, depending on your industry.
- User experience and admin usability: Security shouldn’t come at the expense of usability. Select solutions that balance strong protection with a smooth user experience and offer intuitive interfaces for IT and security teams.
- Vendor support and ecosystem: Evaluate the vendor’s support model, documentation, and community. A strong partner ecosystem and third-party integrations can enhance the solution’s value and adaptability.
By aligning these considerations with your organization’s security maturity and risk profile, you can select a zero trust solution that delivers long-term resilience without unnecessary complexity.
Related content: Read our guide to zero trust security